

Kerberos with MS Active Directory
Basic concepts used in Kerberos LDAP:
-
Active Directory — database and set of services that connect users to the necessary network resources.
-
Lightweight directory access protocol (LDAP) — application layer protocol for accessing the Active Directory directory service, used in cluster kerberization to establish user principals.
-
LDAPS — LDAP activation using SSL/TLS protocol to create secure traffic. Creating passwords for ADS users with accounts in Active Directory during cluster kerberization is only possible using LDAPS.
-
LDAP server — hierarchical database, a directory service based on Active Directory, used for centralized storage of accounts. The credentials include the principals against which the user is validated in Kerberos.
-
Key distribution center (KDC) — access control system component responsible for servicing user requests for access to resources by providing access tickets and session keys. It uses Active Directory as the account database.
-
Distinguished name (DN) is an account in Active Directory. The DN must be unique within the tree. The DN describes the content of the attributes in the tree (navigation path) for accessing a particular entry.
A DN consists of a series of relative distinguished names (RDN) determined by moving up the tree in the direction of its root entry. RDNs are written from left to right.
Prepare to run Active Directory on an ADS cluster
-
Set up an Active Directory server (LDAP server).
-
Create a user account to connect the cluster to LDAP-server using the LDAP protocol.
-
Generate a certificate for the user by enabling LDAP over SSL using a third-party CA.
-
Set a password for the account.
-
Assign a user principal name to the account, for example,
admin-kafka@AD.RANGER-TEST, and generate a keytab file with these principal and keys.
Run Active Directory on ADS cluster in the ADCM interface
-
Make sure you know the necessary data to start Active Directory:
-
KDC hosts — address of the host where Key Distribution Center is installed, for AD kerberization this address is the same as the address of the LDAP server;
-
Realm — designation of realm for authentication in Kerberos;
-
Kadmin server — server for installing the Kerberos V5 administration system, for kerberization on AD this address is the same as the address of the LDAP server;
-
Kadmin principal — designation of the user principal created to connect the cluster to Active Directory;
-
Kadmin password — password for the user principal created to connect the cluster to Active Directory;
-
Admin DN — account in Active Directory for the user used to connect the cluster to Active Directory;
-
LDAP URL — LDAP server address;
-
Container DN — distinguished name ou, which will be the default location for cluster objects created during kerberization below the user described in Admin DN;
-
TLS CA certificate Path — path to the generated CA certificate for the Admin DN user (you can leave it blank, then ADCM will contact the LDAP server);
-
TLS CA certificate (optional) — the number of the created CA certificate for the user Admin DN (it is allowed not to specify, then ADCM will contact the LDAP server)
-
-
Initiate enabling MS Active Directory for the selected cluster. To do this, apply the Manage Kerberos action by clicking on the
in the Actions column.
 Enabling Kerberos on the ADS cluster
Enabling Kerberos on the ADS cluster -
Enable Existing Active Directory. To do this, you need to enable the eponymous switch in the window that opens.
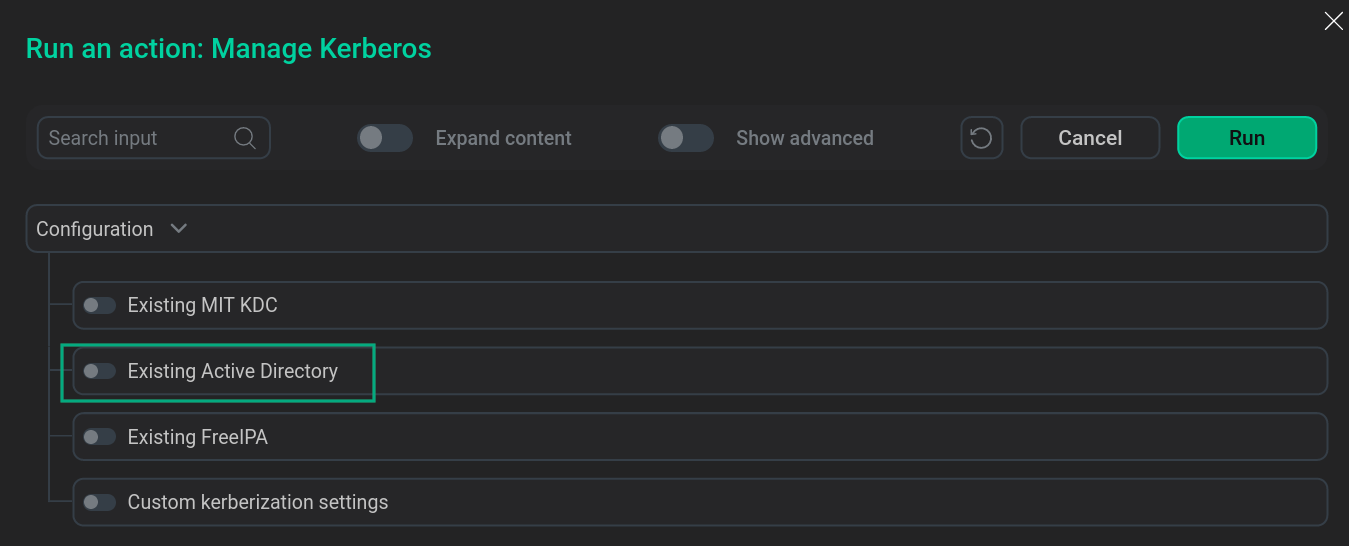 Enable Existing Active DirectoryNOTEEnabling Existing Active Directory can be combined with the Custom kerberization settings option.
