

Set TLS version for an ADH cluster
This section shows how to configure an ADH cluster to use a specific TLS version for SSL communication and how to verify the current TLS version that is in use.
As of ADH 2.1.10.b1, the minimum supported TLS version is TLSv1.2 as restricted by Java 8. TLSv1.3 is supported on JDK11+ and JDK8 build 8u261 or later (JRE 1.8.0_261-b12+).
Select TLS version
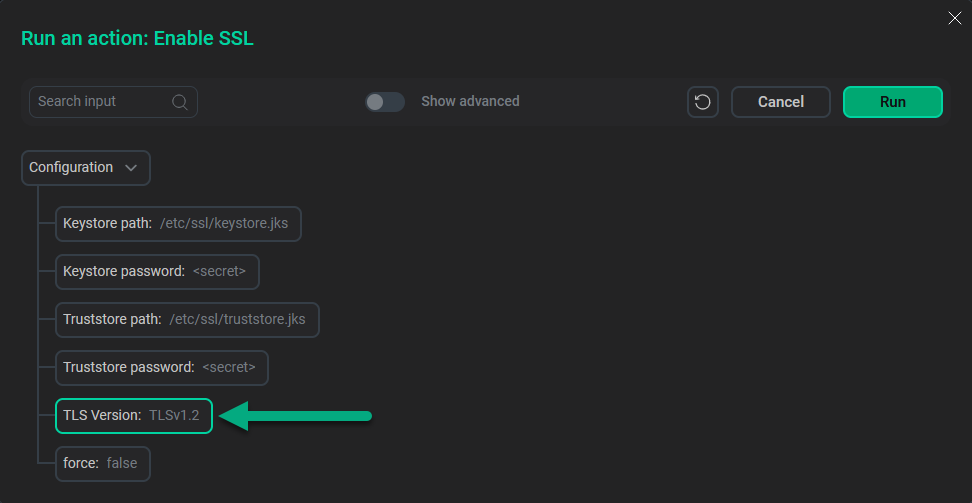
You can specify the desired TLS version for entire ADH cluster using the TLS Version parameter when running the Manage SSL action.
As of 2.1.10.b1, the only supported version is TLSv1.2.
Per-service TLS settings
You can also set a specific TLS version for individual ADH components. The list of configuration files and parameters responsible for the TLS protocol selection is presented below.
| Service | Configuration file | Parameter | Default value | Description |
|---|---|---|---|---|
Hive |
/etc/hive/conf/hive-site.xml |
hive.ssl.protocol.blacklist |
SSLv2Hello,SSLv2,SSLv3,TLSv1,TLSv1.1 |
Disables specified TLS protocols for all Hive Servers |
TezUI |
/etc/nginx/nginx.conf |
server.ssl_protocols |
TLSv1.2 |
A comma-separated list of TLS protocols supported for the SSL transport |
Metastore |
/etc/hive/conf/hive-site.xml |
metastore.ssl.protocol.blacklist |
SSLv2Hello,SSLv2,SSLv3,TLSv1,TLSv1.1 |
Disables specified TLS protocols for Hive Metastore |
HDFS, YARN |
/etc/hadoop/conf/core-site.xml |
hadoop.ssl.enabled.protocols |
TLSv1.2 |
A comma-separated list of TLS protocols used for SSL communication between HDFS DataNodes |
Spark3 |
/etc/spark3/conf/spark-defaults.conf |
spark.ssl.protocol |
TLSv1.2 |
Specifies the TLS protocol to use |
Livy |
/etc/livy-spark3/conf/livy.conf |
livy.server.thrift.ssl.protocol.blacklist |
SSLv2,SSLv3,TLSv1,TLSv1.1 |
Disables specified TLS protocols |
Flink |
/etc/flink/conf/flink-conf.yaml |
security.ssl.protocol |
TLSv1.2 |
Specifies a single TLS version to be used for the SSL transport. Does not support comma-separated values |
ZooKeeper 3.5.5+ |
/etc/zookeeper/conf/zoo.cfg |
|
TLSv1.2 |
|
Test TLS version
To get the TLS version currently used by ADH, you can use curl or OpenSSL as shown below.
Use curl
Below is a sample HTTPS request to the Hive server forcing curl to use the fairly deprecated TLSv1.1.
$ curl https://ka-adh-1.ru-central1.internal:10002/ --insecure --tlsv1.1 --tls-max 1.1The response indicates that TLSv1.1 is unsupported.
curl: (35) Peer reports incompatible or unsupported protocol version
If you omit --tlsv1.1 --tls-max 1.1, the default TLSv1.2 is used and curl returns a web page.
Use OpenSSL
The command below opens an SSL connection to a Tez server and OpenSSL attempts to get SSL certificates using the deprecated TLSv1.1.
$ openssl s_client -connect ka-adh-2.ru-central1.internal:9999 -tls1_1OpenSSL fails to establish the connection due to the unsupported TLS version.
no peer certificate available. No client certificate CA names send
If you omit -tls1_1, the default TLSv1.2 is used and OpenSSL retrieves a certificate.