

Enable Kerberos with prepared FreeIPA server and no admin permissions
Create an IPA user with no admin permissions
If you don’t have a non-admin IPA user, you can create one in FreeIPA UI. To do that, follow the steps below:
-
Login to your IPA server as admin, go to the Identity tab, and click Add.
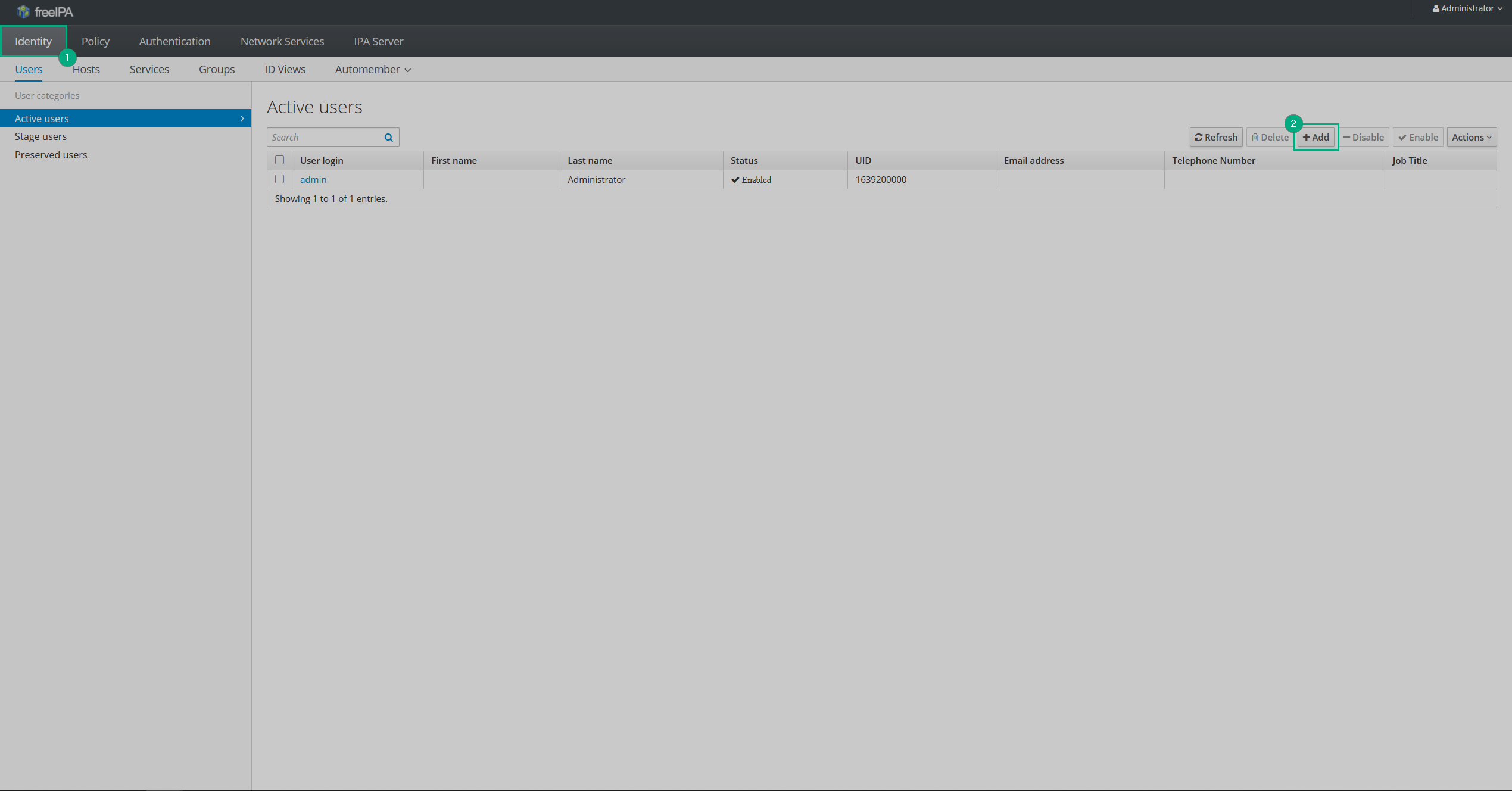 Adding an IPA user
Adding an IPA user Adding an IPA user
Adding an IPA user -
Fill in the form in the pop-up window.
