

MIT Kerberos
Kerberos — network authentication protocol that provides a mechanism for mutual authentication of a client and server before establishing a connection between them.
SASL — authentication and data security framework used in Internet protocols.
Basic concepts used in Kerberos:
-
Principal — unique name for a client that is allowed to authenticate with Kerberos.
-
Ticket — temporary data issued to the client for authentication on the server where the required service is located.
-
Realm — network used by Kerberos, consisting of KDC servers and multiple clients.
-
Key distribution center (KDC) — service that issues Kerberos tickets.
Configure KDC
|
NOTE
|
To install the KDC, run the following command on the selected host:
$ sudo yum install -y krb5-serverThe result is a message:
Complete!
Set up configuration files
|
NOTE
|
-
The configuration file kdc.conf needs to be configured. It displays the name of the realm in which authentication is performed and the path to the configuration files.
Enter the command to open the file:
$ sudo vim /var/kerberos/krb5kdc/kdc.confEdit the opened file as follows:
[kdcdefaults] kdc_ports = 88 kdc_tcp_ports = 88 default_realm = ADS-KAFKA.LOCAL [realms] ADS-KAFKA.LOCAL = { acl_file = /var/kerberos/krb5kdc/kadm5.acl dict_file = /usr/share/dict/words admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal }This file contains the sections described below:
[kdcdefaults]
The section specifies the default values for the tags to be used if the[realms]section does not contain a value for that tag.Tag Tag description kdc_ports
UDP port for connecting to KDC
kdc_tcp_ports
TCP port for connecting to KDC
default_realm
Area designated by the user for authentication
[realms]
Every subsection in the section is the name of a Kerberos realm. The meaning of the subsection tags determines the KDC settings for that particular realm.Tag Tag description acl_file
Location of the ACL file that kadmind uses to determine which principals are granted which permissions in the Kerberos database
admin_keytab
Location of the keytab file that the kadmind4 and v5passwdd administrative services use to authenticate against the database
dict_file
Location of a dictionary file containing strings that cannot be used as passwords. The file must contain one line per line without any extra spaces. If nothing is specified, or if no policy is assigned to the principal, no dictionary password checks will be performed
supported_enctypes
Specifies the default key/salt encryption type combinations for principals for this realm. All members created with kadmin will have keys of these types
NOTEA complete description of the tag values for this file can be found at kdc.conf. -
Next, you need to edit the kadm5.acl file to provide administrative access to the Kerberos domain.
Enter the command to open the file:
$ sudo vim /var/kerberos/krb5kdc/kadm5.aclEdit the opened file as follows:
*/admin@ADS-KAFKA.LOCAL *
The example above is configured so that any
/adminprincipal in theADS-KAFKA.LOCALrealm has all administrative privileges except key extraction.NOTEFor a complete description of the tag values for sections of this file, see kadm5_acl. -
Next, you need to edit the Kerberos domain configuration file krb5.conf.
Enter the command to open the file:
$ sudo vim /etc/krb5.confEdit the opened file as follows:
[logging] default = FILE:/var/log/krb5libs.log kdc = FILE:/var/log/krb5kdc.log admin_server = FILE:/var/log/kadmind.log [libdefaults] default_realm = ADS-KAFKA.LOCAL kdc_timesync = 1 ticket_lifetime = 24h [realms] ADS-KAFKA.LOCAL = { admin_server = sov-ads-test-0.ru-central1.internal kdc = sov-ads-test-0.ru-central1.internal }This file contains the sections described below:
[logging]
The section specifies how the logs are kept.Tag Tag description default
Path to the file where the log is located, unless otherwise specified
kdc
Path to the file where the KDC log is located
admin_server
Path to the file where the log for the administrative server is located
[libdefaults]
This section describes the parameters used by the Kerberos V5 library.Tag Tag description default_realm
Identifies the default Kerberos realm for the client. Set its value to your Kerberos realm. If this value is not set, then when calling programs such as kinit, you must specify a realm for each Kerberos principal
kdc_timesync
Valid values for this ratio are
1or0. If it is non-zero, client machines will calculate the difference between their own time and the time returned by the KDC in ticket timestamps, and use this value to correct inaccurate system clocks when requestedticket_lifetime
Sets the default time to live for initial ticket requests
[realms]
Every subsection in the section is the name of a Kerberos realm. The meaning of subsection tags determines the settings for that particular area.Tag Tag description ADS-KAFKA.LOCAL
