

Ranger authorization with Hive policies
The Trino Ranger plugin can be configured for the Hadoop SQL policies. This article describes how to configure and test this feature.
Setup
-
Enable the Hive Ranger plugin.
-
Enable the Trino Ranger plugin with the Hive SQL Support parameter activated. Make sure that the ranger.plugin.hive.service.name parameter matches the Hive service name in Ranger.
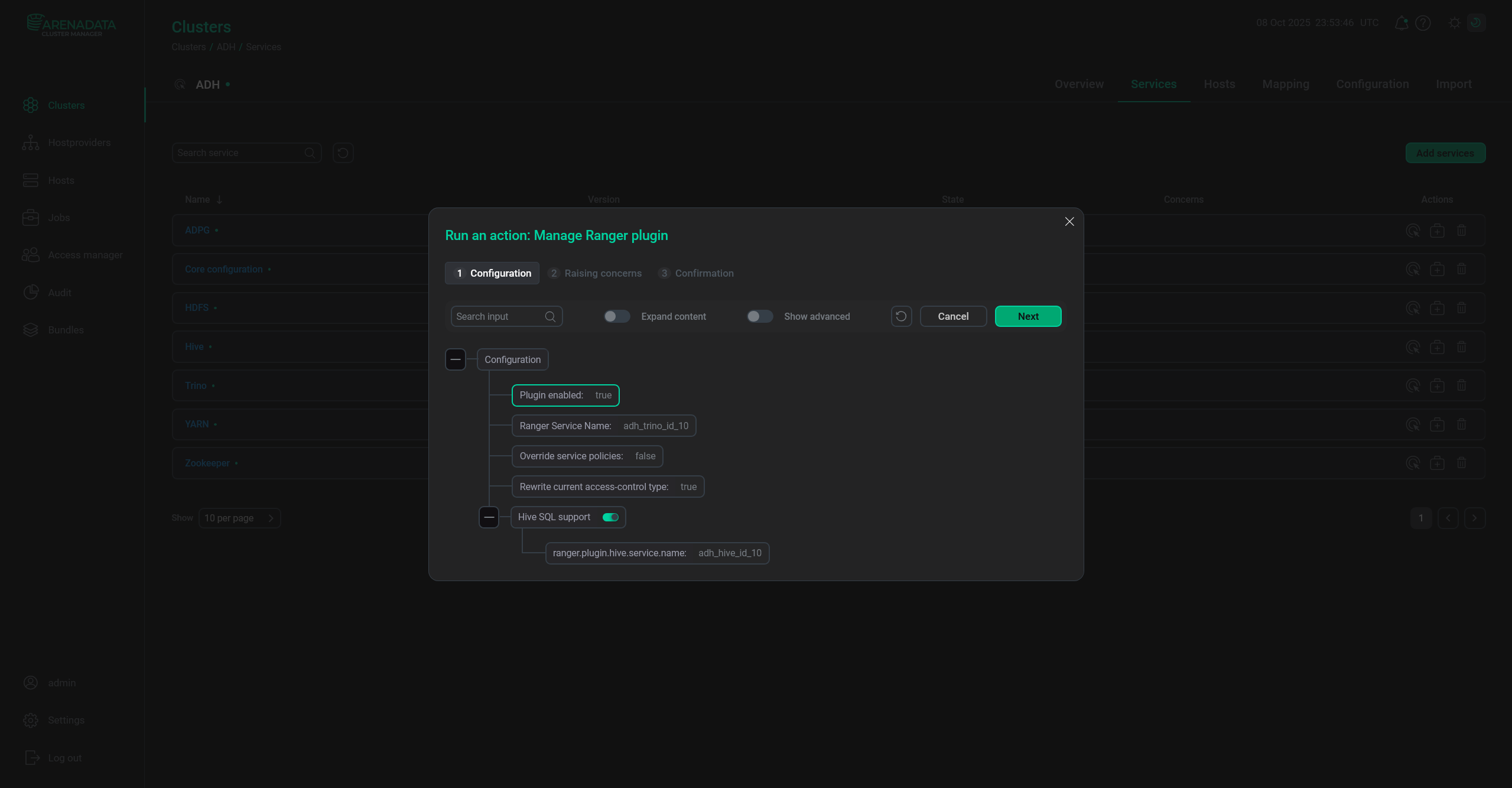 The Trino Ranger plugin parameters