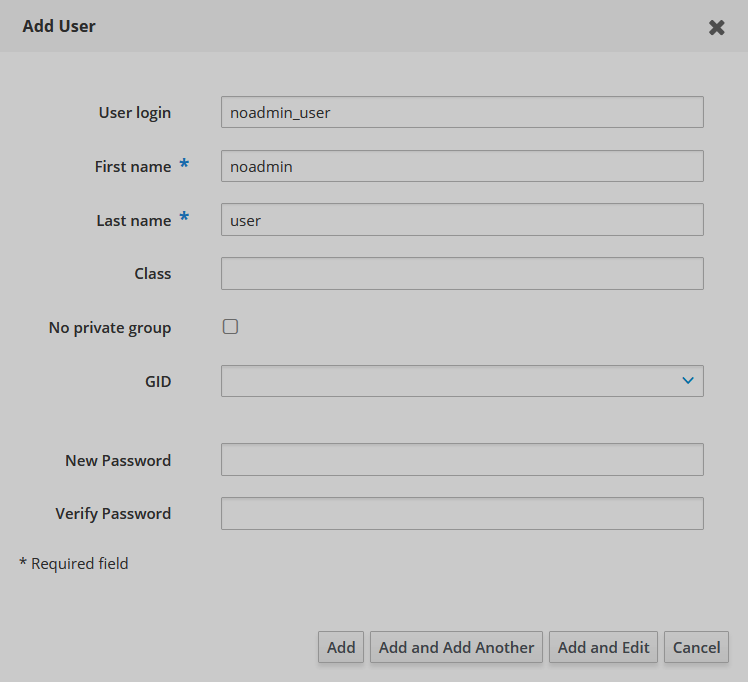 IPA user credentials
IPA user credentials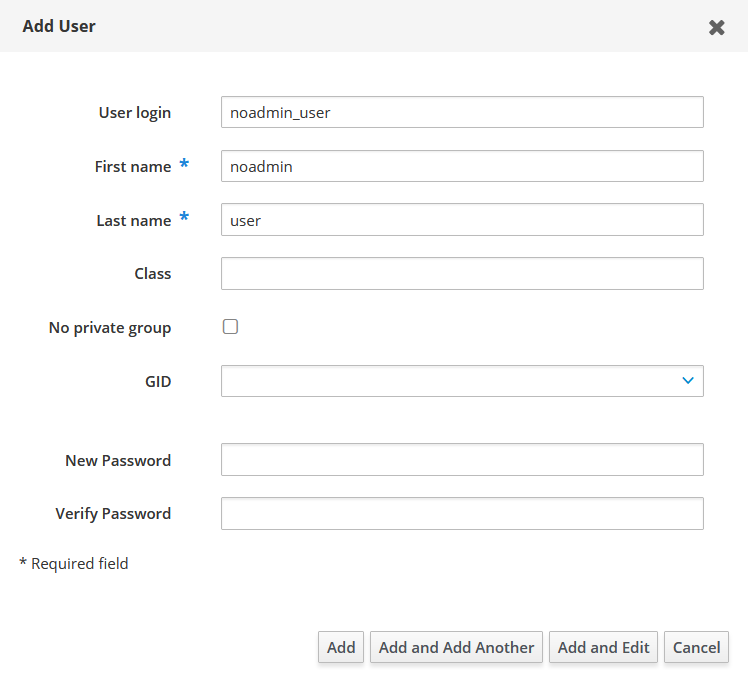 IPA user credentials
IPA user credentials -
Set a password for the user:
-
On the Identity tab, click on the new user in the User login column.