Area designated by the user for authentication
admin_server
Identifies the host on which the administration server is running. Typically, this is the main Kerberos server. This tag must be set to a value to communicate with the kadmind server for this realm
kdc
Name or address of the host running the KDC for this realm. An optional port number can be included, separated from the hostname by a colon
NOTEFor a complete description of the tag values for the areas of this file, see krb5_conf. -
Create a database of Kerberos principals for realm domain
ADS-KAFKA.LOCALusing the kdb5_util utility.Enter command:
$ sudo /usr/sbin/kdb5_util create -s -r ADS-KAFKA.LOCAL -P P@ssw0rdAs a result, a message is displayed about the created database for the
ADS-KAFKA.LOCALarea:Loading random data Initializing database '/var/kerberos/krb5kdc/principal' for realm 'ADS-KAFKA.LOCAL', master key name 'K/M@ADS-KAFKA.LOCAL'
NOTEA complete description of the functions of the kdb5_util utility and applicable options is available at kdb5_util. -
Create user
adminusing command line interface kadmin.local.Enter command:
$ sudo kadmin.local -q "add_principal -pw P@ssw0rd admin/admin"As a result, a message is displayed:
Principal "admin/admin@ADS-KAFKA.LOCAL" created.
NOTEFor a complete description of the kadmin_local command line interface functions and applicable options, see kadmin_local. -
Restart Kerberos and KDC services.
Enter the commands one by one:
$ sudo systemctl restart krb5kdc $ sudo systemctl restart kadminCheck the status of running services by running the commands:
$ sudo systemctl status krb5kdc $ sudo systemctl status kadmin
Configure a custom jaas.conf
Before starting Manage Kerberos, the user file jaas.conf can be configured to specify user data for connecting other service clients to the current service (paths to keytab files, the useTicketCache parameter, and others).
The table below shows a list of services for which a custom jaas.conf file can be configured and the file storage paths for each service.
| Service | Path to jaas.conf |
|---|---|
Kafka |
/etc/kafka/conf/kafka-jaas.conf |
Kafka Connect |
/etc/kafka-connect/jaas_config.conf |
Kafka REST Proxy |
/etc/kafka-rest/jaas_config.conf |
Schema-Registry |
/etc/schema-registry/jaas_config.conf |
ksqlDB |
/etc/ksqldb/jaas_config.conf |
Kafka REST Proxy |
/etc/kafka-rest/jaas_config.conf |
NiFi |
/etc/nifi/conf/nifi-jaas.conf |
The custom jaas.conf file is configured using a special JAAS template on the configuration page of the service. The configuration can be performed both for an individual service and for host groups on which the service is installed.
To configure jaas.conf:
-
Turn on the Show advanced switch.
-
Open the template, make changes and save by clicking Apply.
To configure user data when enabling authentication via the Kerberos protocol, only those JAAS template template blocks that describe the configuration for the Krb5LoginModule module are filled.
Below is an example of a JAAS file template for the Kafka service and a brief description of the blocks to be filled.
JAAS file for Kafka{% if cluster.config.kerberos_client and cluster.config.kerberos_client.enable_kerberos %} Client { com.sun.security.auth.module.Krb5LoginModule required useKeyTab=true storeKey=true useTicketCache=false keyTab="{{ cluster.config.kerberos_client.keytab_dir }}/kafka.service.keytab" principal="kafka/{{ ansible_fqdn }}@{{ cluster.config.kerberos_client.realm }}"; }; KafkaClient { com.sun.security.auth.module.Krb5LoginModule required useKeyTab=true storeKey=true useTicketCache=false keyTab="{{ cluster.config.kerberos_client.keytab_dir }}/kafka.service.keytab" principal="kafka/{{ ansible_fqdn }}@{{ cluster.config.kerberos_client.realm }}"; }; KafkaServer { com.sun.security.auth.module.Krb5LoginModule required useKeyTab=true storeKey=true useTicketCache=false serviceName="kafka" keyTab="{{ cluster.config.kerberos_client.keytab_dir }}/kafka.service.keytab" principal="kafka/{{ ansible_fqdn }}@{{ cluster.config.kerberos_client.realm }}"; }; {%- elif cluster.config.sasl_plain_auth_default_config is not none %} {%- set credential = cluster.config.sasl_plain_auth_default_config.sasl_plain_users_data %} KafkaServer { org.apache.kafka.common.security.plain.PlainLoginModule required username="kafka" password="{{ credential['kafka'] }}" {% for user, password in credential.items() %} user_{{ user }}="{{ password }}"{% if loop.index != loop | length %} {% endif %} {% endfor %}; }; {% endif %}-
Client— describes configuration parameters for connecting other services (for example, Zookeeper) to Kafka brokers. -
KafkaClient— describes configuration parameters for connecting external applications (producers and consumers) to Kafka brokers -
KafkaServer— describes the configuration parameters for communication between Kafka brokers.
