

Configure a cluster
|
IMPORTANT
There is usually no need to change cluster configuration parameters. You can leave all parameters at the default values.
|
After creation a new cluster, you can configure it by performing the following steps:
-
Select a cluster on the Clusters page. To do this, click a cluster name in the Name column.
 Select a cluster
Select a cluster -
Open the Configuration tab on the cluster page. The Configuration tab includes the following sections: Primary configuration, Configuration groups, Ansible settings.
-
Fill in all necessary parameters on the selected tab and click Save.
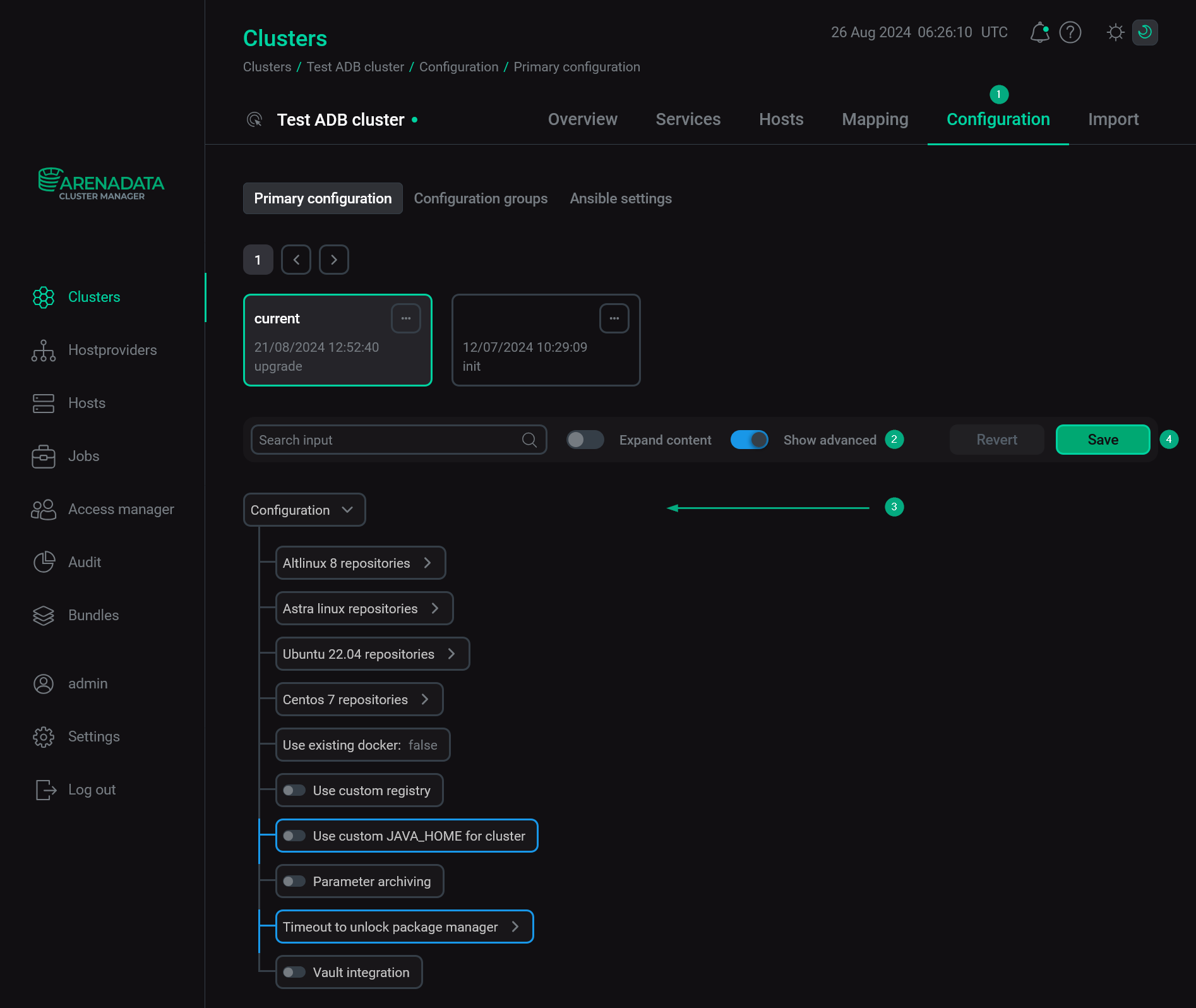
Primary configuration
The Configuration → Primary configuration tab allows you to configure the general cluster settings.
|
CAUTION
Use all custom installations (Use existing docker, Use custom registry, Use custom JAVA_HOME for cluster) on your own risk. |
Available configuration parameters are listed below:
-
Cluster UUID — the unique cluster identifier, which is generated automatically during ADB installation.
