

Configure Kerberos authentication based on Active Directory via ADCM
Overview
To kerberize a cluster using Active Directory, follow the steps below:
-
In ADCM web UI, go to the Clusters page. Select an installed and prepared ADH cluster, and run the Manage Kerberos action.
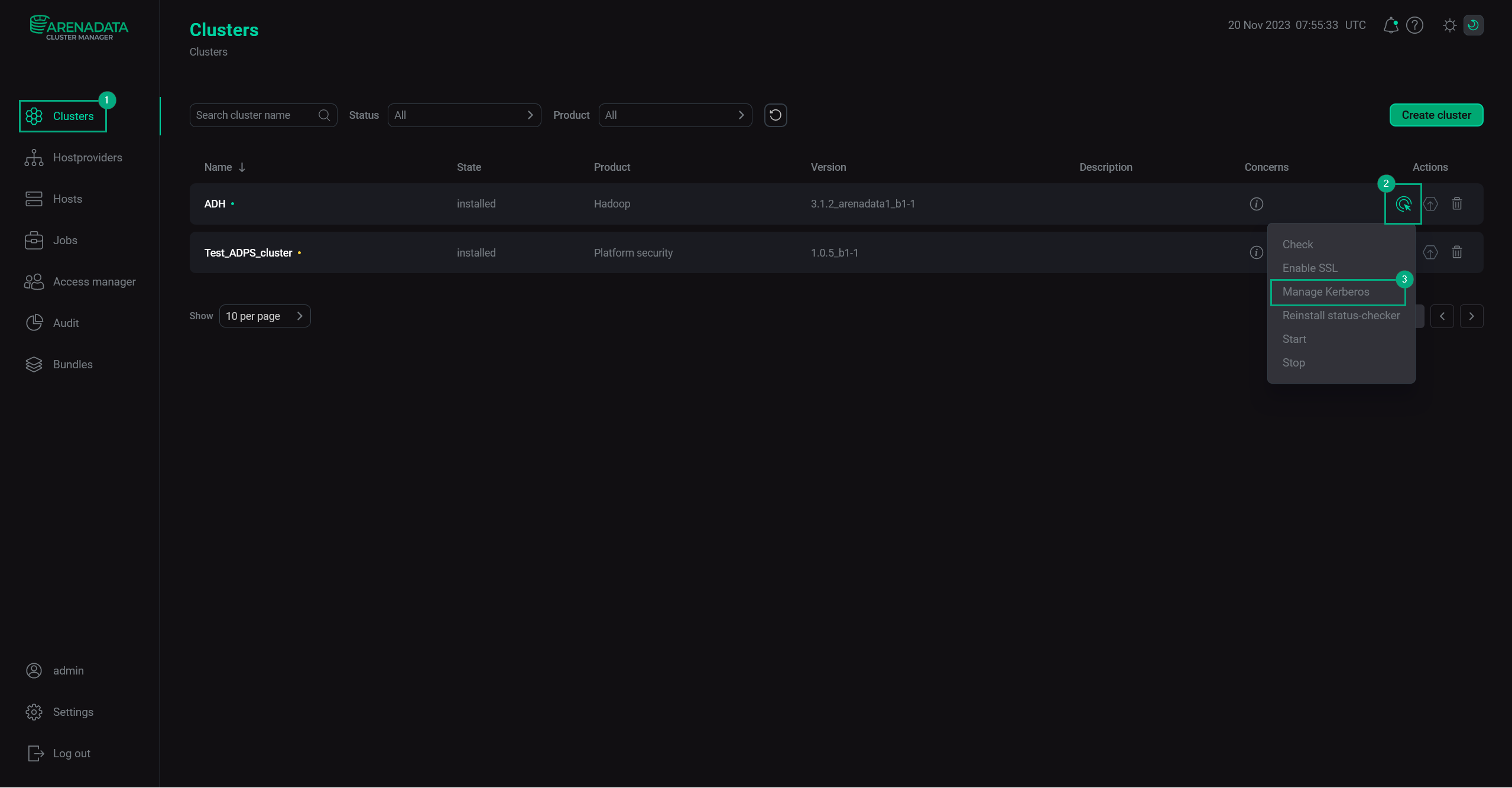 Manage Kerberos
Manage Kerberos -
In the pop-up window, turn on the Existing Active Directory option.
 Choose the relevant option
Choose the relevant option -
Fill in the Active Directory parameters.