-
-
Save the configuration by clicking Save.
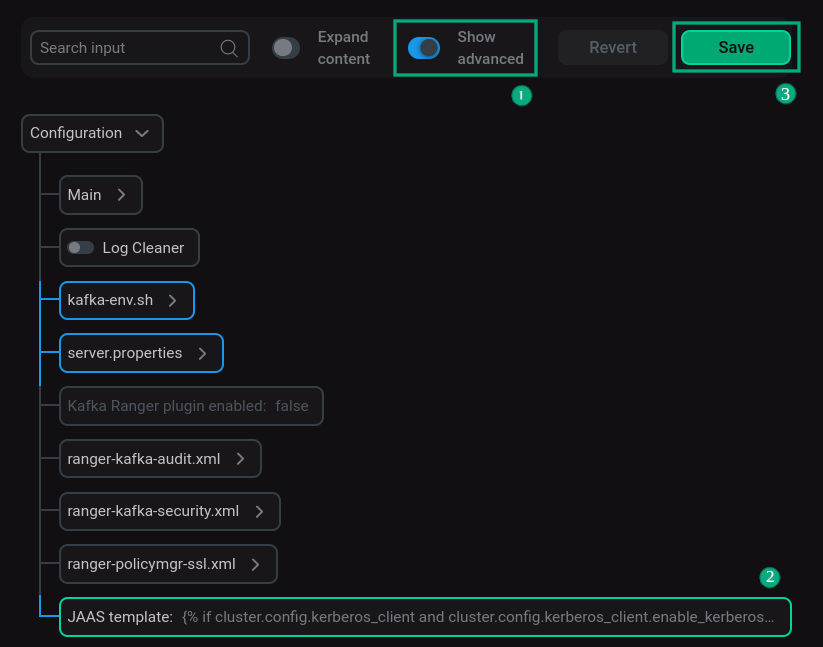 Setting up JAAS template
Setting up JAAS template -
Reload the services for which jaas.conf was configured. To do this, apply the Restart action by clicking
in the Actions column.
|
NOTE
In the case when the JAAS template is not changed before enabling Manage Kerberos, after enabling kerberization on hosts, jaas.conf files are created by default for each service with the data given in the template.
|
Start MIT Kerberos KDC on ADS cluster in ADCM interface
-
Initiate Kerberos enablement for the selected cluster. To do this, apply the Manage Kerberos action by clicking
in the Actions column.
