

Ranger YARN plugin
Enable YARN plugin
To enable the Ranger YARN plugin, follow the steps below:
-
Go to the Clusters → <ADH_cluster> → Services page.
-
Find YARN and click the
icon in the Actions column. In the drop-down menu, select the Manage Ranger plugin action.
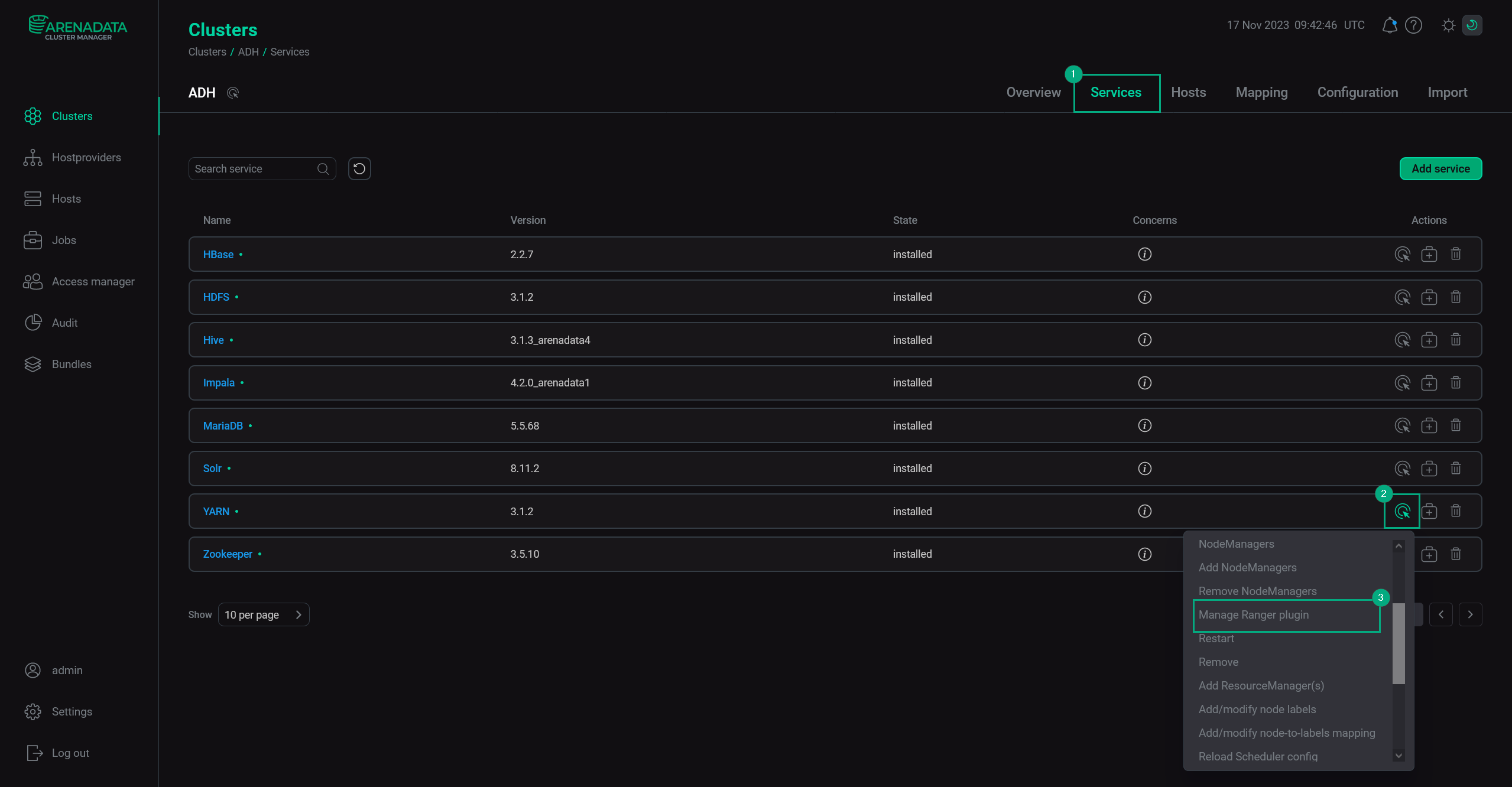 Cluster services
Cluster services -
Select the required state of the Plugin enabled flag. Also, here you can set the name of the Ranger service that will be added. If a service with such name already exists, you can override it by enabling the Override service policies parameter — in that case, the old service will be deleted and policies will be generated for the new service.
