

Kerberos with Samba
Overview
Samba acts as an Active Directory domain controller, so setting up Kerberos authentication with Samba is very similar to setting up authentication with MS Active Directory.
Start Kerberos Samba on an ADS cluster in the ADCM interface
-
Initiate the Kerberos Samba enablement for the selected cluster. To do this, apply the Manage Kerberos cluster action by clicking
in the Actions column.
-
Turn on the Existing Samba switch in the window that opens.
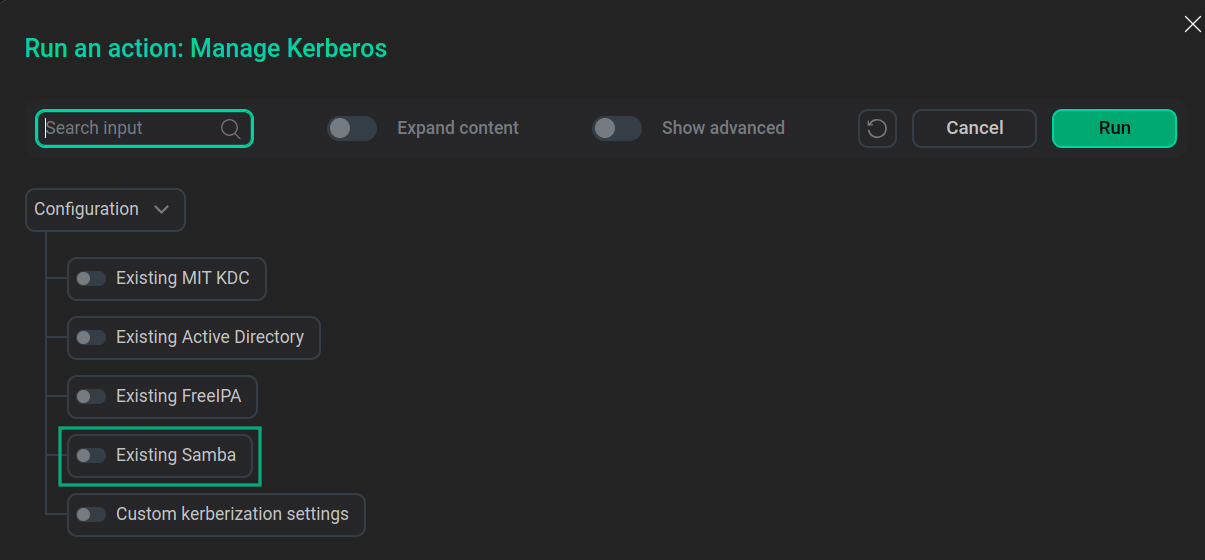 Enable Existing SambaNOTEEnabling Existing Samba can be combined with the Custom kerberization settings option.
Enable Existing SambaNOTEEnabling Existing Samba can be combined with the Custom kerberization settings option. -
Set the Show advanced switch to active.
-
Set the Samba Kerberos parameters of the ADS cluster and click Run.
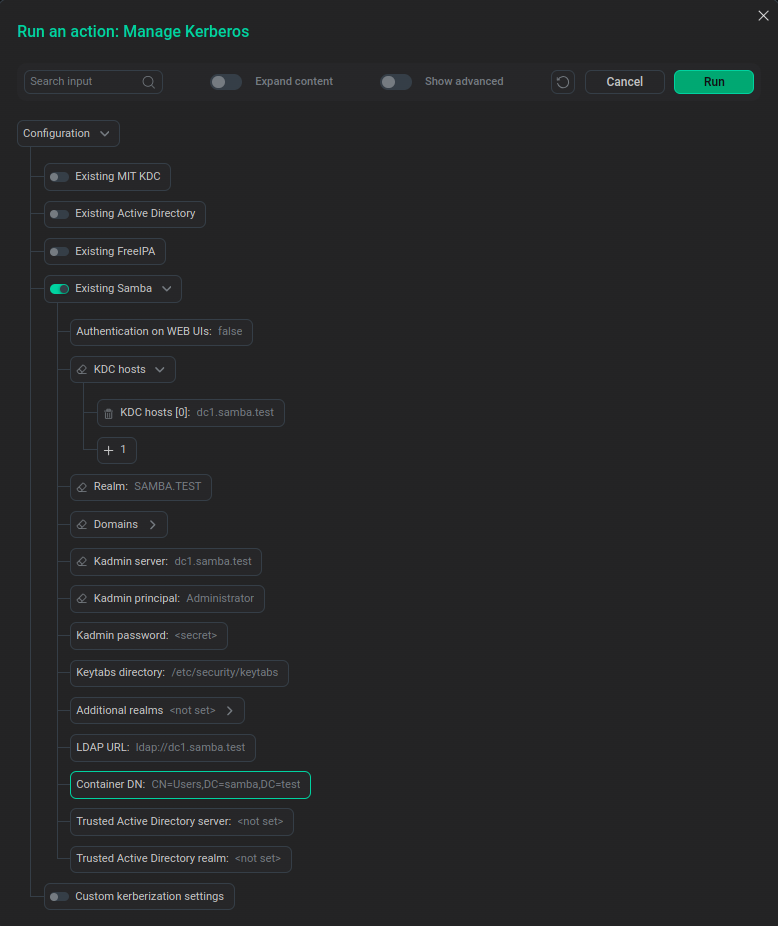 Configuring an ADS cluster for Kerberos Samba
Configuring an ADS cluster for Kerberos Samba -
Verify the action in the opened window.