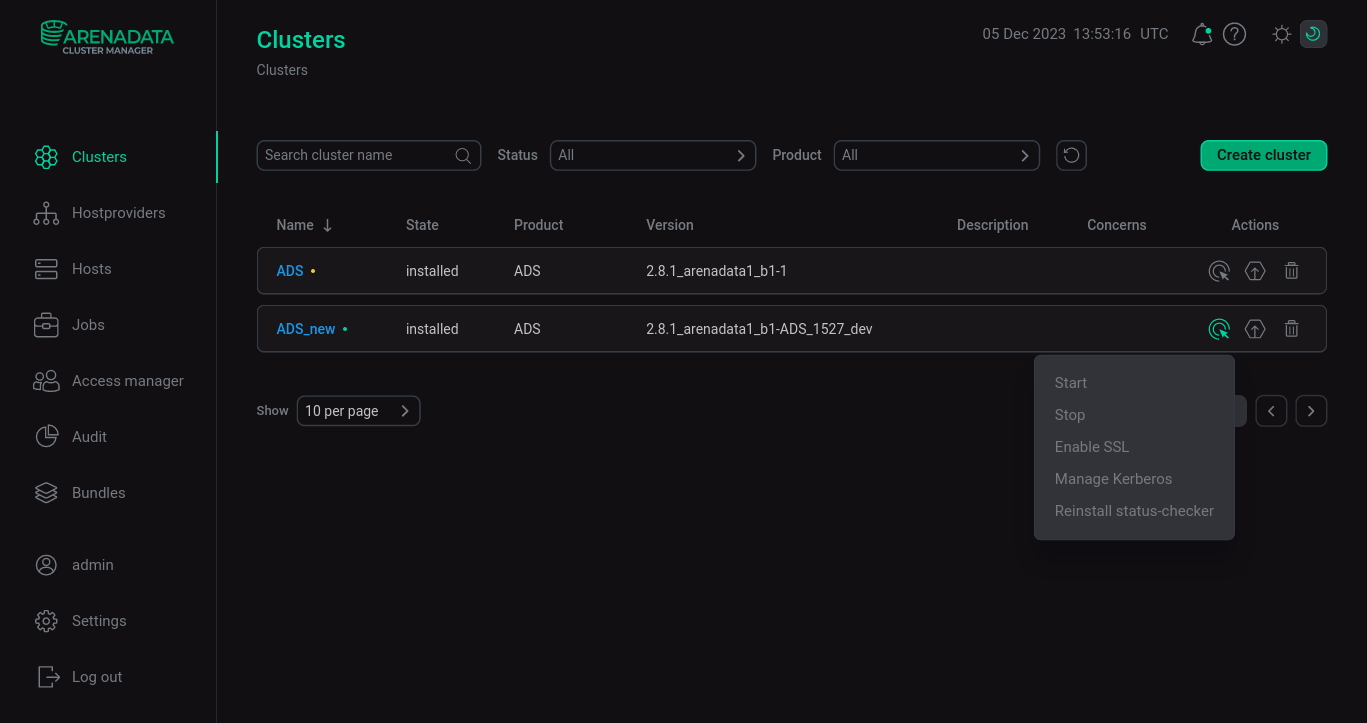 Enabling Kerberos on the ADS cluster
Enabling Kerberos on the ADS cluster -
Enable Existing MIT KDC. To do this, you need to enable the eponymous switch in the window that opens.
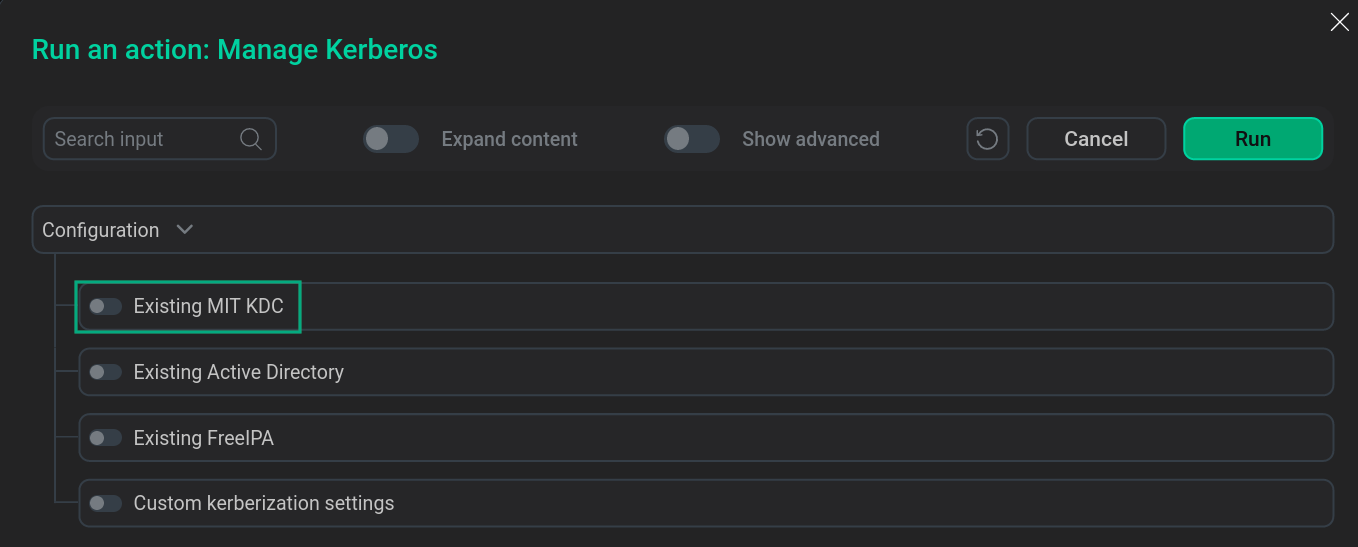 Enabling Existing MIT KDCNOTEEnabling Existing MIT KDC can be combined with the Custom kerberization settings option.