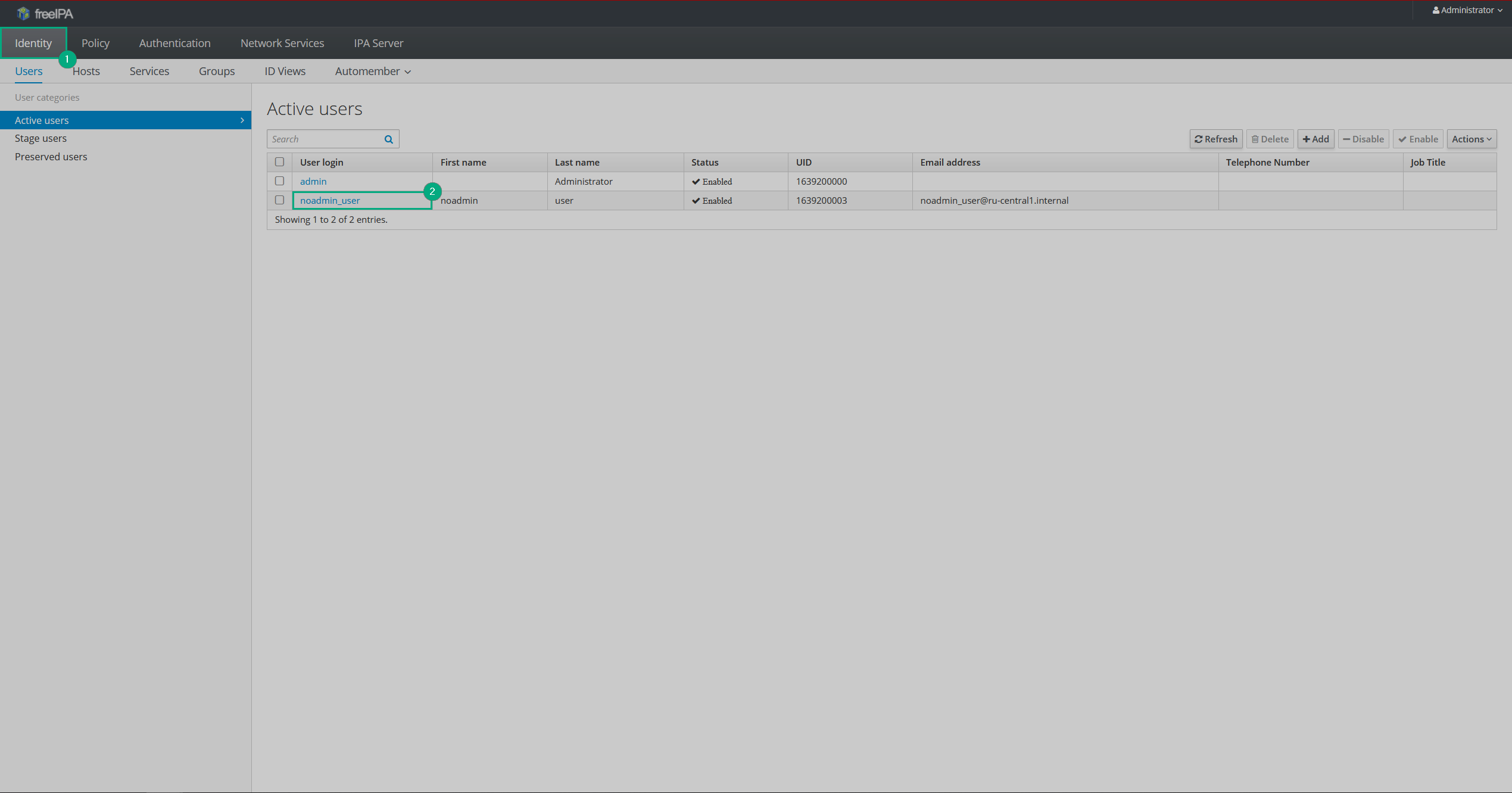 IPA users
IPA users IPA users
IPA users -
Click Actions → Reset password.
