

Manage Credential Encryption
The Manage Credential Encryption action allows you to control ADH services configuration encryption. The encryption is implemented via a Hadoop or KMS credential provider that supports storing passwords in the JCEKS (an encrypted container with passwords, i.e. credential store) instead of configuration files. By default, the credential store is protected by a password that is stored in the environment for each encrypted service, but you can keep that password in a file if such option is available for a service.
Enable encryption with a cluster action
To enable the credential encryption, follow the steps below:
-
Head to the Clusters page and run the Manage Credential Encryption action for your ADH cluster.
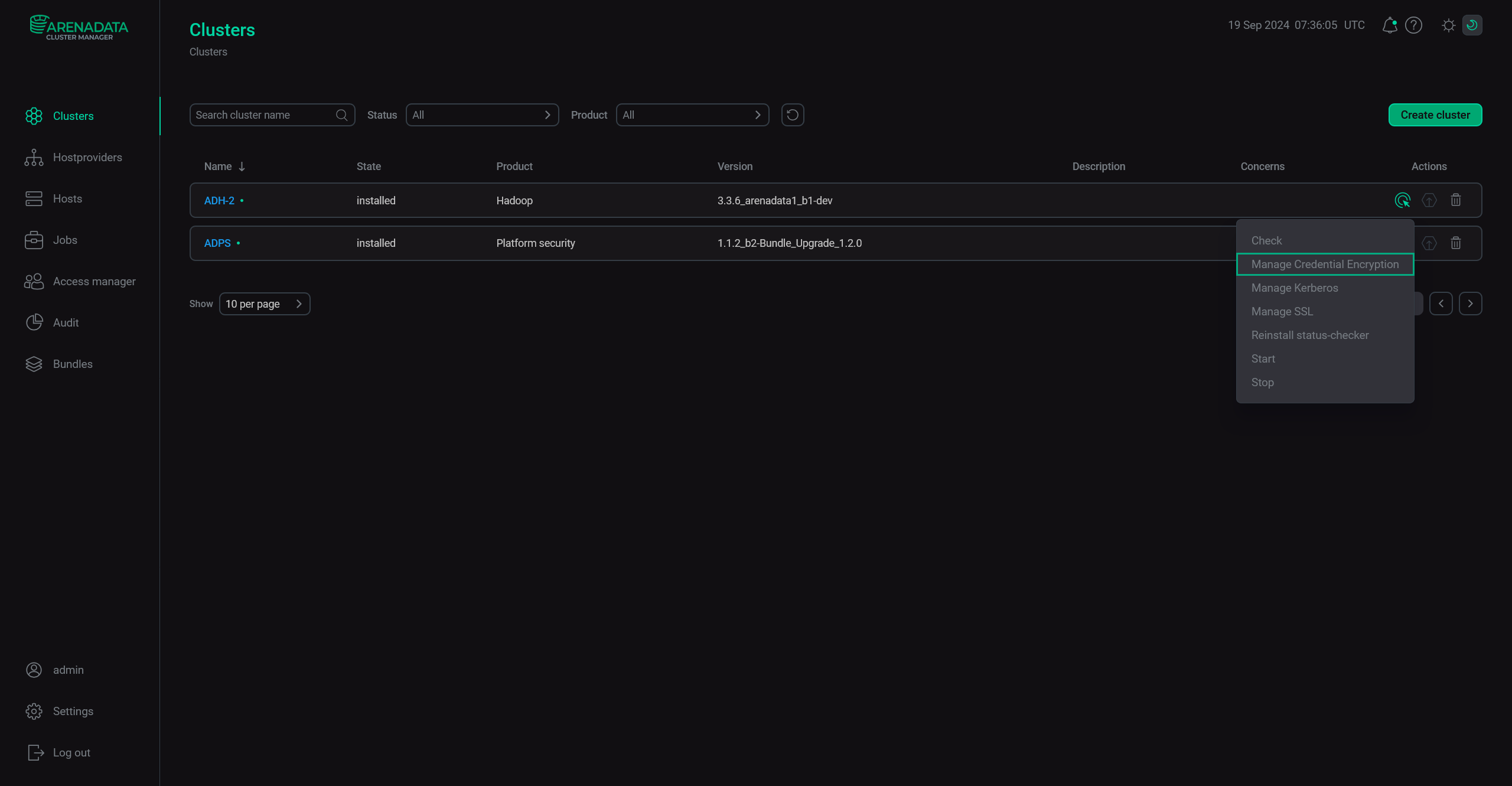 Run the "Manage Credential Encryption" action
Run the "Manage Credential Encryption" action -
In the opened window, set the encryption settings:
-
Credstore password — the encryption provider password.