Enabling Existing MIT KDCNOTEEnabling Existing MIT KDC can be combined with the Custom kerberization settings option. -
Set the Show advanced switch to active.
-
Set the configuration parameters of the ADS cluster for MIT Kerberos KDC in accordance with the previously entered values and click Run.
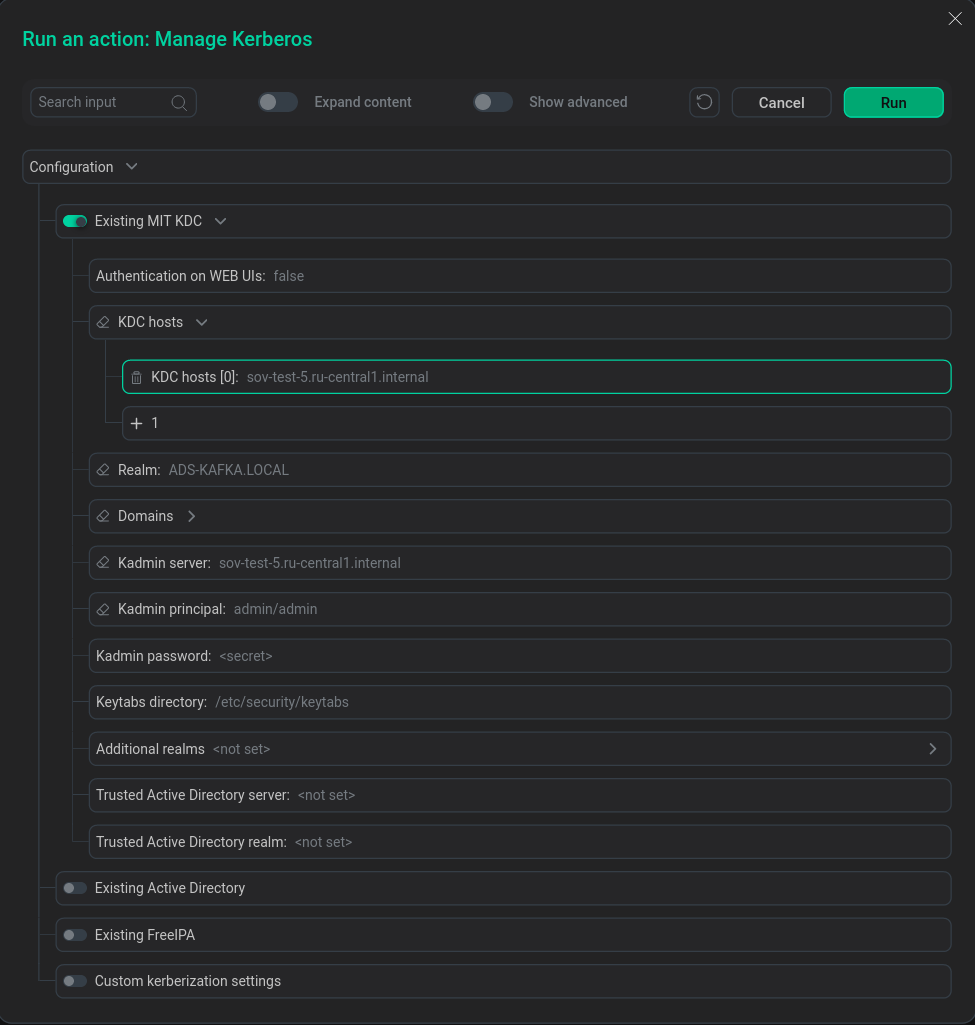 Configuring ADS cluster for MIT Kerberos KDC
Configuring ADS cluster for MIT Kerberos KDC -
Wait for the Kerberos setup to complete. Analyze and correct errors if they occur.