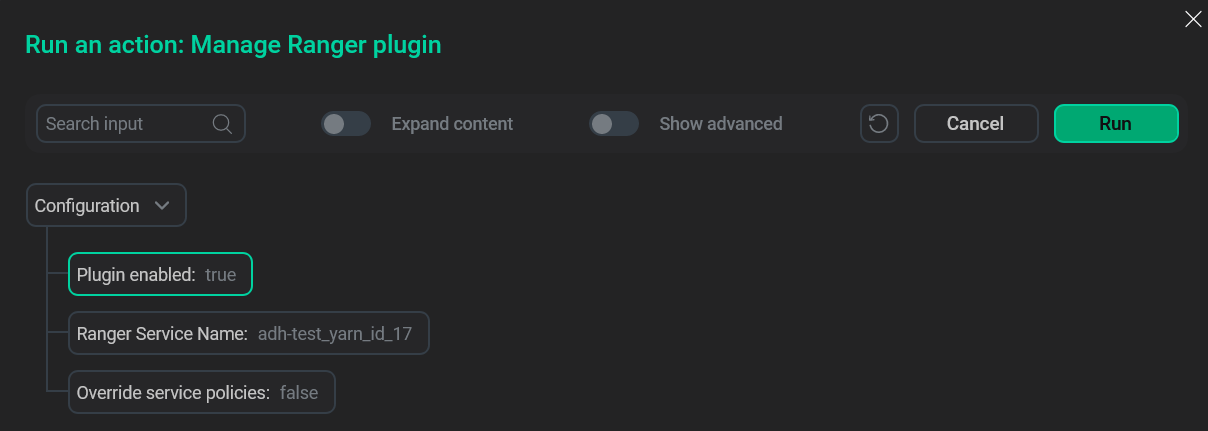 Plugin stateNOTEOn the first plugin enabling, a service with policies will be created (if it doesn’t exist yet) regardless of the Override service policies parameter.
Plugin stateNOTEOn the first plugin enabling, a service with policies will be created (if it doesn’t exist yet) regardless of the Override service policies parameter. -
Click Run and confirm the action in the pop-up window.
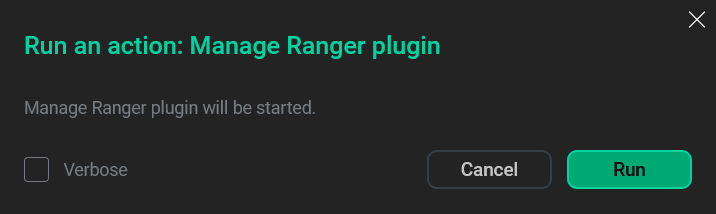 Action confirmation
Action confirmation
Add a new policy in Ranger
To add a new policy to an existing YARN service, you should perform the following actions:
-
On the Service Manager page, click an existing service in the YARN pane.