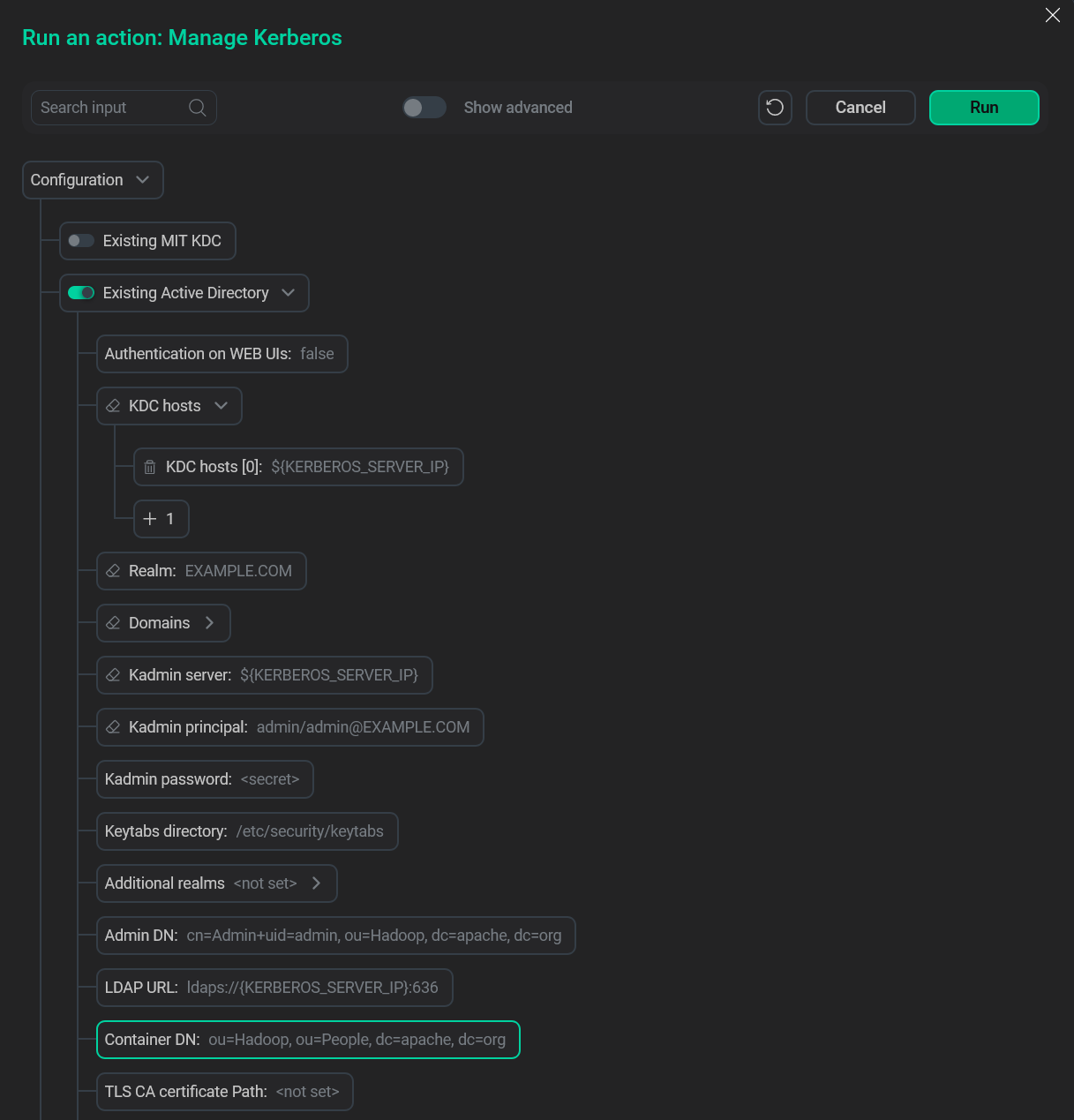 Active Directory fields
Active Directory fields -
Click Run, wait for the job to complete and proceed to setting up Kerberos in the cluster.
 Run the action
Run the action
Active Directory parameters
| Parameter | Description |
|---|---|
Authentication on WEB UIs |
Enables Kerberos authentication on Web UIs |
KDC hosts |
One or more KDC hosts |
Realm |
A Kerberos realm |
Domains |
Domains associated with hosts |
Kadmin server |
A host where |
Kadmin principal |
A principal name used to connect via |
Kadmin password |
A principal password used to connect via |
Keytabs directory |
Directory of the keytab file that contains one or several principals along with their keys |
Additional realms |
Additional Kerberos realms |
Admin DN |
Full distiguished name of admin user with rights create, modify, delete, pwdchange user accounts in the target Organizational Unit |
LDAP URL |
LDAP URL consists of |
Container DN |
Container distinguished name |
TLS CA certificate Path |
CA certificate path on the host’s filesystem. Should be preplaced or will be written down from the |
TLS CA certificate (optional) |
CA certificate to be written on a host using the path from the |
Trusted Active Directory server |
An Active Directory server for one-way cross-realm trust from the MIT Kerberos KDC |
Trusted Active Directory realm |
An Active Directory realm for one-way cross-realm trust from the MIT Kerberos KDC |