-
Credstore options — the way to store the encryption provider password. Three options are available:
no password,password-file, andpassword in the environment.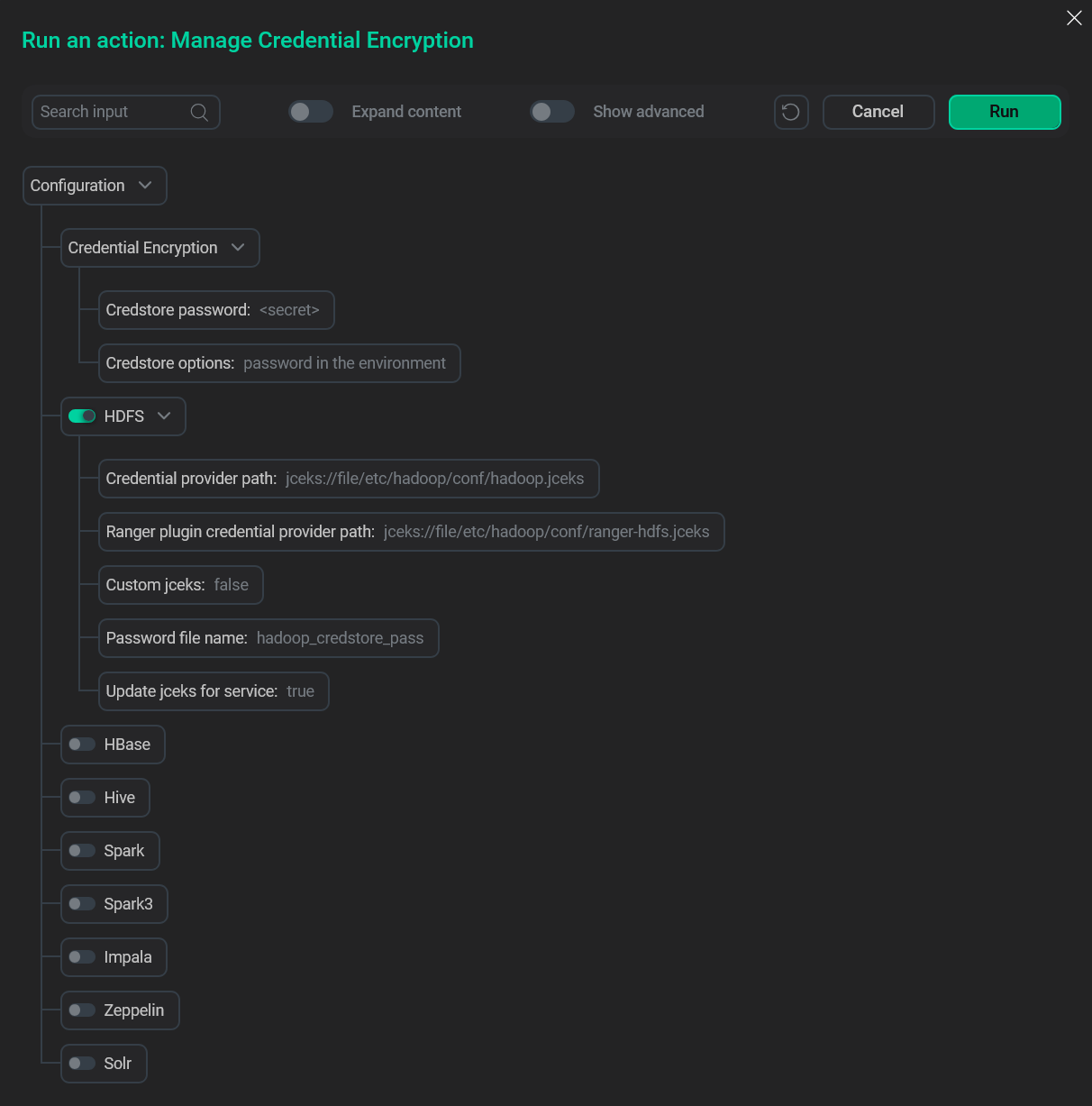 The credential encryption parameters
The credential encryption parameters
-
-
In the same window, select the services for which you want to activate encryption and provide the necessary data:
-
Credential provider path — a credential provider path for creating the JCEKS files with secrets. Can be a local or HDFS path.
-
Ranger plugin credential provider path — a Ranger plugin credential provider path for creating the JCEKS files with secrets.
-
Custom jceks — if enabled, allows you to use your own credential store. Otherwise — generates JCEKS files automatically.