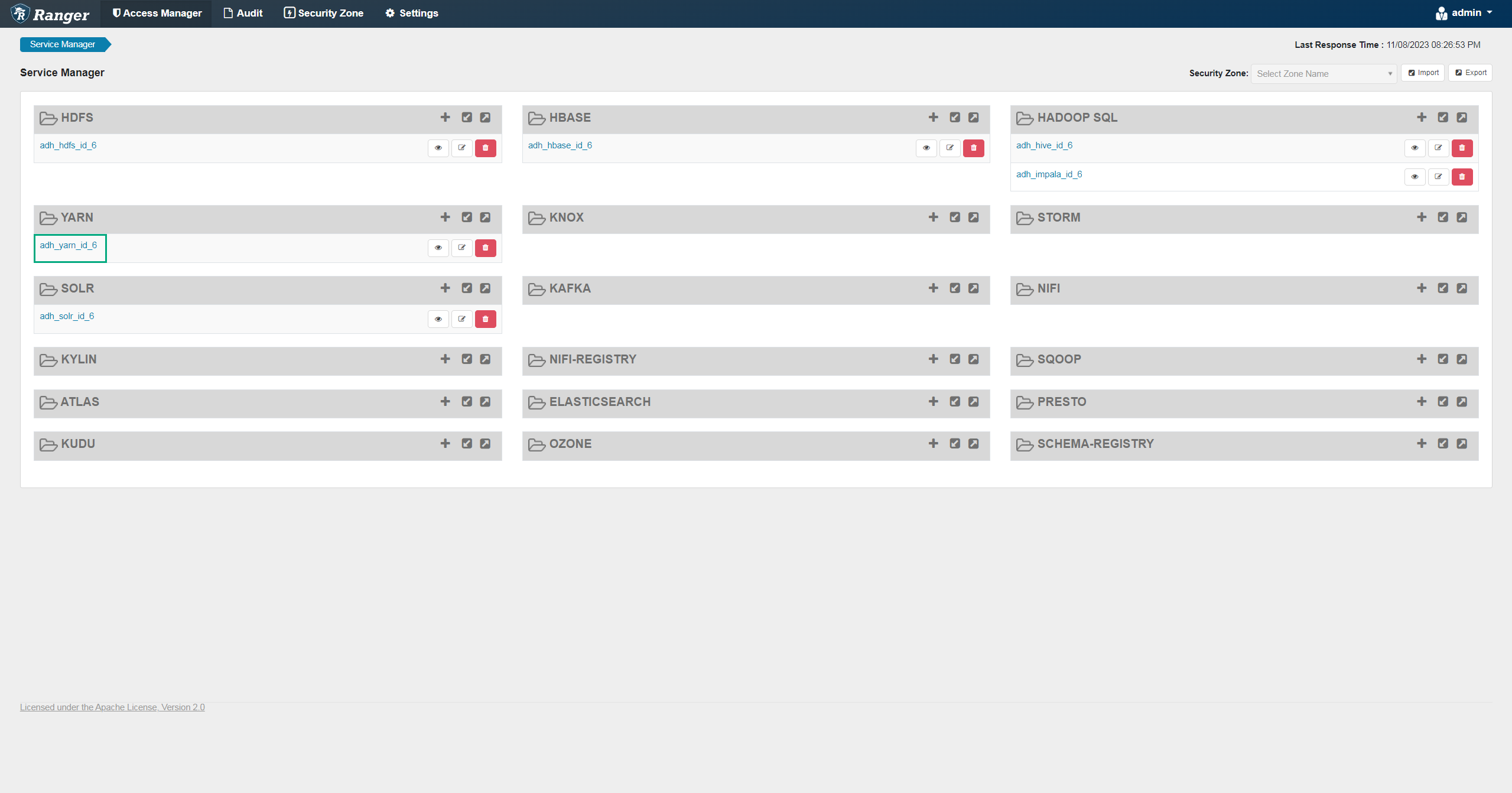 Service Manager
Service Manager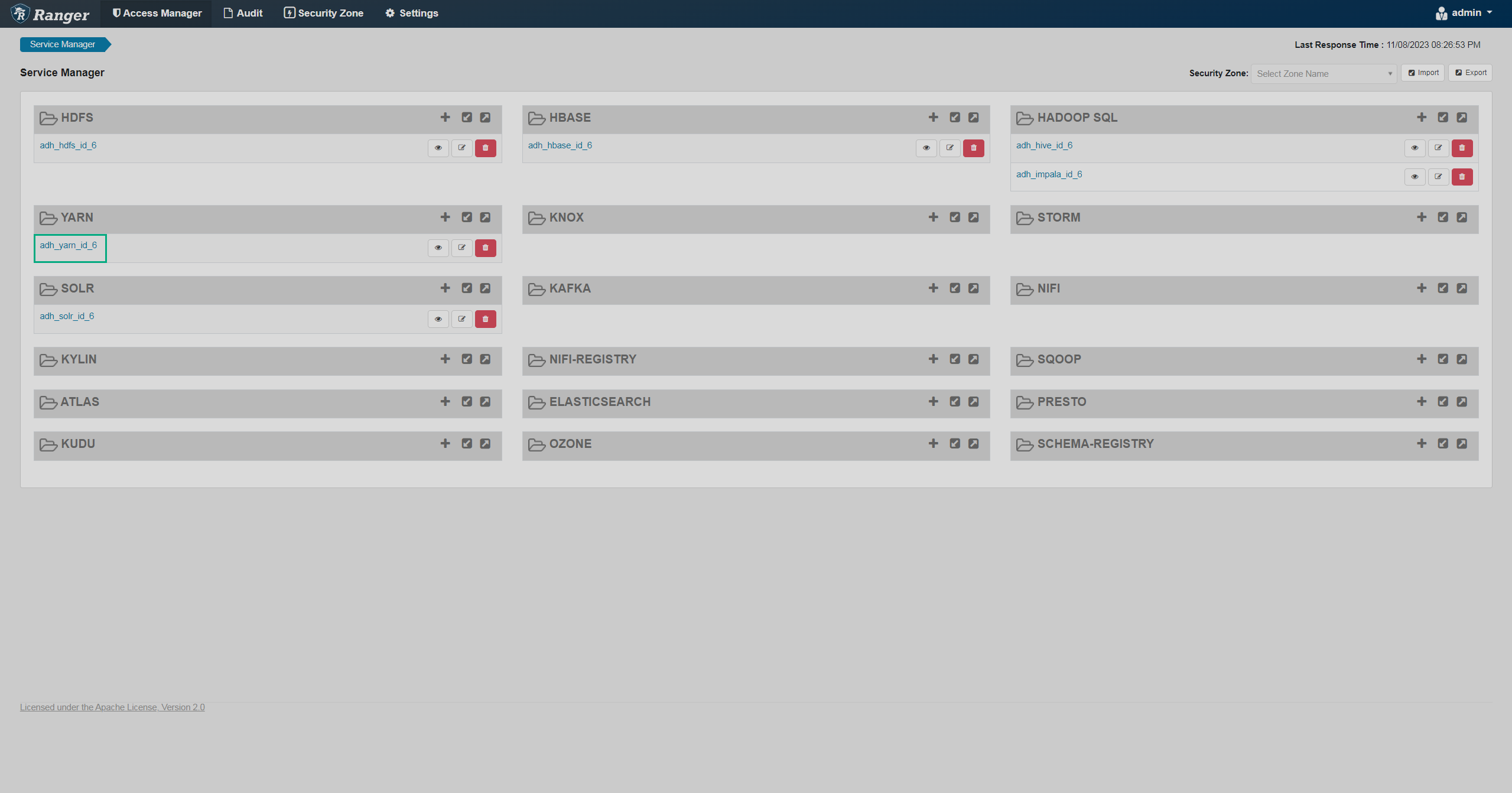 Service Manager
Service Manager -
On the YARN policy page, click Add New Policy.
