

Encryption of NiFi configuration parameters
Main information about encryption
Once the NiFi service is installed, all sensitive plaintext values for the NiFi Server and NiFi Registry components are replaced with encrypted values in the following configuration files:
-
nifi.properties
-
authorizers.xml
-
login-identity-providers.xml
-
nifi-registry.properties
Encryption is performed automatically by ADCM using the encrypt-config tool, which reads plaintext-sensitive configuration values from files, queries the root key, and encrypts each value (replaces plain values with a protected value in the same file).
The default encryption algorithm used is 128/256-bit AES/GCM.
The root key is generated from the password specified in the Nifi config encryption password configuration parameter and written to the bootstrap.conf file by the encryption command to save and provide security scheme configuration when needed.
The bootstrap.conf file should only be granted read permissions to the user who can execute it (user nifi, user in the nifi group, or root).
Encrypt new data when using the service
Encryption for the NiFi service is supported for the following operations:
-
Enable authentication and authorization using UI or Ranger plugin — in this case, all new confidential data is written to configuration files in the encrypted form.
-
Enable the Expand action — this uses the existing password to encrypt sensitive data in configuration files on the new host (or multiple hosts).
Change a password
If you need to change a password, do the following:
-
On the configuration page of the NiFi service, for the Nifi config encryption password parameter enter a new password and save the configuration by clicking Save.
CAUTIONThe password must be at least 12 characters long and can contain letters, numbers, and punctuation.
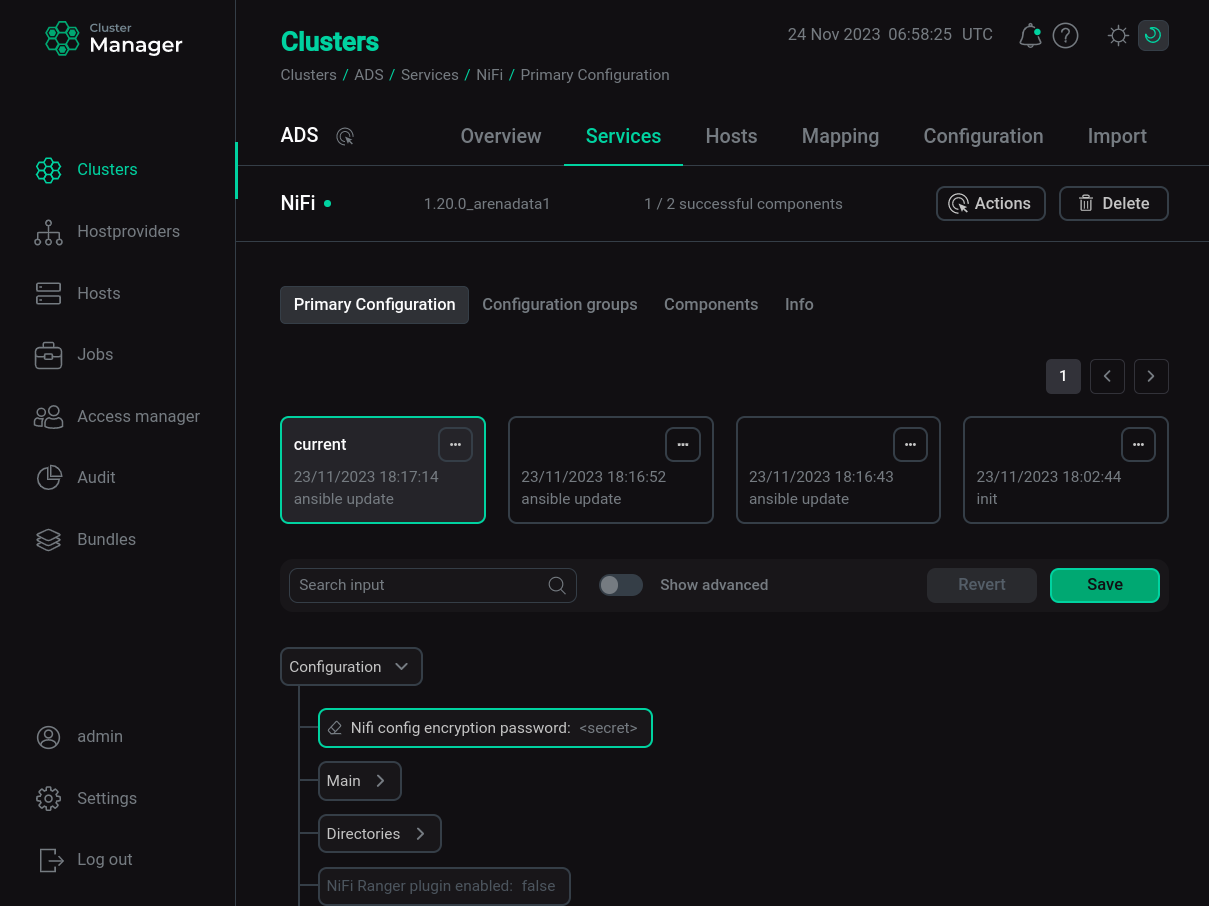 Changing the encryption password for NiFi configuration parameters
Changing the encryption password for NiFi configuration parameters -
Restart the NiFi service. To do this, apply the action Restart by clicking on the
in the Actions column.
Encrypted sensitive data in NiFi configuration files
The table below shows which parameters in NiFi configuration files are encrypted.
|
CAUTION
The parameter table is for informational purposes only. It is not recommended to make changes to configuration files. |
| Component | Configuration file | Parameter | Default value | Encrypted |
|---|---|---|---|---|
NiFi Server |
nifi.properties |
nifi.sensitive.props.key |
mysensetivekey |
+ |
nifi.security.keystorePasswd |
— |
+ |
||
nifi.security.keyPasswd |
— |
+ |
||
nifi.security.truststorePasswd |
— |
+ |
||
nifi_cli.properties |
keystorePasswd |
— |
— |
|
keyPasswd |
— |
— |
||
truststorePasswd |
— |
— |
||
login-identity-providers.xml |
Manager Password |
— |
+ |
|
TLS - Keystore Password |
— |
+ |
||
TLS - Truststore Password |
— |
+ |
||
authorizers.xml |
Manager Password |
— |
+ |
|
TLS - Keystore Password |
— |
+ |
||
TLS - Truststore Password |
— |
+ |
||
NiFi Registry |
nifi-registry.properties |
nifi.registry.security.keystorePasswd |
— |
+ |
nifi.registry.security.keyPasswd |
— |
+ |
||
nifi.security.truststorePasswd |
— |
+ |
||
nifi.registry.db.password |
nifireg |
+ |