-
Timeout to unlock package manager — parameters of this section are intended to set the timeout of the DNF software package manager unlocking wait. In Ubuntu, after the host reboot, automatic update starts, which locks DNF.
Name Description Default retries
The maximum number of retries
3
delay
The time delay between retries (in seconds)
10
-
Paths to the repositories that are used during the installation process depending on the cluster operating system (AltLinux, Astra Linux, RED OS, and Ubuntu). Only the marked repositories are registered on the cluster hosts.
Altlinux 10 repositoriesParameter Description Set up Arenadata repo
Whether or not to use the repository that is described in the field Arenadata repo url
Arenadata repo url
The repository that is required to install ADB
Set up custom Arenadata enterprise repo
Whether or not to use the repository that is described in the field Custom Arenadata enterprise repo
Custom Arenadata enterprise repo
Custom Arenadata Enterprise repository. If not filled in, the default repository will be used
Set up ADB monitoring repo
Whether or not to use the repository that is described in the field prometheus_repo (for future use)
prometheus_repo
The repository that is required to install monitoring (for future use)
Astra linux repositoriesParameter Description Set up Arenadata repo
Whether or not to use the repository that is described in the field Arenadata repo url
Arenadata repo url
The repository that is required to install ADB
Set up custom Arenadata enterprise repo
Whether or not to use the repository that is described in the field Custom Arenadata enterprise repo
Custom Arenadata enterprise repo
Custom Arenadata Enterprise repository. If not filled in, the default repository will be used
Set up ADB monitoring repo
Whether or not to use the repository that is described in the field prometheus_repo (for future use)
prometheus_repo
The repository that is required to install monitoring (for future use)
redos 7 repositoriesParameter Description Set up Arenadata repo
Whether or not to use the repository that is described in the field Arenadata repo url
Arenadata repo url
The repository that is required to install ADB
Set up custom Arenadata enterprise repo
Whether or not to use the repository that is described in the field Custom Arenadata enterprise repo
Custom Arenadata enterprise repo
Custom Arenadata Enterprise repository. If not filled in, the default repository will be used
Set up ADB monitoring repo
Whether or not to use the repository that is described in the field prometheus_repo (for future use)
prometheus_repo
The repository that is required to install monitoring (for future use)
Ubuntu 22.04 repositoriesParameter Description Set up Arenadata repo
Whether or not to use the repository that is described in the field Arenadata repo url
Arenadata repo url
The repository that is required to install ADB
Set up custom Arenadata enterprise repo
Whether or not to use the repository that is described in the field Custom Arenadata enterprise repo
Custom Arenadata enterprise repo
Custom Arenadata Enterprise repository. If not filled in, the default repository will be used
Set up ADB monitoring repo
Whether or not to use the repository that is described in the field prometheus_repo (for future use)
prometheus_repo
The repository that is required to install monitoring (for future use)
-
Use existing docker — a flag that indicates whether to use the existing Docker during the installation of ADB services (e.g. ADB Control, ADBM, Monitoring, Enterprise Tools). If this flag is set, only containers will be deployed, while Docker and Docker Compose installation will be skipped. For more information on Docker requirements, see Software requirements.
IMPORTANTStarting with ADB 6.27.1.56, ADB Control rewrites Docker settings in the /etc/docker/daemon.json file for security purposes. Thus, if you need to modify this file, set the Use existing docker option when configuring ADB. This option will also allow you to use Docker in the rootless mode.
-
Use custom registry — a switcher that determines whether to use a custom registry. When the switcher is activated, the following parameters are available.
Parameter Description registry
A custom registry URL in the following form:
<host>:<port>prefix
An optional subdirectory name that will be added to the custom registry URL:
<registry>/<prefix>Use self-signed certificate
Whether or not to use a self-signed certificate
Self-signed certificate
A self-signed certificate text
-
Use custom JAVA_HOME for cluster — a switcher that indicates whether to use a custom Java path for ADB services (e.g. PXF, ADB Control, ADBM). Displayed if the Show advanced flag is set. When the switcher is activated, the JAVA_HOME field becomes available. Enter a work Java path in that field. The selected path should contain а bin folder with a Java binary file, for example /usr/lib/jvm/java-17-openjdk-amd64. Installation will fail if there is no Java at the specified path. For more information on Java requirements, see Software requirements.