-
Password file name — a filename in service’s classpath for storing the password file. It is accounted for only if the
password-filevalue is selected in the Credstore options parameter. -
Update jceks for service — defines whether to recreate the JCEKS files for this service. Takes effect only if the JCEKS files were previously created. Activate if you have changed the SSL (keystore, truststore) or LDAP passwords, the DB connection password, or any other password in a service configuration.
You can enable the encryption for HDFS (with YARN), HBase, Hive, Impala, Kyuubi, Spark/Spark3, Zeppelin, and Solr. The parameter list above is similar for each service — some services don’t require all the parameters.
-
-
The action also has an advanced mode, enabling which allows you to reconfigure services and recreate JCEKS files for them. Here, you can unselect the unaffected services so that they will not be reconfigured (which makes sense since their configuration hasn’t been changed).
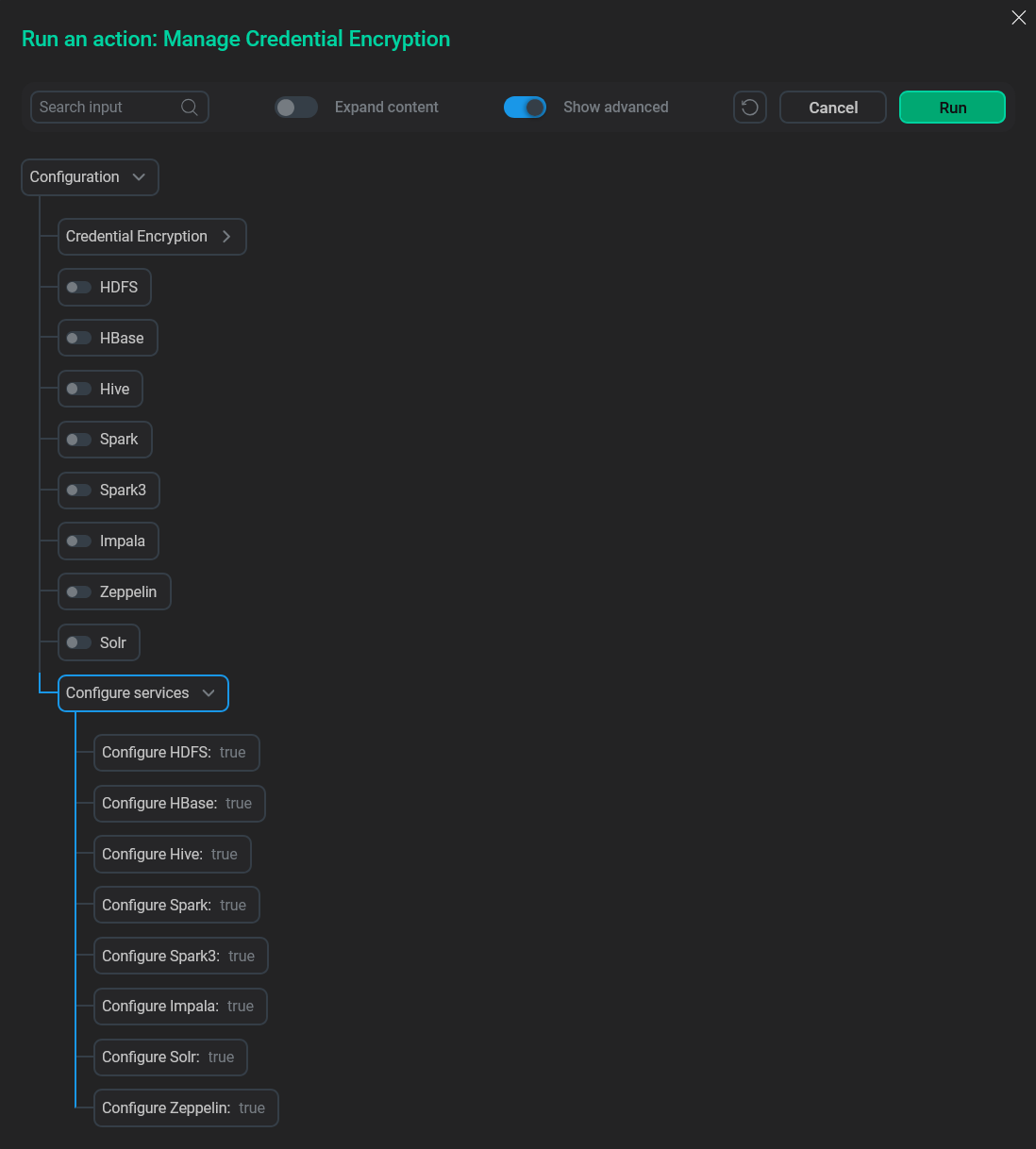 Advanced mode
Advanced mode -
Click Run and confirm the action in a pop-up window.