Enable Existing Active DirectoryNOTEEnabling Existing Active Directory can be combined with the Custom kerberization settings option. -
Set the configuration parameters of the ADS cluster for MS Active Directory according to the values set for the user in the LDAP directory and click Run.
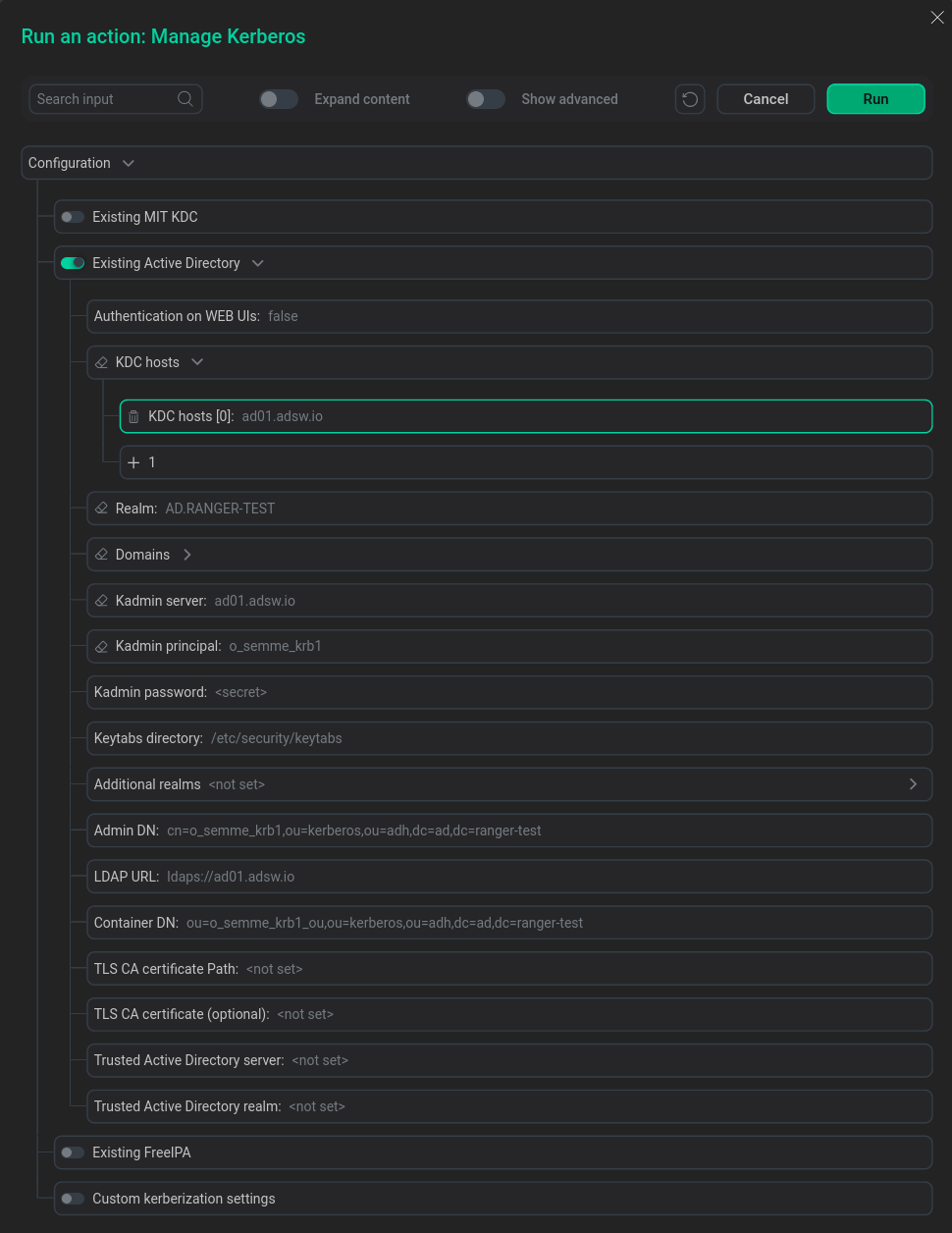 Configuring ADS Cluster for MS Active Directory
Configuring ADS Cluster for MS Active Directory -
Wait for the Kerberos LDAP enablement to complete. Analyze and correct errors if they occur.