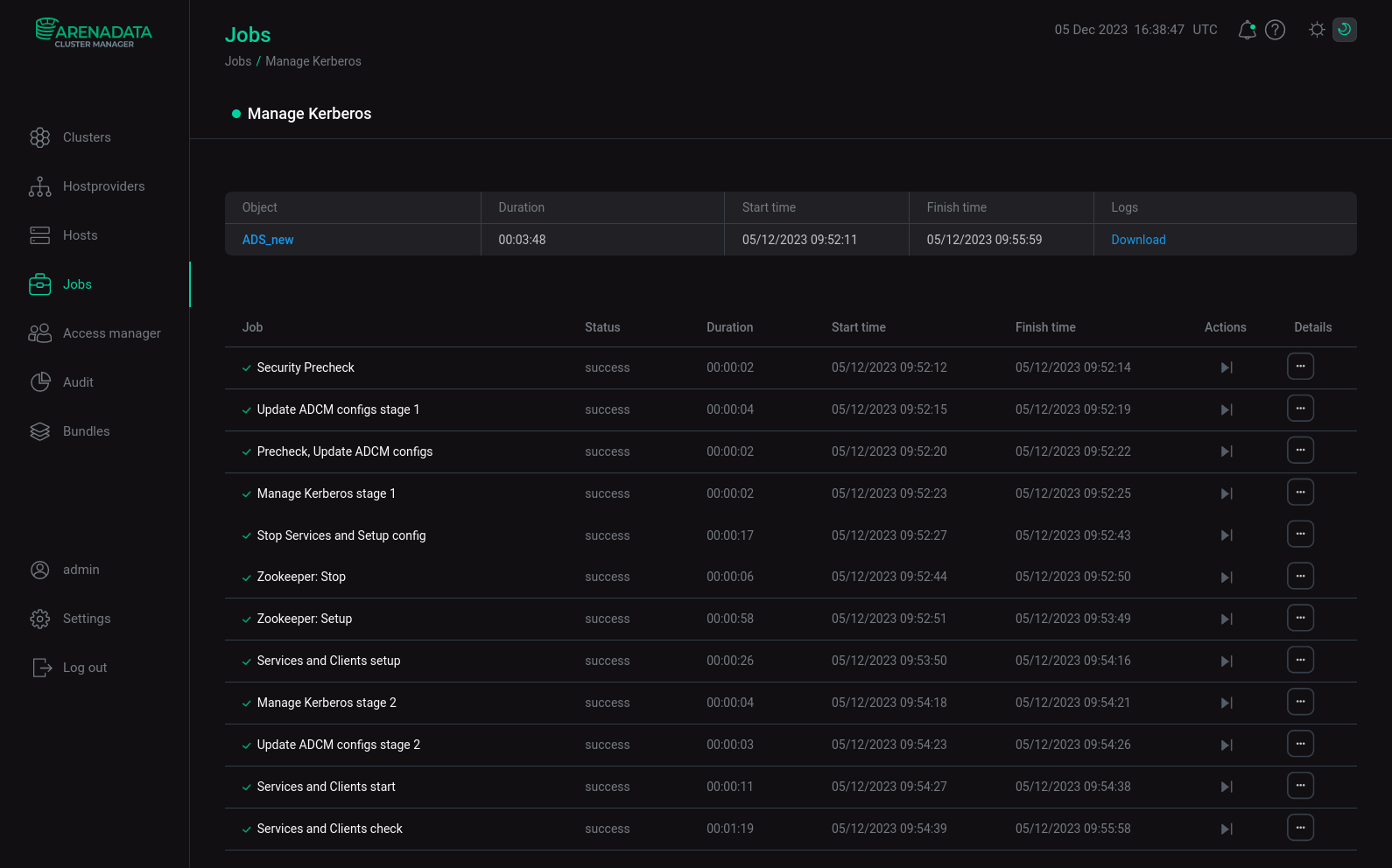 Kerberos installation process
Kerberos installation process
|
NOTE
Kerberos authentication after running Manage Kerberos in Kafka service is done according to Use MIT Kerberos in Kafka.
|