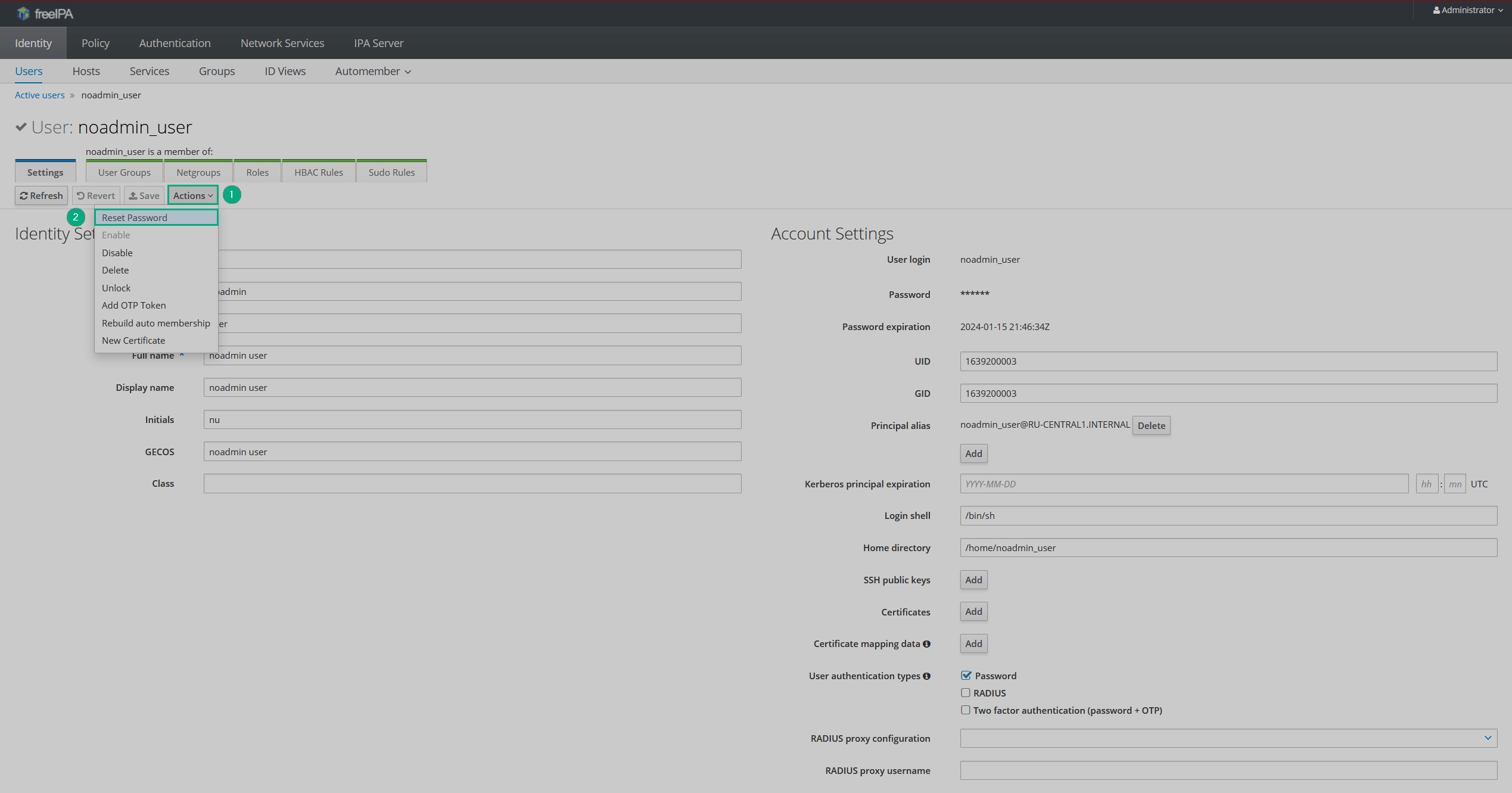 Setting a password
Setting a password Setting a password
Setting a passwordIn the pop-up window, enter the new password and confirm it.
-
Prepare cluster hosts
|
IMPORTANT
Note that the steps 2—8 can be done manually, but it’s highly recommended to use the script below to complete them automatically.
|
Do the following actions on each cluster host:
-
Add the krb5.conf file to the /etc/ directory. You can do it manually, but another way is to launch the Manage Kerberos action with Existing FreeIPA option and the Configure Kerberos on hosts parameter enabled in the Custom kerberization settings menu. Make sure to provide non-admin credentials while filling out the Existing FreeIPA form.