 Verify the action
Verify the action -
Wait until Kerberos Samba is enabled. Analyze and correct errors if they occur.
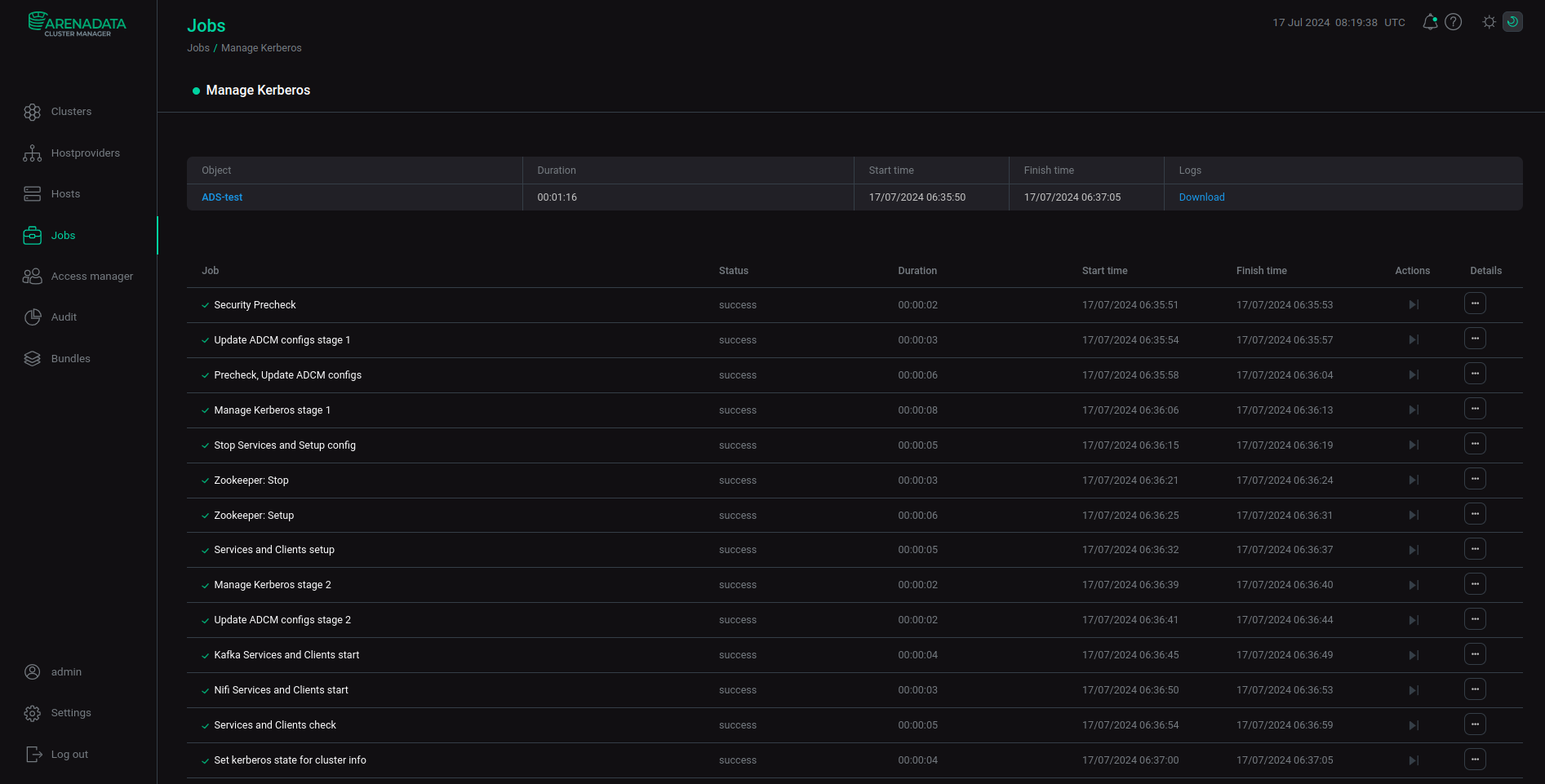 Kerberos startup process
Kerberos startup process
Samba Kerberos parameters
| Parameter | Description |
|---|---|
Authentication on WEB UIs |
Enables Kerberos authentication on Web UIs |
KDC hosts |
One or more domain controller hosts |
Realm |
Kerberos realm |
Domains |
Domains associated with hosts |
Kadmin server |
Host where |
Kadmin principal |
Principal name used to connect via |
Kadmin password |
A principal password used to connect via |
Keytabs directory |
Directory of the keytab file that contains one or several principals along with their keys |
Additional realms |
Additional Kerberos realms |
LDAP URL |
LDAP URL consists of |
Container DN |
Container distinguished name |
Trusted Active Directory server |
Trusted DC server |
Trusted Active Directory realm |
Realm for cross-realm trust |
|
NOTE
Samba-based Kerberos authentication after running Manage Kerberos in the Kafka service is done according to Use Kerberos with MS Active Directory in Kafka.
|