 Confirmation window
Confirmation window
Enable encryption for a service
There is an alternate way to enable the credential encryption for a service that supports it. Instead of launching the Manage Credential Encryption action, you can do the following:
-
Head to the Services tab of your ADH cluster and select a service for which you want to enable encryption.
-
Expand the Credential Encryption parameter group and configure the parameters shown below.
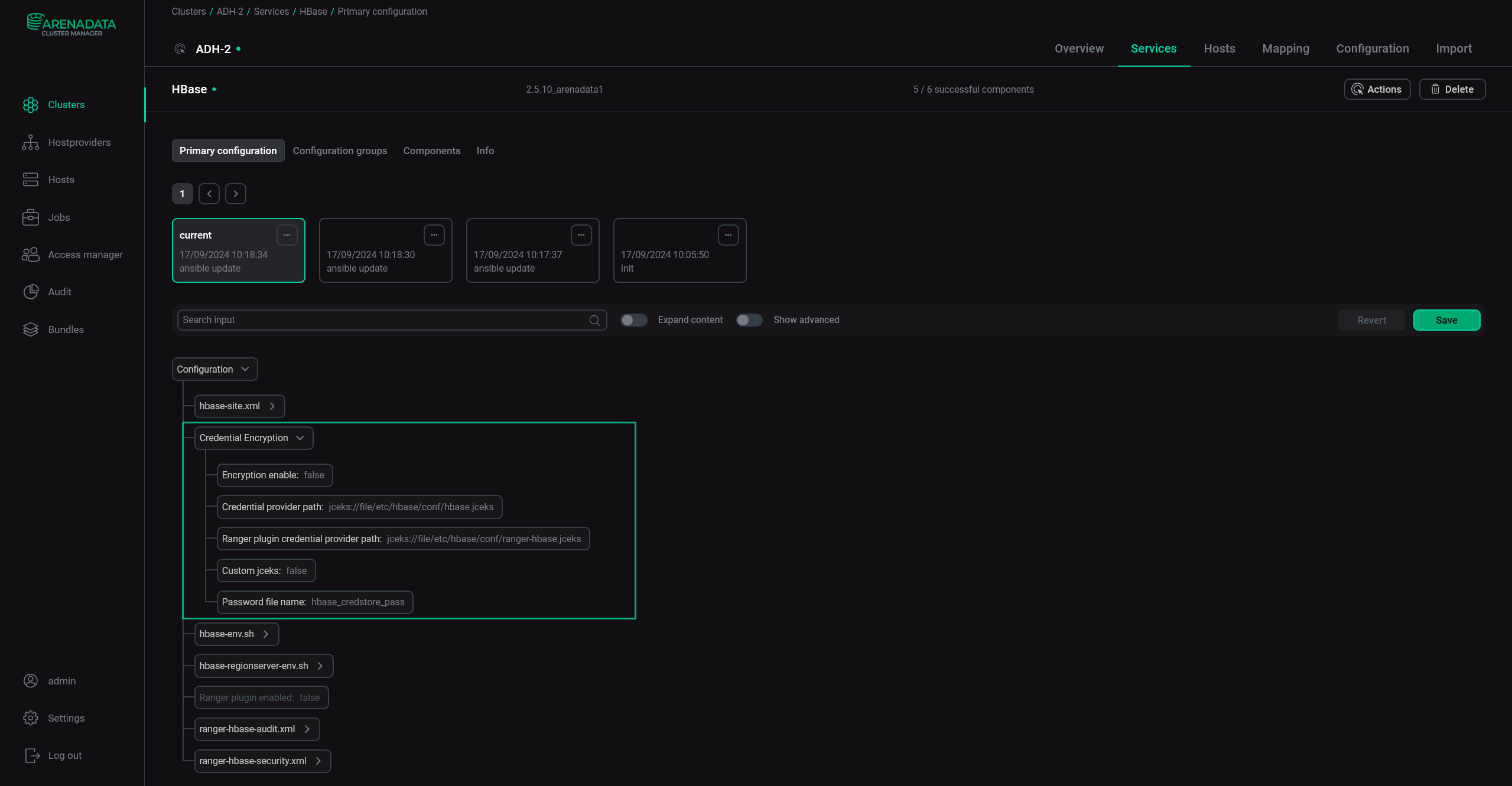 Service configuration
Service configurationThe parameter list is similar to the one in the Manage Credential Encryption action, but there is one new flag parameter — Encryption enable. To enable credential encryption, you need to activate it and save the service configuration.