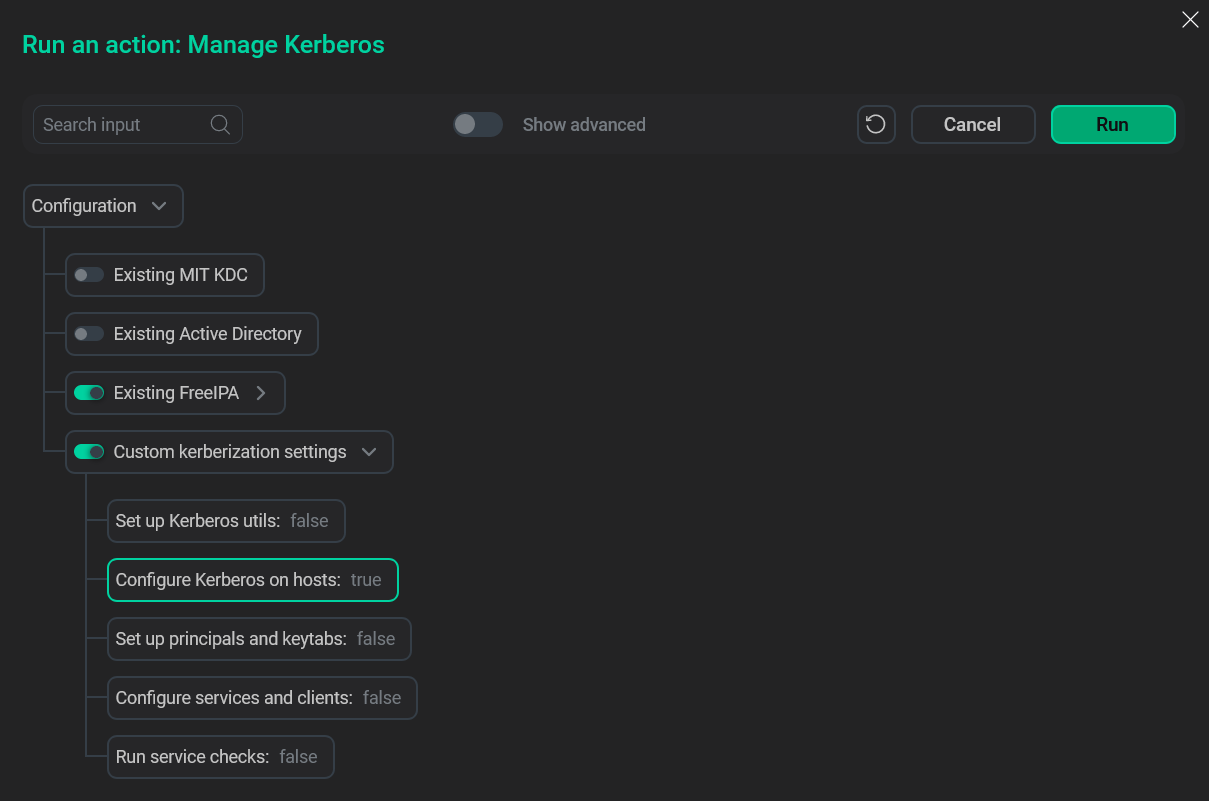 Config file creation
Config file creation -
Install the FreeIPA client by calling the command below:
$ sudo ipa-client-install -U -p <ipa_user> -w <ipa_pass> --server=<ipa_server> --domain=<domain> --realm=<realm>where:
-
<ipa_user>— non-admin username. -
<ipa_pass>— password for<ipa_user>. -
<ipa_server>— FQDN of a FreeIPA server. -
<domain>— FreeIPA domain. -
<realm>— FreeIPA realm.
-
-
Call
kinitwith non-admin credentials:$ kinit <username>where
<username>is a username for IPA user with no admin permissions. -
Add services to IPA. You can use the Keytab column in the owner-keytab mapping as a list of services you need to add.
$ ipa service-add <service_name>/<fqdn>where:
-
<service_name>— name of a service component. -
<fqdn>— FQDN of the host you launch the command on.
-
-
Add keytabs for each service and locate them in /etc/security/keytabs. You can use the Keytab column in the owner-keytab mapping as a list of keytabs you need to add.
$ ipa-getkeytab -p <service_name>/<fqdn> -k <service_name>.service.keytabwhere:
-
<service_name>— name of a service component. -
<fqdn>— FQDN of the host you launch the command on.
-
-
Add a user for each serivce if it doesn’t exist yet. You can use the Owner user column in the owner-keytab mapping as a list of services you need to add.
$ adduser <service_name>where
<service_name>is a name of a service. -
Change the owner for each keytab. You can use the owner-keytab mapping as guidance.
$ chown <user>:<group> <keytab_name>where:
-
<user>— owner username. -
<group>— owner group. -
<keytab_name>— name of a keytab file.