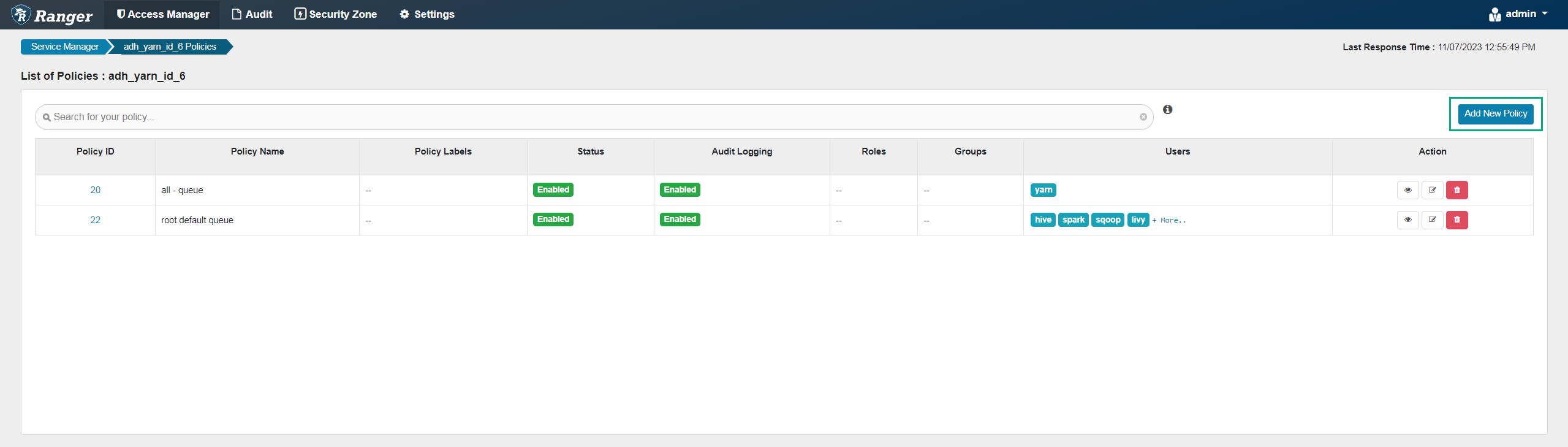 Add new policy
Add new policy Add new policy
Add new policy -
On the opened Create Policy page, fill in the required policy details.
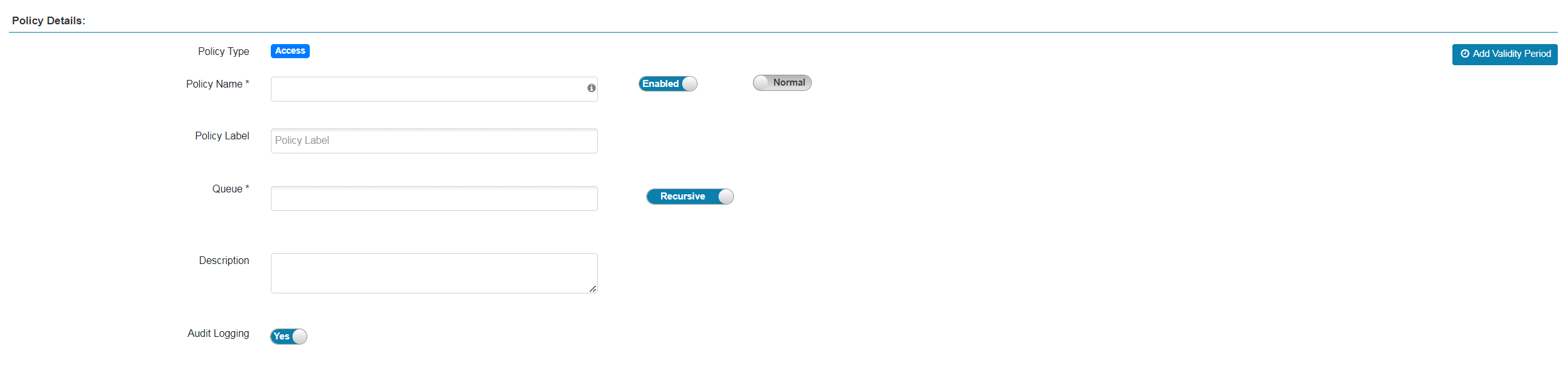 YARN policy details
YARN policy details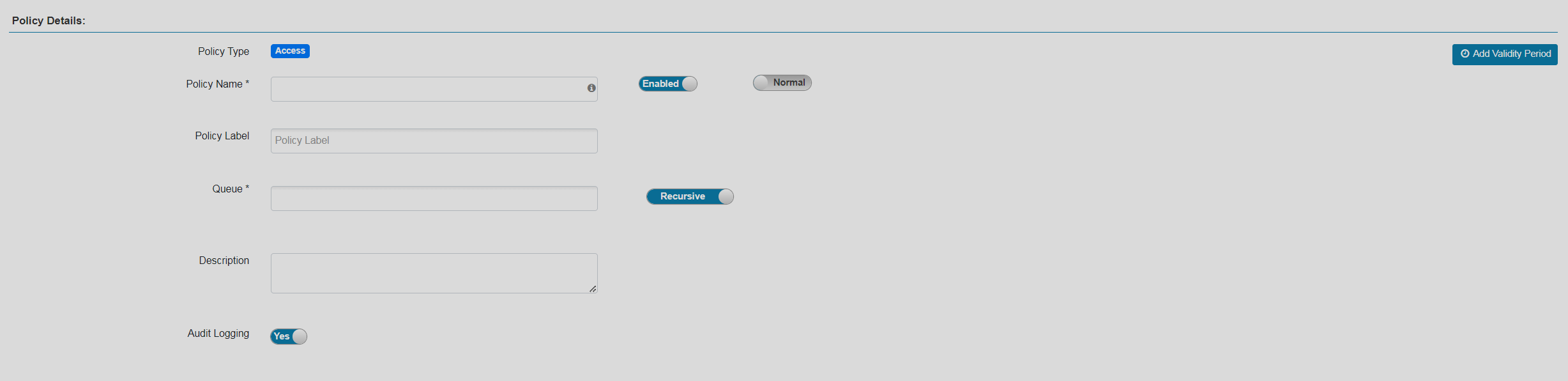 YARN policy details
YARN policy detailsPolicy details parameters Parameter Description Policy Name
The policy name. Must be unique across the system
Enabled
Indicates whether to enable the policy after creation
Normal/Override
Allows you to specify an override policy. When override state is selected, the access permissions of the new policy override the access permissions in existing policies
Policy Label
Allows grouping of sets of policies with one or more labels and searching for policies by label names. You can use search on the Policy listing page and on the Reports page. Also helps to export/import policies. If a user has to export some specific set of policies, then they can search for a policy label and export the specific set of policies
Queue
The fundamental unit of scheduling in YARN
Recursive/Non-recursive
Indicates whether all files and folders within the existing folder should be affected by the policy. Can be used instead of wildcard characters
Description
Describes the purpose of the policy
Audit Logging
Enables audit for the policy
Add Validity Period
Allows you to set the lifetime for the policy
-
Set allow/deny condition parameters. The Allow Conditions section lets you grant access permissions to certain roles/groups/users. It makes sense to use this section if you want to allow acess to a few roles/groups/users and deny it to all others. The Deny Conditions sections in the reverse logic compared to Allow Conditions — it’s useful when you want to deny access to a few roles/groups/users and allow it to everyone else. You can also combine rules from both sections. To add additional conditions, click
 .
Conditions take priority in the order listed in the policy.
The condition at the top of the list is applied first, then the second, then the third, and so on.
.
Conditions take priority in the order listed in the policy.
