

Configure Kerberos authentication based on Samba via ADCM
Overview
Samba acts as an Active Directory domain controller, so its configuration is very similar to that of Active Directory.
Kerberization in ADCM
To kerberize a cluster using Samba, follow the steps below:
-
In the ADCM web UI, go to the Clusters page. Select an installed and prepared ADH cluster, and run the Manage Kerberos action.
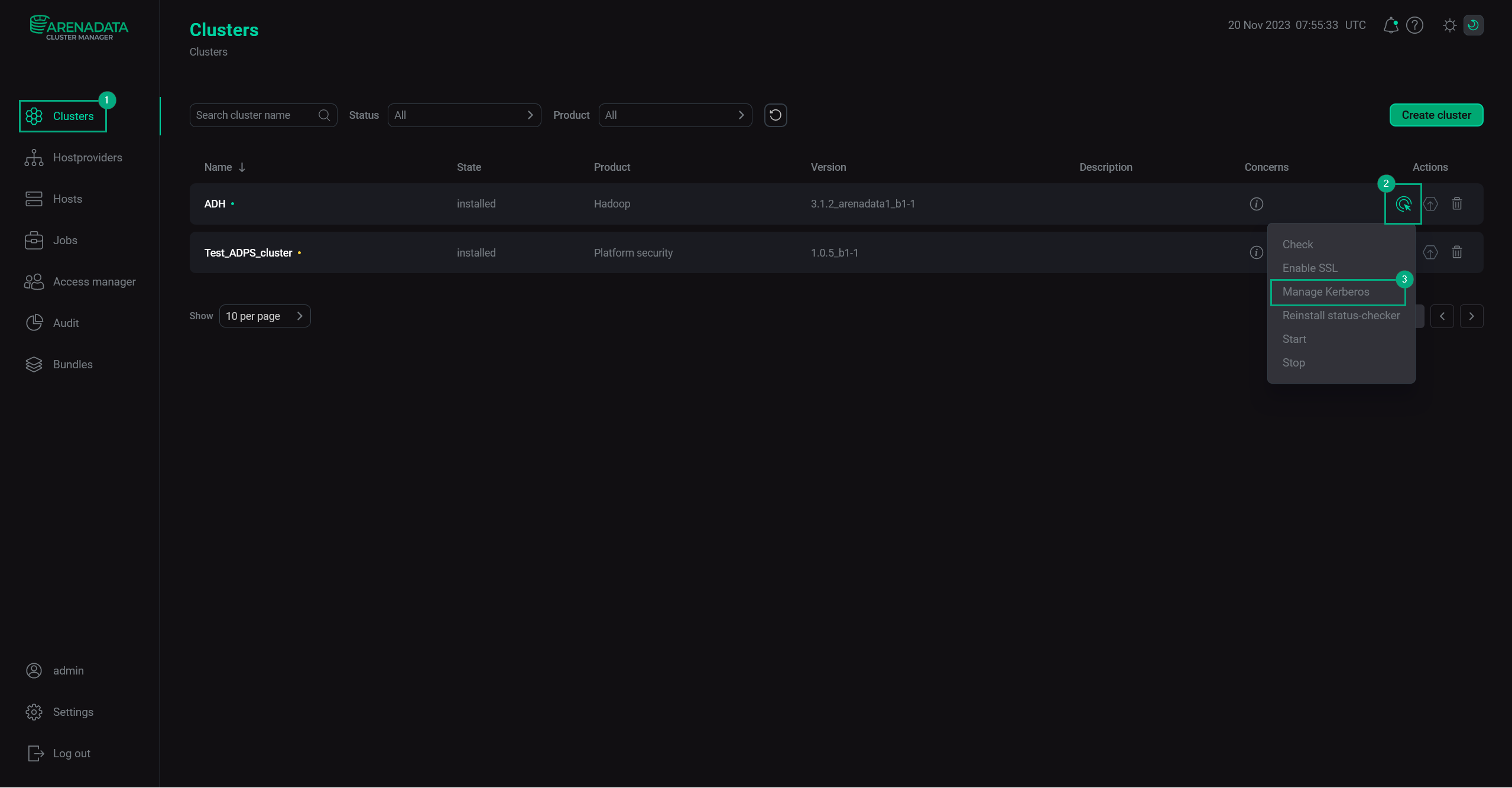 Manage Kerberos
Manage Kerberos -
In the pop-up window, turn on the Existing Samba option.
