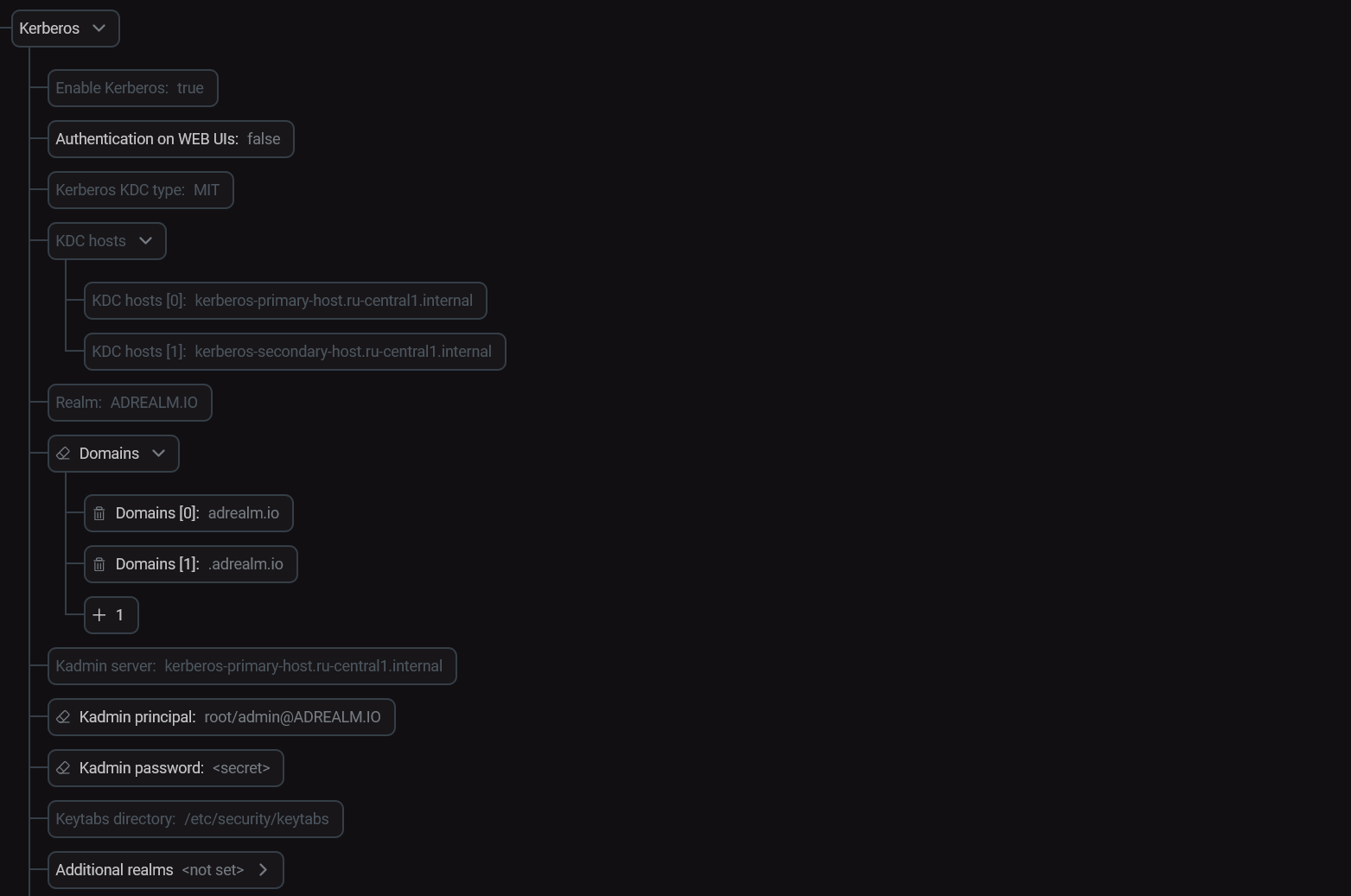
Kerberos server settings
Main Kerberos server setup
|
TIP
The instruction described in this section can be used to interchange the main and secondary KDC, if needed.