-
-
Set additional permissions (640) for Spark, HDFS, HBase, Hive, HTTP, and YARN service keytabs:
$ chmod 640 <keytab_name>where
<keytab_name>is a name of a keytab file.
Enable Kerberos
Run the Manager Kerberos action with FreeIPA user credentials. Also, disable the Set up Kerberos utils and Set up principals and keytabs parameters in the Custom kerberization settings menu.
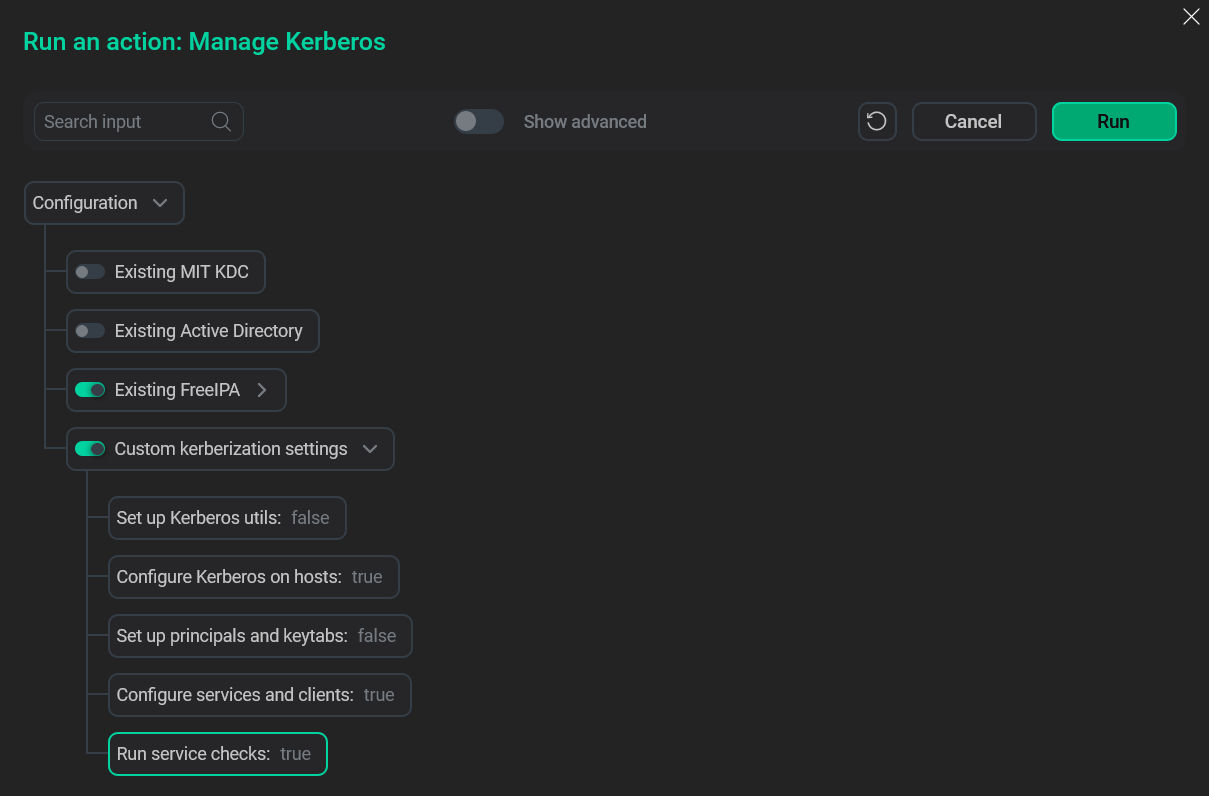
Additional information
| Owner user | Owner group | Keytab | Permissions |
|---|---|---|---|
airflow |
airflow |
airflow.service.keytab |
600 |
flink |
flink |
flink.service.keytab |
600 |
hbase |
hadoop |
hbase.service.keytab |
640 |
hbase |
hbase-thrift2.service.keytab |
600 |
|
hdfs |
hadoop |
HTTP.service.keytab |
640 |
hdfs-datanode.service.keytab |
600 |
||
hdfs-journalnode.service.keytab |
600 |
||
hdfs-namenode.service.keytab |
600 |
||
hdfs-zkfc.service.keytab |
600 |
||
hdfs.service.keytab |
640 |
||
hive |
hive |
hive.service.keytab |
640 |
httpfs |
httpfs |
httpfs.service.keytab |
600 |
livy |
hadoop |
livy.service.keytab |
600 |
mapred |
hadoop |
mapreduce-historyserver.service.keytab |
600 |
phoenix |
phoenix |
hbase-phoenix_queryserver.service.keytab |
600 |
solr |
solr |
solr.service.keytab |
600 |
spark |
spark |
spark.service.keytab |
640 |
yarn |
hadoop |
yarn-nodemanager.service.keytab |
600 |
yarn-resourcemanager.service.keytab |
600 |
||
yarn-timelineserver.service.keytab |
600 |
||
yarn.service.keytab |
640 |
||
zeppelin |
zeppelin |
zeppelin.service.keytab |
600 |
zookeeper |
zookeeper |
zookeeper.service.keytab |
600 |
impala |
impala |
impala.service.keytab |
600 |
#!/bin/bash
# Script for adding services and keytabs to Cluster hosts
# Edit NUMHOSTS and HOSTS as it will be suitable for your case.
# EDIT your IPA parameters
# Select services according to the bundle
declare -a NUMHOSTS
declare -a HOSTS
SSH_OPTS='-o GlobalKnownHostsFile=/dev/null -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no'
NUMHOSTS=(adh3-1 adh3-2 adh3-3)
HOSTS=$(for i in "${NUMHOSTS[@]}"; do echo "stikhomirov-$i.ru-central1.internal"; done)