The Trino Ranger plugin parameters -
Remove the
all - catalog, schema, table, columnpolicy for Trino in Ranger.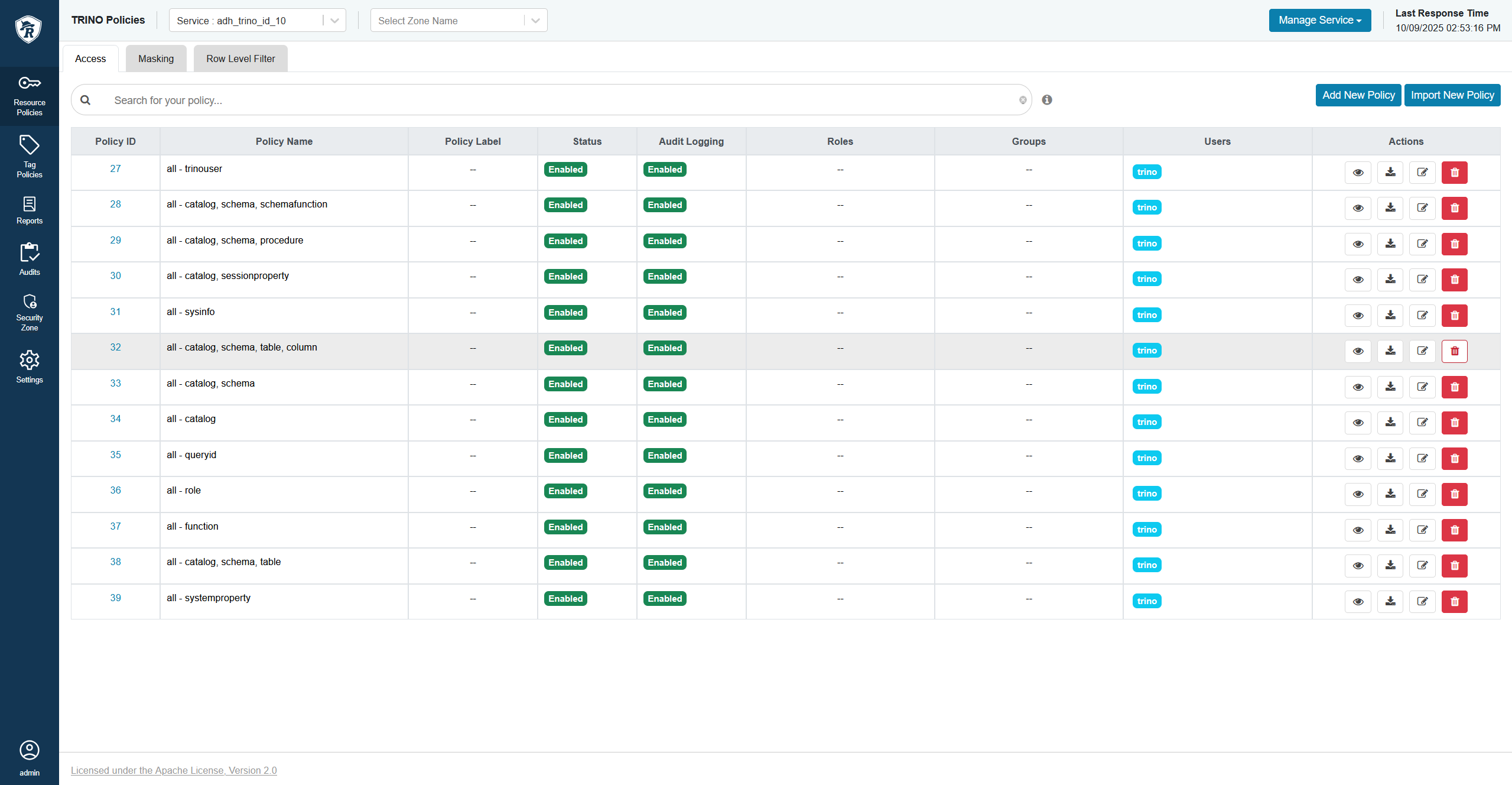 The Trino policy to remove
The Trino policy to remove The Trino policy to remove
The Trino policy to remove -
Add a user that should be able to authenticate into the
all - trinouser,all - catalog, schema, andall - queryidpolicies in Trino. -
In Hive, create a policy that would allow the user access to all columns in a specific database and table.