If the JAVA_HOME value is empty, one of the following default paths is used (depending on the operating system).
|
IMPORTANT
|
-
Parameter archiving — a switcher that indicates whether to export ADB settings according to the specified schedule. When the switcher is activated, the Parameter archiving job setting field becomes available. Enter a schedule for an export job in that field. The field value should be a valid
cronexpression. After you edit and save the Parameter archiving job setting value, run the cluster action Reconfigure parameter archiving.Each time a
cronjob is run, ADB settings are exported to the following directory:/home/gpadmin/arenadata_configs/settings/<timestamp>
where
<timestamp>is a timestamp of the export job launch in theYYYY-MM-DD_HH-mm-ssformat.A job execution log is saved to the parameter_archiving.log file.
Currently, the following settings are offloaded.
| Service | Exported parameters | Relative path |
|---|---|---|
ADB |
GUC values for coordinator/segment |
./<YYYY-MM-DD_HH-mm-ss>_guc_config.json |
Linux Greenplum-related parameters that are exported from /etc/sysctl.conf |
./<YYYY-MM-DD_HH-mm-ss>_os_config.json |
|
Resource group parameters |
./<YYYY-MM-DD_HH-mm-ss>_rg_config.json |
|
ADB Control |
Configuration parameters of ADB Control components |
./adcc/* |
ADBM |
Configuration parameters of ADBM components |
./adbm/* |
PXF |
PXF settings that are exported from:
|
./pxf_config/* |
-
Vault integration — a switcher that indicates whether to use HashiCorp Vault to store secrets of ADB services. When the switcher is activated, the following parameters become available.
Name Description Default Address of the Vault server
The Vault server address (e.g.
192.168.1.120orvault.domain.com)—
Port of the Vault server
The Vault server port. Should be specified if the service is published on a port other than HTTPS (443)
443
Internal CA certificate in PEM format (optional)
The internal CA certificate in PEM format that signed the Vault server’s certificate
—
Use PEM CA for vault
Defines whether to use the CA certificate in PEM format. If you set this parameter to
true, you also need to fill in Internal CA certificate in PEM format (optional).To hide the truststore password in Vault, set Use PEM CA for vault to
truefalse
Vault namespace (optional)
The Vault namespace
—
Writer authentication method for the Vault server
The authentication method that is used to connect to the Vault server with write access.
Possible values:
-
token -
approle
approle
Writer Vault token
The application token that is used to connect to the Vault server with write access. Required only if the Writer authentication method for the Vault server parameter is set to
token—
Writer Vault role ID
The role identifier provided for applications to connect to the Vault server with write access. Required only if the Writer authentication method for the Vault server parameter is set to
approle—
Writer Vault secret ID
The secret identifier associated with the Writer Vault role ID role that is used by applications to connect to the Vault server with write access. Required only if the Writer authentication method for the Vault server parameter is set to
approle—
Reader authentication method for the Vault server
The authentication method that is used to connect to the Vault server with read access.
Possible values:
-
token -
approle
approle
Reader Vault token
The application token that is used to connect to the Vault server with read access. Required only if the Reader authentication method for the Vault server parameter is set to
token—
Reader Vault role ID
The role identifier provided for applications to connect to the Vault server with read access. Required only if the Reader authentication method for the Vault server parameter is set to
approle—
Reader Vault secret ID
The secret identifier associated with the Reader Vault role ID role that is used by applications to connect to the Vault server with read access. Required only if the Reader authentication method for the Vault server parameter is set to
approle—
Mount point for ADB cluster secrets
A mount point that is accessible for read/write operations with the provided ADB cluster authentication parameters. Each service will store secrets on the Vault server at the following path: <Mount point for ADB cluster secrets>/adb/<cluster_name>/service/<service_name>/<component>
—
Login mount point
A custom authentication mount point. If empty, equals to the authentication method selected in the Writer authentication method for the Vault server (write) or Reader authentication method for the Vault server (read) field
—
-
|
IMPORTANT
|
Configuration groups
The Configuration → Configuration groups tab is designed to set cluster configuration groups.
Ansible settings
The Configuration → Ansible settings tab allows you to set Ansible configuration options at the cluster level. The tab is available starting with ADCM 2.2.0.
| Name | Description | Default |
|---|---|---|
forks |
The number of parallel processes to spawn when communicating with remote hosts |
5 |