Enable Kerberos with prepared Active Directory server and no admin permissions
Prepare cluster hosts
-
Check that the ADH cluster is successfully installed and there are no issues.
-
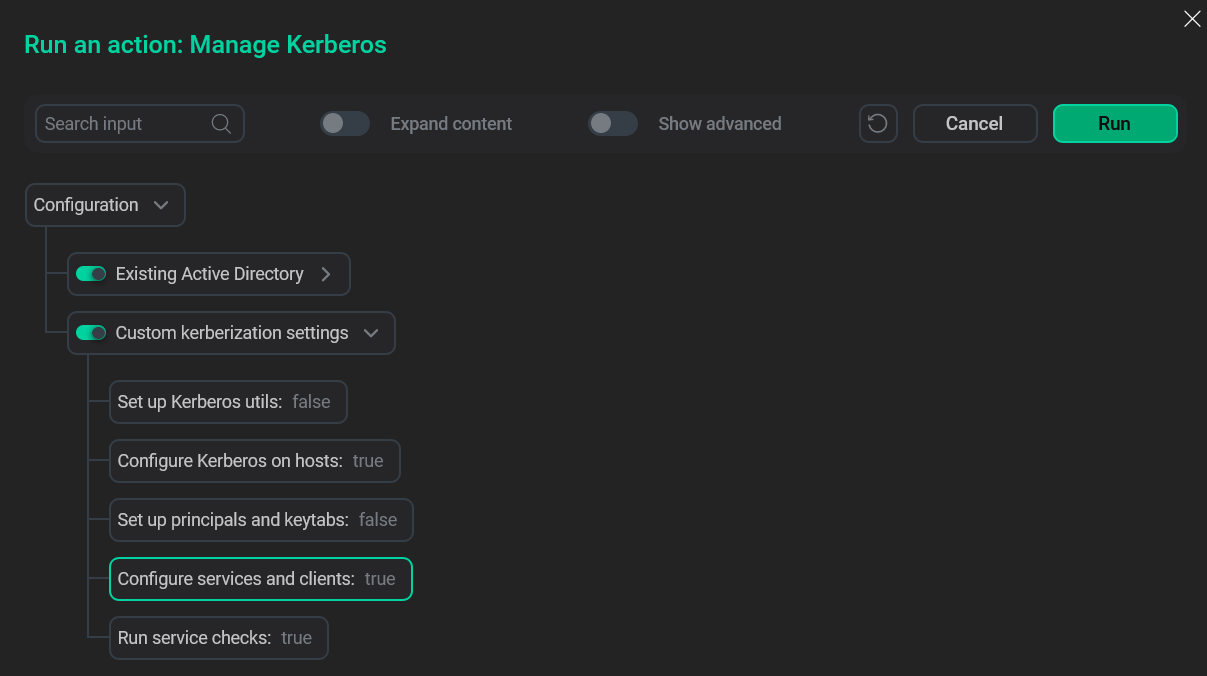
Add the krb5.conf file to the /etc/ directory. You can do it manually, but another way is to launch the Manage Kerberos action with the Existing Active Directory option selected and the Configure Kerberos on hosts parameter enabled in the Custom kerberization settings menu. Make sure to provide non-admin credentials while filling out the Existing Active Directory form.
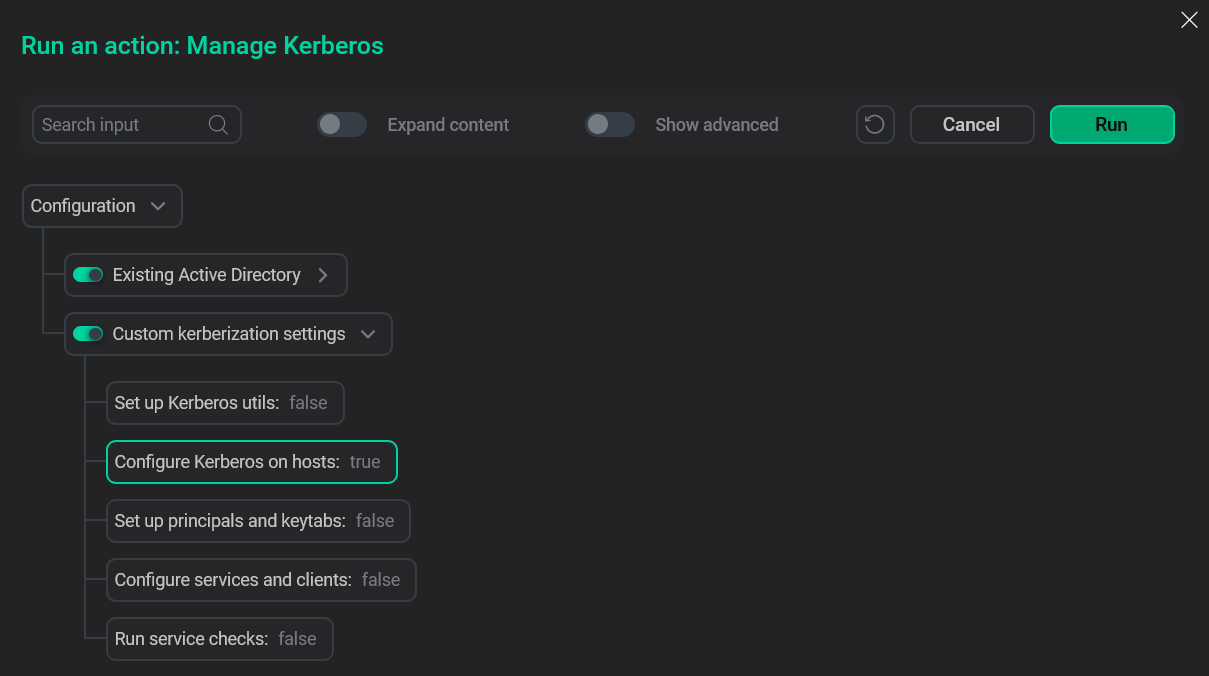 Config file creation
Config file creation -
Manually add principals for each service. You can use the Keytab column in the owner-keytab mapping table as a guide for which services you need to add a principal.
$ ldapadd -H <ldap_link> -x -D <username>@<realm> -w <password> -f <ldif_file>.ldifwhere:
-
<ldap_link>— link to the LDAP server. -
<username>— name of the LDAP user. -
<realm>— realm of the user. -
<password>— password for<username>. -
<ldif_file>— name of the file with principal information. An example of contents is presented below.
DN: CN=HTTP/<principal>,OU=Hadoop,DC=fresh,DC=com changetype: add objectClass: top objectClass: person objectClass: organizationalPerson objectClass: user accountExpires: 0 userPrincipalName: HTTP/<principal>@<realm> servicePrincipalName: HTTP/<principal> distinguishedName: CN=HTTP/<principal>,OU=Hadoop,DC=fresh,DC=com userAccountControl: 514where
<principal>is the principal name for a service.A successful principal addition should result in a message like the one below:
adding new entry "CN=HTTP/<principal>,OU=kerberos,ou=adh,DC=ad,DC=ranger-test"
To see a more detailed output, use the
-voption with ldapadd which enables the verbose mode.You can check the correctness of your principals using ldapsearch:
$ ldapsearch -x -H <ldap_link> -D <username>@<realm> -w <password> -b <search_base> <search_filter>where:
-
<search_base>— base for the search prompt. -
<search_filter>— search prompt.
-