#IPA credentials
ipa_user='noadmin_username'
ipa_pass='12345678'
ipa_server='stikhomirov-freeipa.ru-central1.internal'
domain='ru-central1.internal'
realm='RU-CENTRAL1.INTERNAL'
#ADH services
services=(airflow flink hbase-phoenix_queryserver hbase-thrift2 hbase hdfs-datanode hdfs-journalnode hdfs-namenode hdfs-zkfc hdfs hive httpfs livy mapreduce-historyserver solr spark sqoop yarn-nodemanager yarn-resourcemanager yarn-timelineserver yarn zeppelin zookeeper impala)
user-groups=(airflow:airflow flink:flink hbase:hadoop hbase:hbase hdfs:hadoop hdfs:hadoop hdfs:hadoop hdfs:hadoop hdfs:hadoop hdfs:hadoop hive:hive httpfs:httpfs livy:hadoop mapred:hadoop phoenix:phoenix solr:solr spark:spark sqoop:sqoop yarn:hadoop yarn:hadoop yarn:hadoop yarn:hadoop zeppelin:zeppelin zookeeper:zookeeper impala:impala)
users=(airflow flink hbase hdfs hive httpfs impala livy mapred phoenix solr spark sqoop yarn zeppelin zookeeper)
rwr_services=(spark hdfs hbase hive yarn HTTP)
for HOST in $HOSTS; do
echo "Installing FreeIPA client"
ssh $SSH_OPTS $HOST sudo ipa-client-install -U -p $ipa_user -w $ipa_pass --server=$ipa_server --domain=$domain --realm=$realm
echo "Creating keytab directory"
ssh $SSH_OPTS $HOST sudo mkdir /etc/security/keytabs
echo "Launching kinit on $HOST"
ssh $SSH_OPTS $HOST sudo kinit $ipa_user <<< $ipa_pass
for user in ${users[@]}; do
echo "Adding $user user"
ssh $SSH_OPTS $HOST sudo adduser $user
done
for service in ${!services[@]}; do
echo "Adding $service service to IPA"
ssh $SSH_OPTS $HOST sudo ipa service-add ${services[i]}/$HOST
echo "Get $service keytab"
ssh $SSH_OPTS $HOST sudo ipa-getkeytab -p ${services[i]}/$HOST -k /etc/security/keytabs/${services[i]}.service.keytab
echo "Changing owner for $service keytab"
ssh $SSH_OPTS $HOST sudo chowner ${user-groups[i]} /etc/security/keytabs/${services[i]}.service.keytab
done
for service in ${rwr_services[@]}; do
echo "Setting 640 permissions for $service"
ssh $SSH_OPTS $HOST sudo chmod 640 /etc/security/keytabs/$service.service.keytab
done
done