The condition at the top of the list is applied first, then the second, then the third, and so on.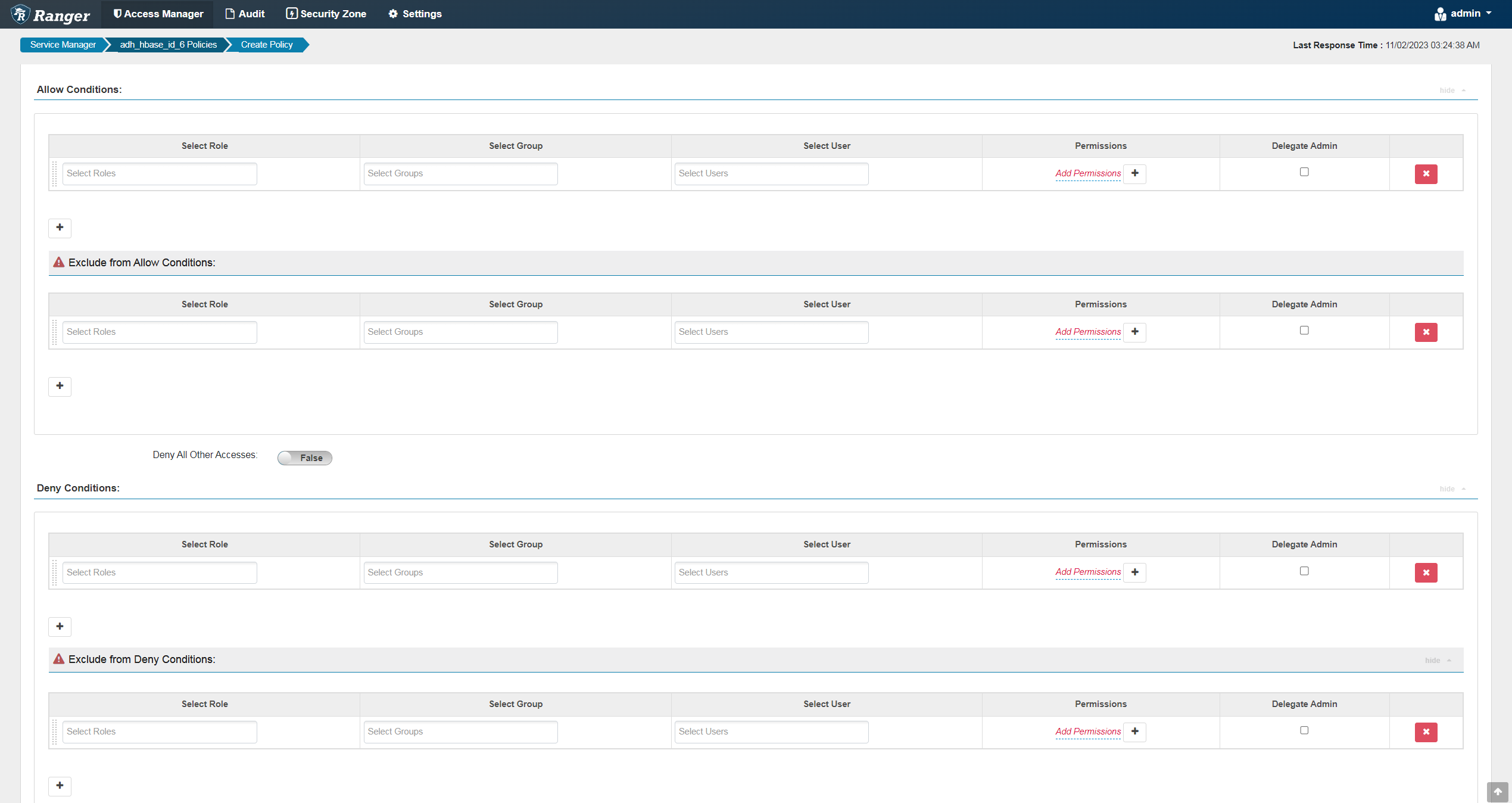 YARN allow conditions parameters
YARN allow conditions parameters YARN allow conditions parametersAllow Conditions parameters
YARN allow conditions parametersAllow Conditions parametersParameter Description Select Role
Specifies the roles to which this policy applies
Select Group
Specifies the groups to which this policy applies. The public group contains all users, so granting access to the public group grants access to all users
Select User
Specifies a user to which this policy applies (outside an already-specified group) or makes the user an Administrator for this policy
Permissions
Allows you to add or edit permissions
Delegate Admin
Grants administrator privileges to the users or groups specified in the policy. Administrators can edit or delete policies and create child policies based on the existing ones
Deny Conditions parametersParameter Description Select Role
Specifies the roles to which this policy does not apply
Select Group
Specifies the groups to which this policy does not apply. The public group contains all users, so denying access to the public group denies access to all users
Select User
Specifies a user to which this policy does not apply (outside an already-specified group) or makes the user an Administrator for this policy
Permissions
Allows you to add or edit permissions
Delegate Admin
Grants administrator privileges to the users or groups specified in the policy. Administrators can edit or delete policies and create child policies based on the existing ones
-
Click Add at the bottom of the page.