|
-
To install the Kerberos server package to the server, run the command:
$ sudo yum install -y krb5-server pam_krb5 krb5-workstation xinetd -
To change the configuration, edit the /etc/krb5.conf file:
krb5.conf# Configuration snippets may be placed in this directory as well includedir /etc/krb5.conf.d/ [logging] default = FILE:/var/log/krb5libs.log kdc = FILE:/var/log/krb5kdc.log admin_server = FILE:/var/log/kadmind.log [libdefaults] dns_lookup_realm = false ticket_lifetime = 24h renew_lifetime = 7d forwardable = true rdns = false pkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crt default_realm = ADREALM.IO default_ccache_name = KEYRING:persistent:%{uid} [realms] ADREALM.IO = { kdc = kerberos-primary-host.ru-central1.internal #primary KDC host kdc = kerberos-secondary-host.ru-central1.internal #secondary KDC host admin_server = kerberos-primary-host.ru-central1.internal } [domain_realm] .adrealm.io = ADREALM.IO adrealm.io = ADREALM.IO -
You also need to edit the /var/kerberos/krb5kdc/kdc.conf file:
kdc.conf[kdcdefaults] kdc_ports = 88 kdc_tcp_ports = 88 [realms] ADREALM.IO = { #master_key_type = aes256-cts acl_file = /var/kerberos/krb5kdc/kadm5.acl dict_file = /usr/share/dict/words admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal } -
The last file that should be edited before the Kerberos database setup is /var/keberos/krb5kdc/kadm5.acl:
kadm5.acl*/admin@ADREALM.IO *
-
Now you have to configure the Kerberos database. For this, use the
kdb5_utilutility:$ sudo kdb5_util create -s -r ADREALM.IO -
Memorize the Master KDC password and run the services:
$ sudo systemctl enable kadmin $ sudo systemctl enable krb5kdc $ sudo systemctl start kadmin $ sudo systemctl start krb5kdc -
Now you have to create the new principals. You need to create host principals for every KDC instance. In order to do this, use the Kerberos administrator console:
$ sudo kadmin.local $ addprinc root/admin $ addprinc -randkey host/kerberos-primary-host.ru-central1.internal $ addprinc -randkey host/kerberos-secondary-host.ru-central1.internal $ ktadd host/kerberos-primary-host.ru-central1.internal -
Generate the keytab of the secondary Kerberos server on the main Kerberos server:
$ ktadd -k /tmp/kerberos-secondary-host.keytab host/kerberos-secondary-host.ru-central1.internal
Secondary Kerberos server setup for high availability
-
Install the necessary packages to the second server:
$ sudo yum install -y krb5-server krb5-workstation xinetd -
To enable password authentication, uncomment the following string in the /etc/ssh/sshd_config file:
PasswordAuthentication yes
-
Restart the service:
$ sudo systemctl restart sshd -
Copy the secondary server keytab file (the one obtained at the previous step) to the secondary KDC host:
$ sudo scp /tmp/kerberos-secondary-host.keytab <user>@<ip address>:/tmp/ -
While at secondary host, move the keytab file to the /etc/ directory and rename it:
$ sudo cp /tmp/kerberos-secondary-host.keytab /etc/krb5.keytab -
The principal database is transferred from the main KDC to KDC replicas via the kpropd daemon. You have to specify the principals that are permitted to receive the updates of secondary Kerberos server dumps. Those updates contain the new database. You have to create the kpropd.acl file in the KDC state-monitoring directory. The kpropd.acl file will contain the principal host names for every KDC:
$ sudo vi /var/kerberos/krb5kdc/kpropd.acl -
Add the following lines to kpropd.acl:
host/kerberos-primary-host.ru-central1.internal@ADREALM.IO host/kerberos-secondary-host.ru-central1.internal@ADREALM.IONOTEIf you expect that the primary and secondary KDC might swap their places, you should specify the host addresses of all KDC servers in the kpropd.acl files on every KDC. Otherwise, you have to specify only the primary host in the kpropd.acl files on KDC replicas. -
You should copy the following files from the primary KDC host to the secondary KDC host:
-
krb5.conf
-
kdc.conf
-
kadm5.acl
-
master key stash file
-
-
Move the files that were copied to the corresponding directories. The files and directories structure should be exactly like it is at the primary KDC.
TIPThe kadm5.acl file is needed to allow the replica to communicate with the primary KDC. -
Run the following commands on the primary server:
$ sudo scp /etc/krb5.conf <user>@<ip address>:/tmp/ $ sudo scp /var/kerberos/krb5kdc/kdc.conf <user>@<ip address>:/tmp/ $ sudo scp /var/kerberos/krb5kdc/kadm5.acl <user>@<ip address>:/tmp/ $ sudo scp /var/kerberos/krb5kdc/.k5.ADREALM.IO <user>@<ip address>:/tmp/ $ sudo scp /var/kerberos/krb5kdc/kpropd.acl <user>@<ip address>:/tmp/ -
Run the following commands on the secondary server:
$ sudo cp /tmp/krb5.conf /etc/ $ sudo cp /tmp/kdc.conf /var/kerberos/krb5kdc/ $ sudo cp /tmp/kadm5.acl /var/kerberos/krb5kdc/ $ sudo cp /tmp/.k5.ADREALM.IO /var/kerberos/krb5kdc/ $ sudo cp /tmp/kpropd.acl /var/kerberos/krb5kdc/ -
Create the /etc/xinetd.d/krb5_prop configuration file:
/etc/xinetd.d/krb5_propservice krb5_prop { socket_type = stream wait = no user = root server = /usr/sbin/kpropd only_from = 0.0.0.0/0 log_on_success = PID HOST EXIT DURATION } -
Add the following line (if it’s missing) to the /etc/services file on every KDC:
krb5_prop 754/tcp # Kerberos replica propagation
-
Run the following command:
$ sudo systemctl restart xinetd -
Before you copy the database, create the database dump file on the primary KDC:
$ sudo kdb5_util dump /var/kerberos/krb5kdc/slavedump -
Copy the database manually to every KDC replica:
$ sudo kprop -f /var/kerberos/krb5kdc/slavedump kerberos-secondary-host.ru-central1.internalThe result should look like this:
Database propagation to kerberos-secondary-host.ru-central.internal: SUCCEEDED
-
Run KDC on the secondary host:
$ sudo systemctl enable krb5kdc $ sudo systemctl start krb5kdc -
Enter the
admin.localconsole and execute thelistprincscommand to view the principals list and make sure that the list is the same as the list on the primary host.
In order to implement the principals database regular synchronization, you have to create a cron job. A script sample is below:
#!/bin/sh
kdclist = "kerberos-primary-host.ru-central1.internal kerberos-secondary-host.ru-central1.internal"
kdb5_util dump /var/kerberos/krb5kdc/slavedump
for kdc in $kdclist
do
kprop -f /var/kerberos/krb5kdc/slavedump $kdc
doneAn example of ADCM settings for the case of several KDC hosts: