

Configure a cluster
|
IMPORTANT
There is usually no need to change cluster configuration parameters. You can leave all parameters at the default values.
|
After creation a new cluster, you can configure it by performing the following steps:
-
Select a cluster on the Clusters page. To do this, click a cluster name in the Name column.
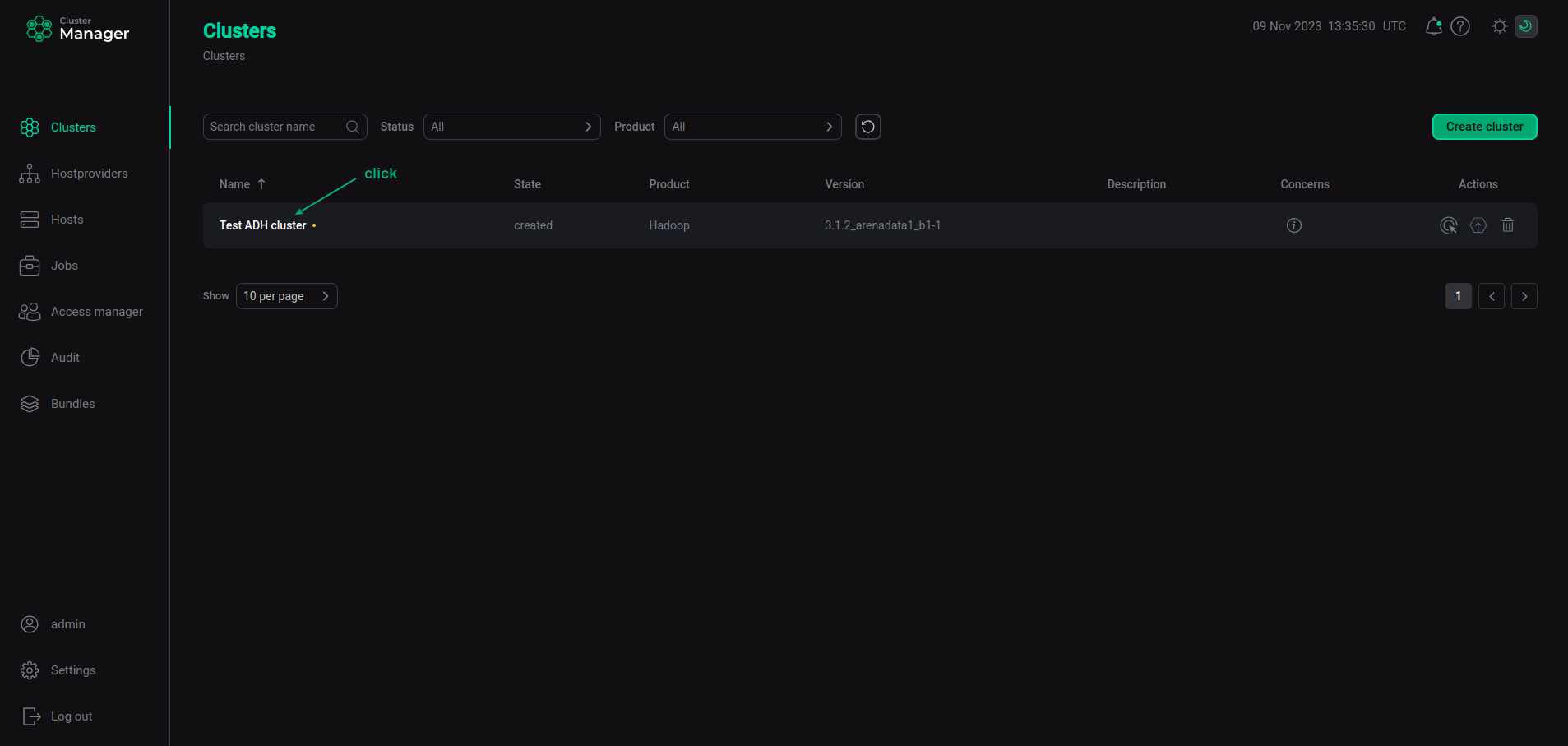 Select a cluster
Select a cluster -
Open the Configuration tab on the cluster page. The Configuration tab includes the following sections: Primary configuration, Configuration groups, Ansible settings.
-
Fill in all necessary parameters on the selected tab and click Save.
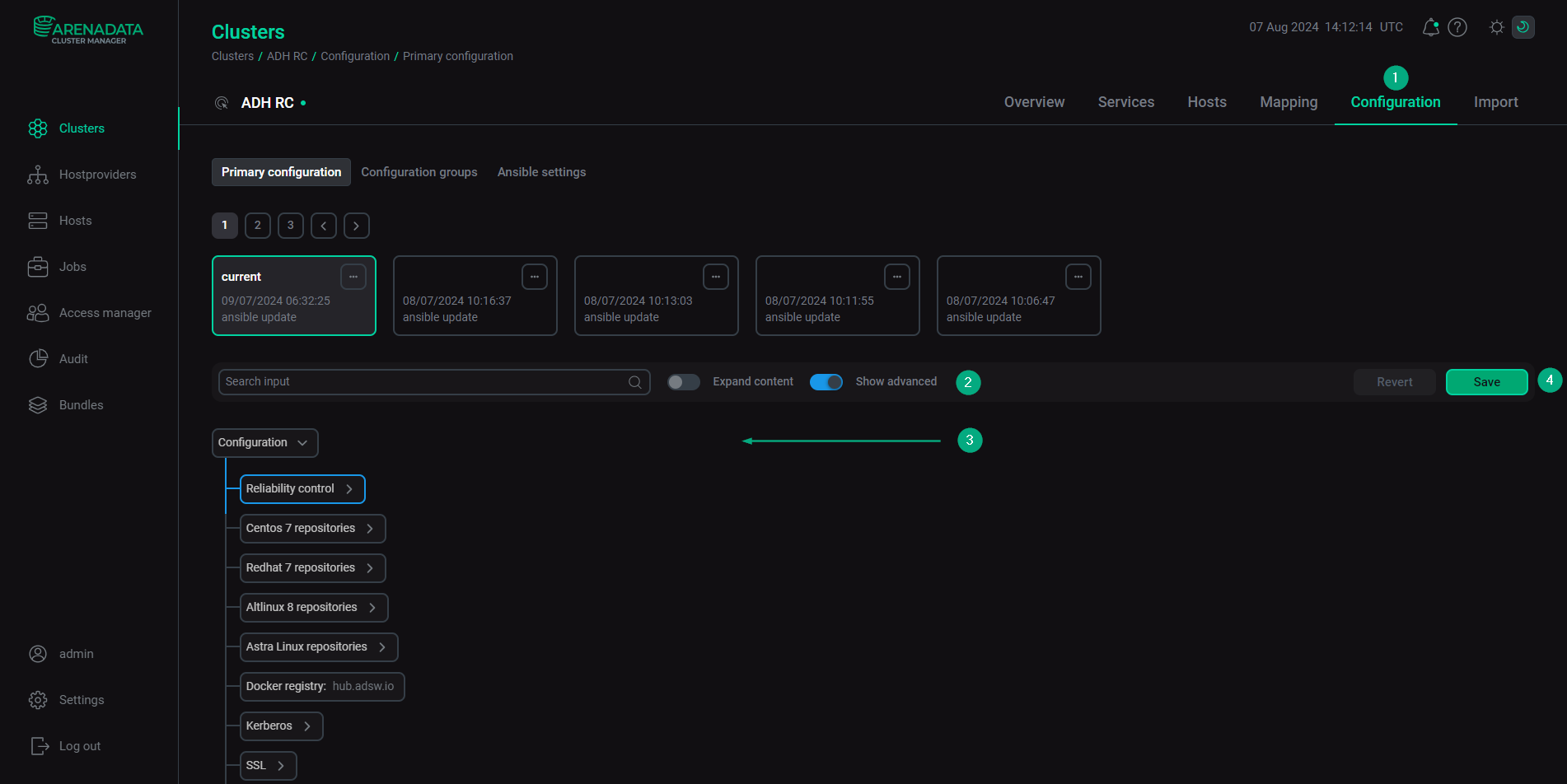
Primary configuration
The Configuration → Primary configuration tab allows you to configure the general cluster settings.
Available configuration parameters are listed below:
-
The Reliability control section. It is displayed if the Show advanced switch is activated. The section contains the following parameters:
-
retries — the number of retries for cluster operations (20 by default);
-
delay — the delay between retries in seconds (10 by default);
-
timeout — timeout for checks of network ports in seconds (60 by default).
-
-
Paths to the repositories that are used in the process of installing — depending on the cluster operating system (CentOS 7, Red Hat 7, Ubuntu 22, ALT Linux 8, Astra Linux, RedOS 7):
-
monitoring — monitoring components repository;
-
arenadata — Arenadata YUM repository;
-
arenadata_postgres — Arenadata PostgreSQL YUM repository;
-
prometheus_repo — Prometheus YUM repository;
-
arenadata_enterprise — Arenadata Enterprise YUM repository;
-
-
The Docker registry parameter that specifies a Docker Registry address. The default value is hub.adsw.io — Docker Registry from the Arenadata repository.
-
The Kerberos section that includes settings listed in the table below. Some options are visible only with the Show advanced option enabled.
Parameter Description Default value Enable Kerberos
Enables the Kerberos authentication
False
Authentication on WEB UIs
Enables the Kerberos authentication on WEB UIs
False
SPNEGO Signature Value
A secret key that is used to generate and verify the signature in the HTTP authentication protocol SPNEGO (in the Base64 format)
—
Kerberos KDC type
A KDC type. For more information, see Kerberos
MIT
KDC hosts
One or more KDC hosts with running FreeIPA server(s)
—
Realm
A Kerberos realm to connect to the FreeIPA server
—
Domains
One or more domains associated with FreeIPA
—
Kadmin server
A host where
kadminis running—
Kadmin principal
A principal name used to connect via
kadmin, for exampleadmin@RU-CENTRAL1.INTERNAL—
Kadmin password
An IPA Admin password
—
Keytabs directory
A directory with keytab files
/etc/security/keytabs
Additional realms
Additional Kerberos realms
—
Delay between kinit invocation attempts
Delay between kinit invocation attempts
5
Number of retries for kinit invocation attempts
Number of retries for kinit invocation attempts
10
Trusted Active Directory server
An Active Directory server for one-way cross-realm trust from the MIT Kerberos KDC
—
Trusted Active Directory realm
An Active Directory realm for one-way cross-realm trust from the MIT Kerberos KDC
—
Custom krb5.conf
Enables adding custom parameters to the krb5.conf file
False
krb5.conf
Additional parameters to write to the krb5.conf file
—
Admin DN
A full DistinguishedName of the admin user with rights to
create/modify/delete/pwdchangeuser accounts in the target Organizational Unit—
LDAP URL
LDAP URL that consists of the
ldap://orldaps://protocol prefix, hostname or IP address and port of an AD server. For example,ldaps://192.168.4.2:636—
Container DN
A container distinguished name
—
TLS CA certificate Path
A CA certificate path on the host filesystem that is pre-located or should be written from the TLS CA certificate field
—
TLS CA certificate (optional)
A CA certificate that is written on a host by the path from TLS CA certificate Path during the execution of the Manage Kerberos action. The certificate is not saved in ADCM
—
Custom ldap.conf
Enables adding custom parameters to the ldap.conf file
False
ldap.conf
Additional parameters that are written to the ldap.conf file
—
IpaClient No NTP Autoconf
Disables the NTP configuration during the IPA client installation
False
IpaClient No DNS Lookup
Disables the DNS lookup for the FreeIPA server during the IPA client installation
True
Custom smb.conf
Usage of custom configuration file smb.conf
False
smb.conf
Custom configuration file smb.conf
—
Set up Kerberos utils
Enables installation or removal of Kerberos clients and utils. Affects the Expand and Install actions
True
Configure Kerberos on hosts
Enables cluster configuration, including krb5.conf, ldap.conf
True
Set up principals and keytabs
Enables creation, recreation, or removal of principals and keytabs. Passwords for principals are generated randomly before keytab creation. Affects the Expand and Install actions. ADCM bundle will set up owner and permissions for keytabs only if this checkbox is selected in the cluster configuration. In case of absence of admin permissions, a customer should provide the prepared keytabs with correctly set owner and permissions (see Custom keytab recommendations)
True
Configure services and clients
Enables updating of services and clients configuration
True
Run service checks
Enables service check runs
True
-
The Credential encryption section with the encryption provider settings:
-
Credstore password — encryption provider password;
-
Credstore options — the way of storing the encryption provider password:
no password,password-file, orpassword in the environment.
-
-
The SSL section with the settings listed in the table below.
Parameter Description Default value Enable SSL
Enables SSL
false
Keystore path
A path to the keystore file
/etc/ssl/keystore.jks
Keystore password
A password for the keystore file
—
Truststore path
A path to the truststore file
/etc/ssl/truststore.jks
Truststore password
A password for the truststore file
—
TLS Version
Version of the TLS protocol. See Set TLS version for an ADH cluster
TLSv1.2
Run service checks
Enables service check runs
true
-
The java.io.tmpdir parameter that specifies an environment variable to control
java.io.tmpdirfor YARN, HBase, Hive, Spark3.
-
The ad-runtime-utils parameter contains a configuration file template that specifies the runtime detection installation path settings for a given runtime (Java, Python, etc.). The template contains cluster settings as well as service-specific settings for Trino, Flink, and Ozone. You can use this parameter to explicitly define the Java version. For more information, see Software Requirements — Java.
-
The
defaultsection configures the default behavior for the cluster. -
The
autodetectsection defines the algorithm for automatically detecting different Java versions. For each version (8, 17, 21, 23, 24), the following is configured:-
env_var— an environment variable that specifies version (for example,JAVA8_HOME,JAVA17_HOME); -
paths— a list of paths to search for the Java installation.
-
-
The
servicessection defines services for which specific Java versions are required.
-
default:
runtimes:
java:
version: "8"
env_var: JAVA_HOME
autodetect:
runtimes:
java:
"8":
env_var: JAVA8_HOME
paths:
- /usr/java/jdk1.8
- /usr/java/jre1.8
- /usr/lib/jvm/j2sdk1.8-oracle
- /usr/lib/jvm/j2sdk1.8-oracle/jre
- /usr/lib/jvm/java-8-oracle
- /usr/lib/jdk8-latest
- /usr/lib/jvm/java-1.8.0
- /usr/lib/jvm/java-1.8.0-oracle
- /usr/lib/jvm/bellsoft-java8-amd64
- /usr/lib/jvm/java-arenadata-openjdk-8
"17":
env_var: JAVA17_HOME
paths:
- /usr/lib/jvm/bellsoft-java17-amd64
- /usr/lib/jvm/bellsoft-java17
- /usr/lib/jvm/liberica-jdk-17*
- /usr/lib/jvm/liberica-jre-17*
- /usr/lib/jvm/zulu-17*
- /usr/lib/jvm/temurin-17*
- /usr/lib/jvm/adoptopenjdk-17*
- /usr/lib/jvm/jdk-17*
- /usr/lib/jvm/java-17*
- /usr/lib/jvm/openjdk-17*
- /usr/lib/jvm/openjdk-17*
- /opt/java/bellsoft-java17-amd64
- /opt/java/temurin-17*
- /usr/local/java/bellsoft-java17-amd64
- /usr/lib/jvm/java-arenadata-openjdk-17
- /usr/lib64/jvm/java-17*
"21":
env_var: JAVA21_HOME
paths:
- /usr/lib/jvm/java-21*
- /usr/lib/jvm/jdk-21*
- /usr/lib/jvm/java-arenadata-openjdk-21
"23":
env_var: JAVA23_HOME
paths:
- /usr/lib/jvm/bellsoft-java23-amd64
- /usr/lib/jvm/bellsoft-java23
- /usr/lib/jvm/liberica-jdk-23*
- /usr/lib/jvm/liberica-jre-23*
- /usr/lib/jvm/zulu-23*
- /usr/lib/jvm/temurin-23*
- /usr/lib/jvm/adoptopenjdk-23*
- /usr/lib/jvm/jdk-23*
- /usr/lib/jvm/java-23-openjdk
- /usr/lib/jvm/openjdk-23*
- /opt/java/bellsoft-java23-amd64
- /opt/java/temurin-23*
- /usr/local/java/bellsoft-java23-amd64
- /usr/lib/jvm/java-arenadata-openjdk-23
"24":
env_var: JAVA24_HOME
paths:
- /usr/lib/jvm/bellsoft-java24-amd64
- /usr/lib/jvm/bellsoft-java24
- /usr/lib/jvm/liberica-jdk-24*
- /usr/lib/jvm/liberica-jre-24*
- /usr/lib/jvm/zulu-24*
- /usr/lib/jvm/temurin-24*
- /usr/lib/jvm/adoptopenjdk-24*
- /usr/lib/jvm/jdk-24*
- /usr/lib/jvm/java-24-openjdk
- /usr/lib/jvm/openjdk-24*
- /opt/java/bellsoft-java24-amd64
- /opt/java/temurin-24*
- /usr/local/java/bellsoft-java24-amd64
- /usr/lib/jvm/java-arenadata-openjdk-24
services:
TRINO:
path: /etc/trino/conf/trino-java.yaml
FLINK2:
path: /etc/flink2/conf/flink2-java.yaml
OZONE:
path: /etc/ozone/conf/ozone-java.yaml
SPARK4:
path: /etc/spark4/conf/spark4-java.yaml-
The Precheck packages parameter that specifies whether the availability of the packages in the repository should be checked before installation.