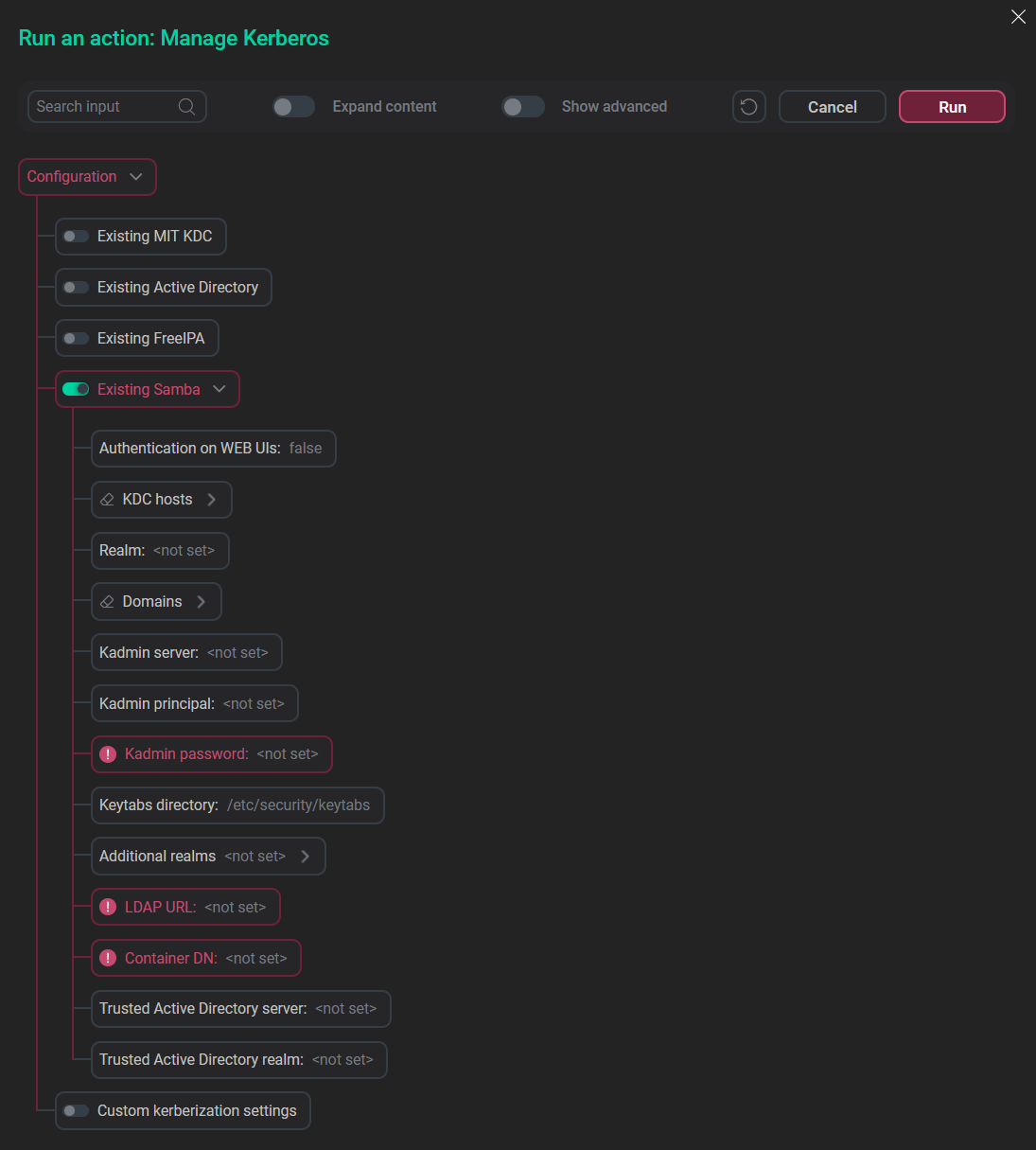 Choose the relevant option
Choose the relevant option -
Fill in the Samba Kerberos parameters.