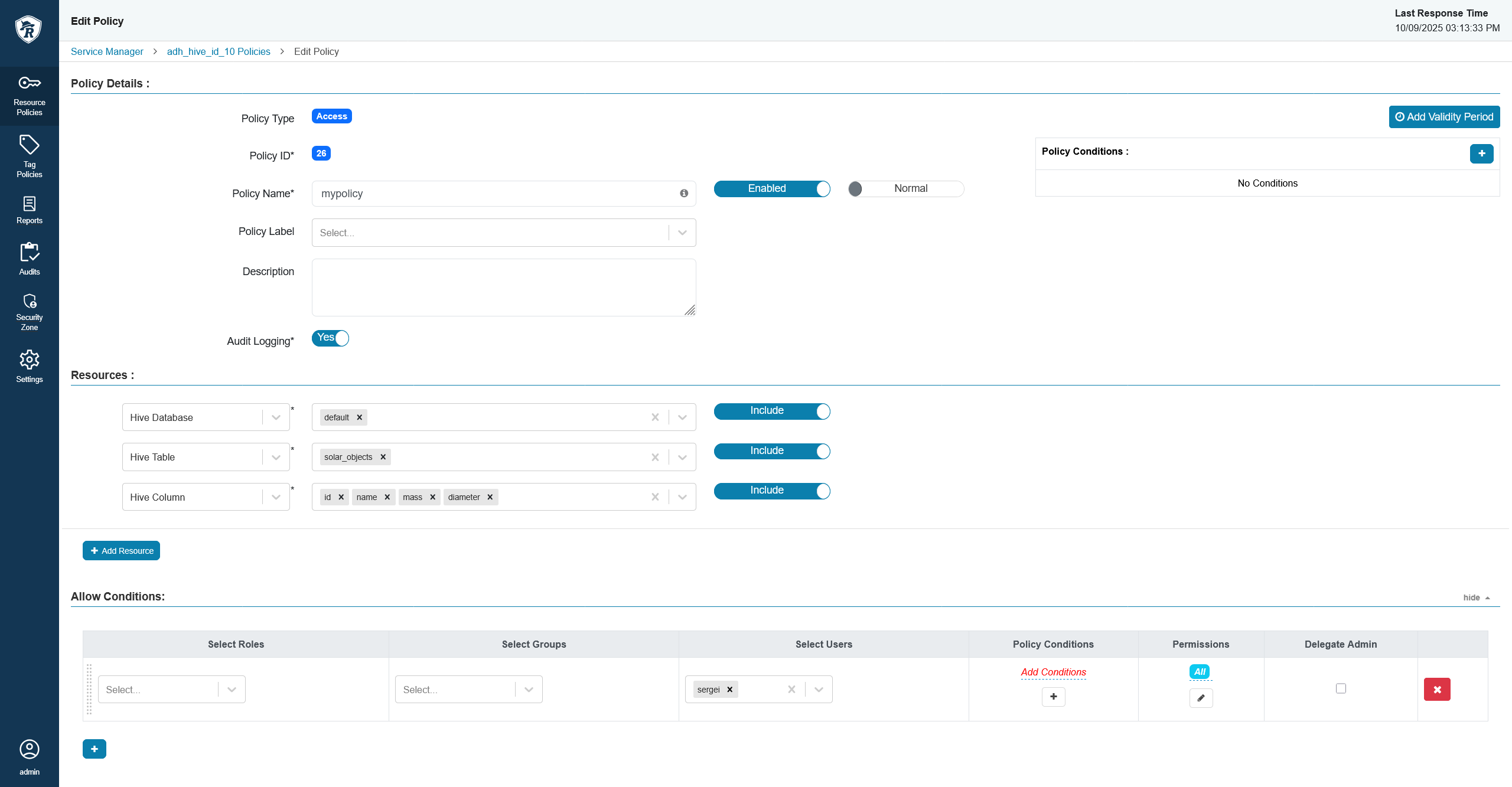 Create a Hive policy
Create a Hive policy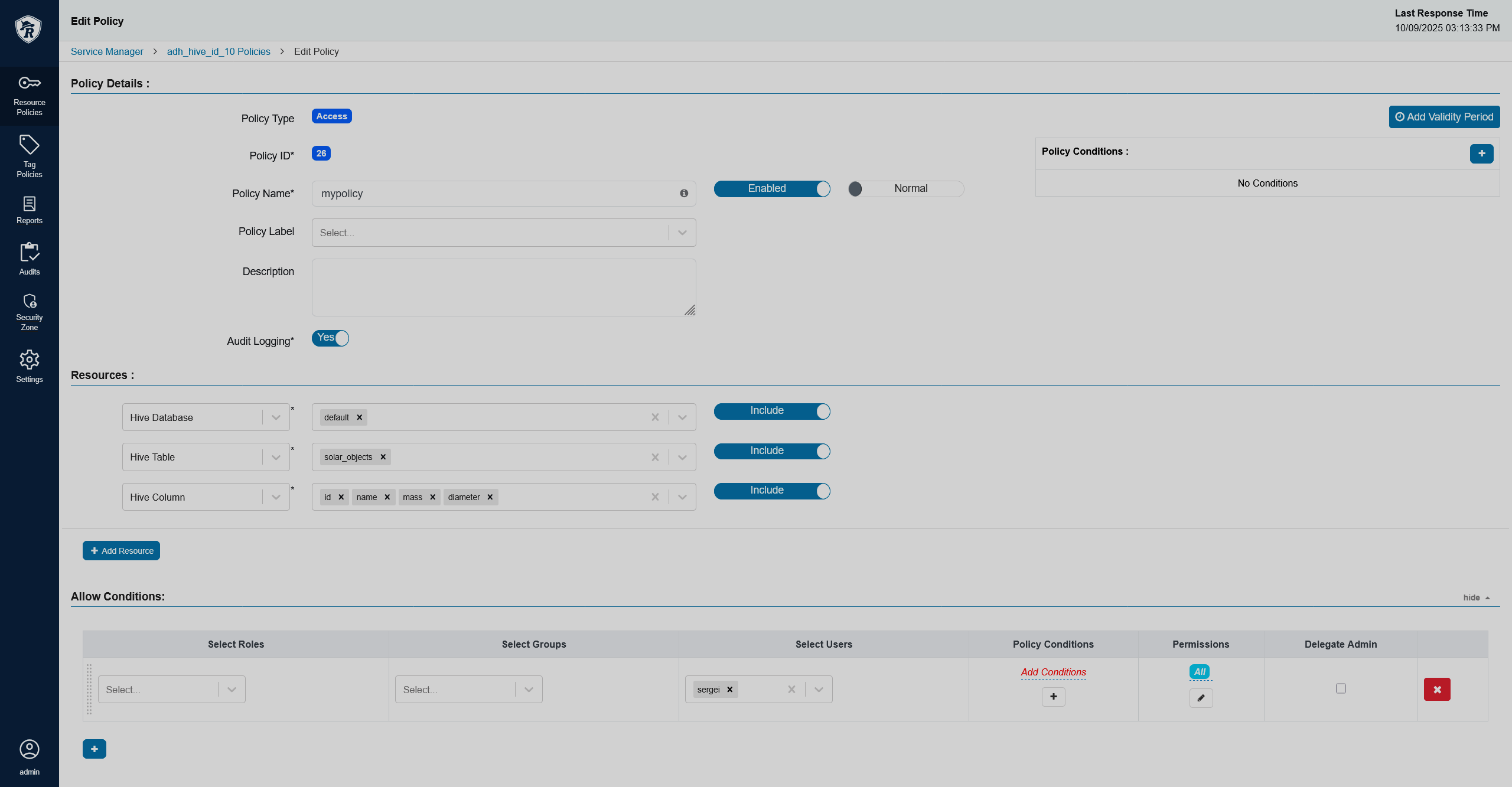 Create a Hive policy
Create a Hive policy
Check
To check that the setup works correctly, follow the steps below:
-
On an ADH cluster host, execute a query using the Trino shell:
$ trino --execute 'select * from "hive-adh"."default"."solar_objects";'The output is expected to be the table’s content:
"1","Sun","1989100000","1392000" "2","Mercury","330","4879" "3","Venus","4867","12104" "4","Earth","5972","12742" "5","Mars","642","6780" "6","Jupiter","1898187","139822" "7","Saturn","568317","116464" "8","Uranus","86813","50724" "9","Neptune","102413","49244"
-
In the Ranger Admin UI, check the Audits → Access page to see that the access was allowed and the impersonation works correctly.