Falseby default. -
Cluster UUID — displays the universally unique identifier of the cluster.
-
The Ranger plugins version parameter that allows you to override the version number for the Ranger plugins.
Configuration groups
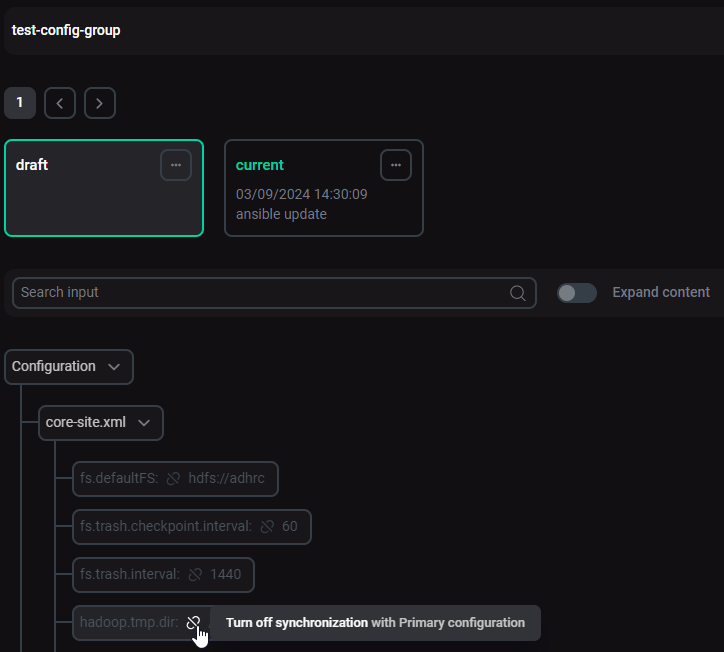
The Configuration → Configuration groups tab is designed to set cluster configuration groups.
To configure parameters in a configuration group, hover over the parameters that you wish to configure differently, click the Turn off synchronization icon, edit them, and click Save.
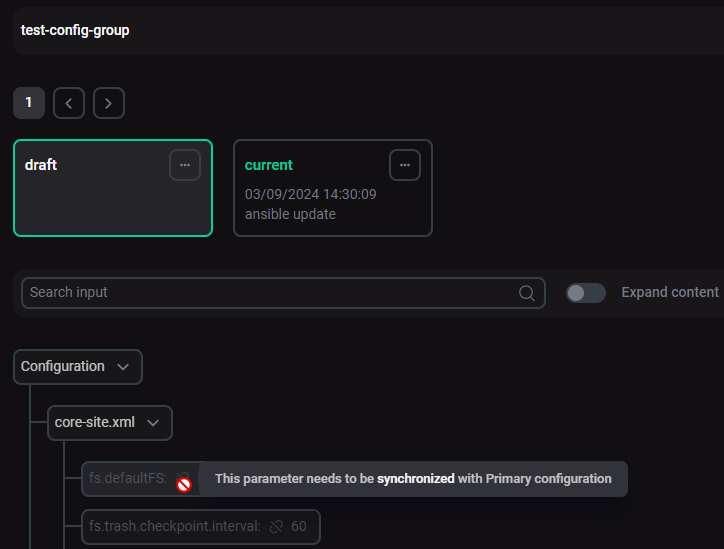
Some parameters you cannot change within a configuration group as they must always be synchronized with the primary configuration.
Ansible settings
The Configuration → Ansible settings tab allows you to set Ansible configuration options at the cluster level. The tab is available starting with ADCM 2.2.0.
| Name | Description | Default |
|---|---|---|
forks |
The number of parallel processes to spawn when communicating with remote hosts |
5 |