-
Restart the service. The Update jceks parameter appears in the action menu only after enabling the Encryption enable configuration parameter. It is needed during the first encryption activation via the Restart action (as opposed to the Manage encryption action, which creates a JCEKS archive with passwords automatically with no additional actions required).
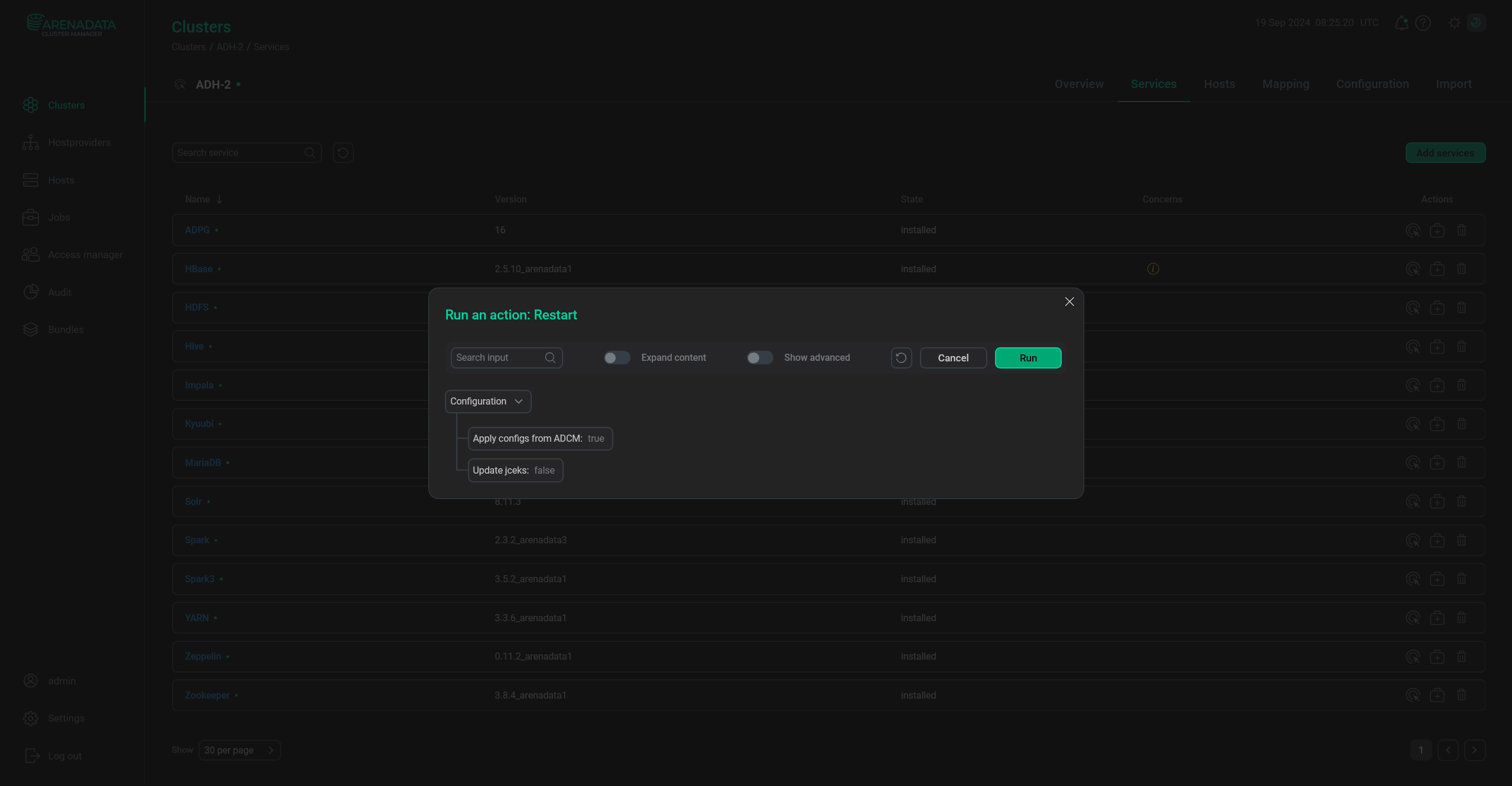 The "Update jceks" parameter
The "Update jceks" parameterTo update the JCEKS files (when a service password or provider settings have changed), activate it and click Run.