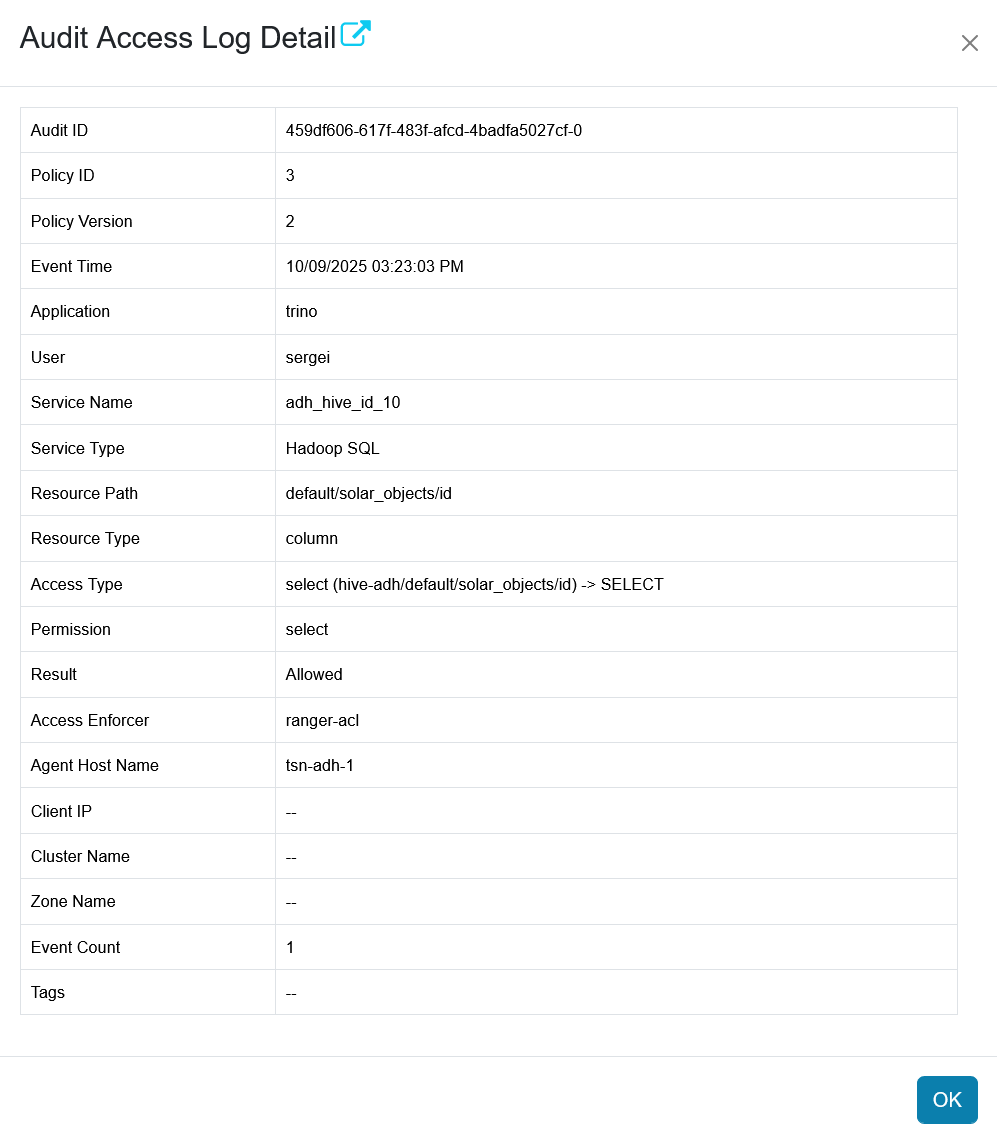 The Ranger Audits page
The Ranger Audits page The Ranger Audits page
The Ranger Audits page