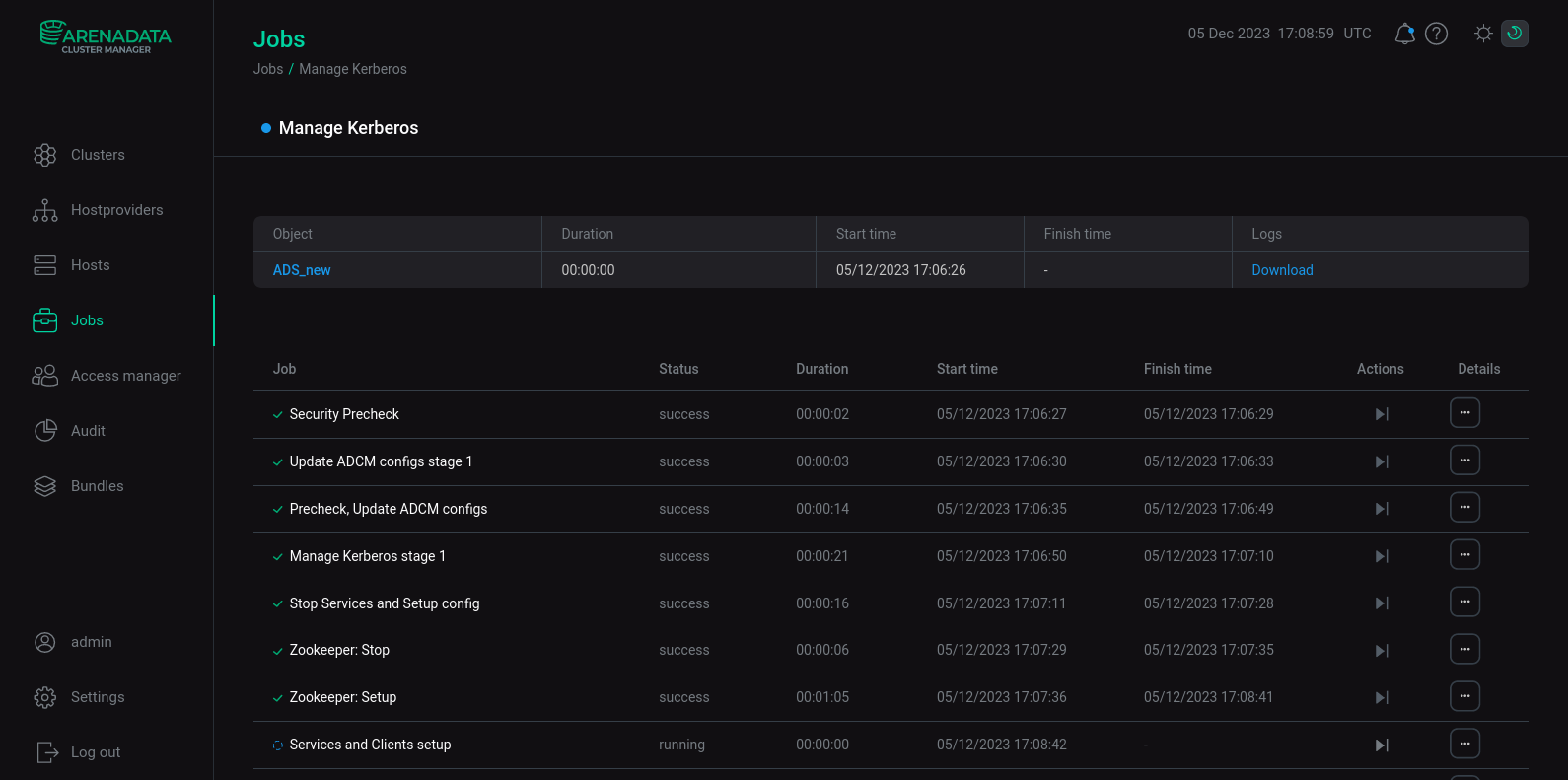 LDAP installation process
LDAP installation process
|
NOTE
LDAP authentication after running Manage Kerberos on the Kafka service is done according to Use Kerberos with MS Active Directory in Kafka.
|