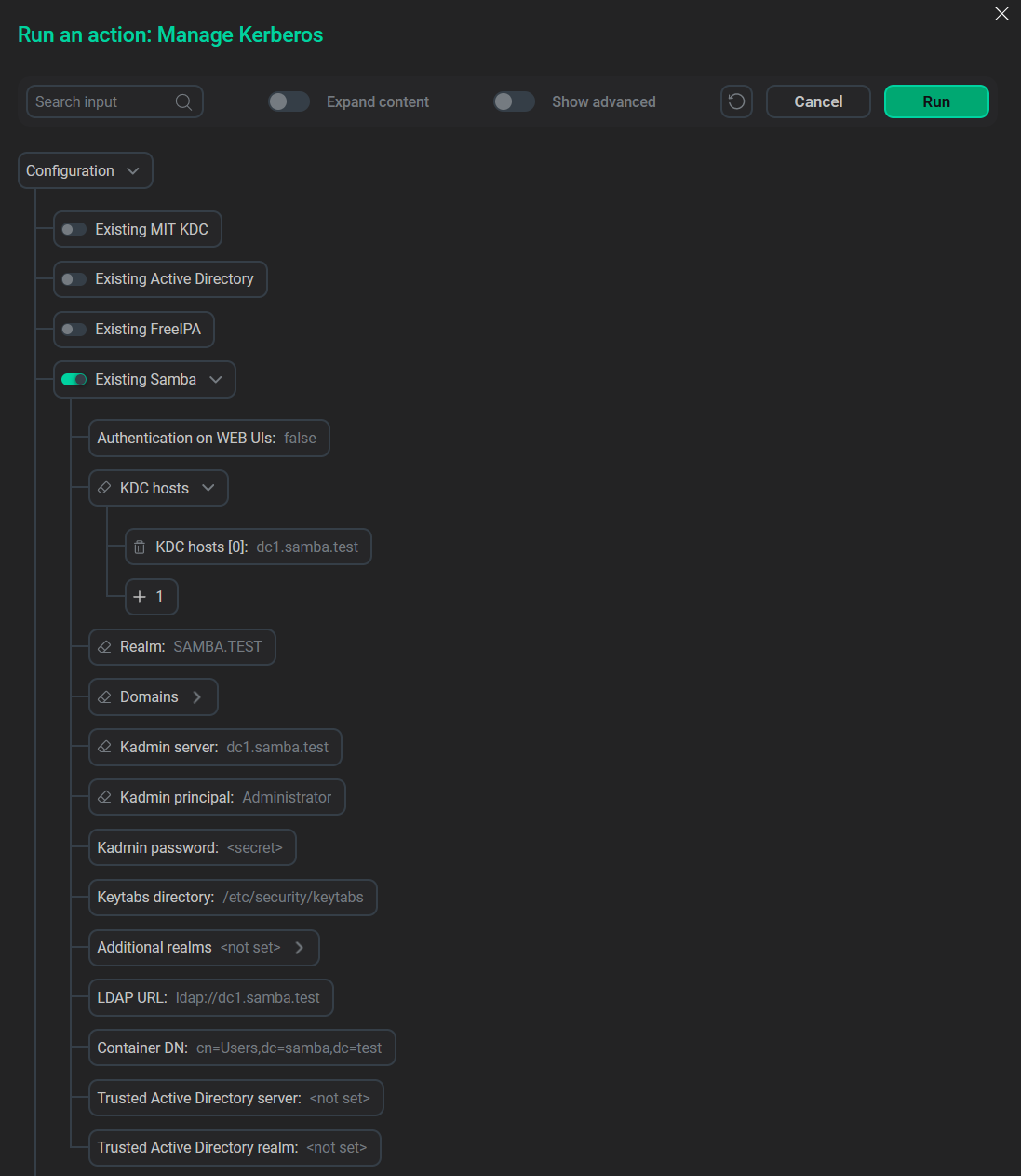 Samba Kerberos fields
Samba Kerberos fields -
Click Run, wait for the job to complete and proceed to setting up Kerberos in the cluster.
 Run the action
Run the action
To check, run the kinit command. If it doesn’t work with the generated keytabs on your system, it might be useful to add the following password encryption options to the libdefaults section of your custom krb5.conf cluster parameter in ADCM:
[libdefaults]
permitted_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 arcfour-hmac rc4-hmac arcfour-hmac-md5
default_tkt_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 rc4-hmac
default_tgs_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 rc4-hmacSamba Kerberos parameters
| Parameter | Description |
|---|---|
Authentication on WEB UIs |
Enables Kerberos authentication on Web UIs |
KDC hosts |
One or more domain controller hosts |
Realm |
A Kerberos realm |
Domains |
Domains associated with hosts |
Kadmin server |
A host where |
Kadmin principal |
A principal name used to connect via |
Kadmin password |
A principal password used to connect via |
Keytabs directory |
Directory of the keytab file that contains one or several principals along with their keys |
Additional realms |
Additional Kerberos realms |
LDAP URL |
LDAP URL consists of |
Container DN |
Container distinguished name |
Trusted Active Directory server |
A trusted DC server |
Trusted Active Directory realm |
A realm for cross-realm trust |