

SSL channel security in Kafka
|
NOTE
Enabling SSL channel security is carried out in accordance with the article SSL channel security.
|
Check the installed SSL
-
Verify that the listeners parameter in the Kafka service settings changed from
SASL_PLAINTEXT://:9092toSASL_SSL://:9092.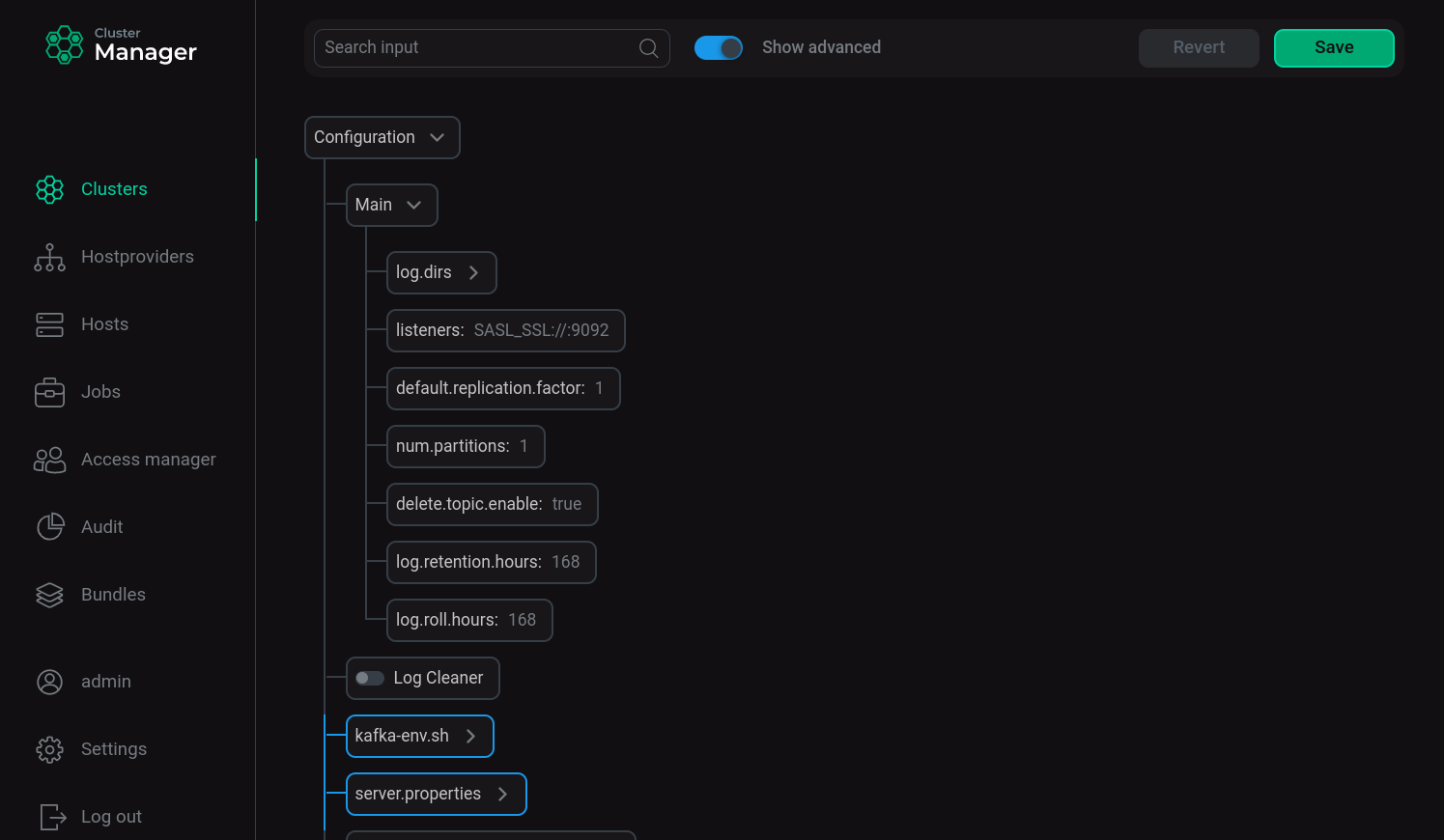 Kafka service settings
Kafka service settings -
Check for a change in the server.properties file on each Kafka server.
Open file server.properties:
$ sudo vim /usr/lib/kafka/config/server.properties -
Make sure that for each Kafka broker the line defining the security protocol is changed to
SASL_SSLand there are lines defining the server RSA keystores and passwords for them:
security.inter.broker.protocol=SASL_SSL ... ... ... ssl.keystore.location=/tmp/keystore.jks ssl.keystore.password=bigdata ssl.key.password=bigdata ssl.keystore.type=JKS ssl.truststore.location=/tmp/truststore.jks ssl.truststore.password=bigdata ssl.truststore.type=JKS
Connect to Kafka (create tickets) and work with .sh files (scripts) with participation of different users after installing SSL
-
To create a configuration file .properties for a user with SSL in mind, run the command:
$ sudo vim /tmp/client_ssl.propertiesFill the file with data:
security.protocol=SASL_SSL sasl.mechanism=GSSAPI sasl.kerberos.service.name=kafka
-
Follow the steps to connect to Kafka as user
writerfrom the article Use MIT Kerberos in Kafka:-
Open terminal session 1 and connect to one of the Kafka brokers.
-
Create a ticket for user
writer. -
Check ticket.
-
Export the client.jaas file as a JVM option for the given user using the
KAFKA_OPTSenvironment variable.
-
-
Create a topic by specifying the path to the created client_ssl.properties file:
$ /usr/lib/kafka/bin/kafka-topics.sh --create --topic test-topic1 --bootstrap-server sov-ads-test-1.ru-central1.internal:9092,sov-ads-test-2.ru-central1.internal:9092,sov-ads-test-3.ru-central1.internal:9092 --command-config /tmp/client_ssl.propertiesNOTEThe client.jaas file does not need to be changed after installing SSL. -
Write a message to a topic:
$ /usr/lib/kafka/bin/kafka-console-producer.sh --topic test-topic1 --bootstrap-server sov-ads-test-1.ru-central1.internal:9092,sov-ads-test-2.ru-central1.internal:9092,sov-ads-test-3.ru-central1.internal:9092 --producer.config /tmp/client_ssl.properties -
Follow the steps to connect to Kafka as the user
readerfrom the article Use MIT Kerberos in Kafka:-
Open terminal session 2 and connect to one of the Kafka brokers.
-
Create a ticket for user
reader. -
Check ticket.
-
Export the generated client.jaas file as a JVM option for the given user using the
KAFKA_OPTSenvironment variable.
-
-
Read messages from a topic by specifying the path to the created client_ssl.properties file:
$ /usr/lib/kafka/bin/kafka-console-consumer.sh --topic test-topic1 --from-beginning --bootstrap-server sov-ads-test-1.ru-central1.internal:9092,sov -ads-test-2.ru-central1.internal:9092,sov-ads-test-3.ru-central1.internal:9092 --consumer.config /tmp/client_ssl.propertiesMake sure messages are read correctly.