

Authorization
Roles and access permissions
Authorization in ADB Control is based on Role Based Access Control (RBAC). This mechanism allows you to control access to the various functions of the system depending on the role assigned to each user.
Currently, ADB Control supports the following roles:
-
Owner— system owner. -
Administrator— ADB Control administrator. -
ADBM Administrator— ADBM administrator. -
Advanced User— user with advanced permissions. -
Regular User— ordinary user.
|
NOTE
For users with the |
The table below shows the distribution of access rights between the abovementioned roles.
|
IMPORTANT
The resource group management feature, which was available in ADB Control 4.14, is absent in the current ADB Control version, 4.15.
Support for this functionality will be restored in future releases of ADB Control.
|
| Permission | Description | Regular User | Advanced User | Administrator | Owner | ADBM Administrator |
|---|---|---|---|---|---|---|
View self queries |
Ability to view own transactions and commands (including detailed information on them). These are transactions and queries that are committed in ADB under the role which name matches the user name in ADB Control or belongs to the LDAP group for which a mapping is configured in ADB Control |
Yes |
Yes |
Yes |
Yes |
No |
Kill self queries |
Ability to terminate and cancel own transactions and commands. These are transactions and queries that are committed in ADB under the role which name matches the user name in ADB Control or belongs to the LDAP group for which a mapping is configured in ADB Control |
Yes |
Yes |
Yes |
Yes |
No |
View some queries |
Ability to view the transactions and commands to which a user has relevant permissions (including detailed information) |
No |
Yes |
Yes |
Yes |
No |
Kill some queries |
Ability to terminate and cancel the transactions to which a user has relevant permissions |
No |
Yes |
Yes |
Yes |
No |
View all queries |
Ability to view all transactions and commands (including detailed information) |
No |
No |
Yes |
Yes |
No |
Kill all queries |
Ability to terminate and cancel all transactions |
No |
No |
Yes |
Yes |
No |
View relation audit page |
Ability to view the Audit → Relations page where statistics on the number of access attempts to ADB relations are displayed |
No |
No |
Yes |
Yes |
No |
View secured relation audit |
Ability to view a table with secured statistics on ADB relations in a separate modal window |
No |
No |
Yes |
Yes |
No |
View Operations audit page |
Access to the Audit → Operations page where statistics on launches of various operations in ADB Control is displayed |
No |
No |
Yes |
Yes |
No |
View Authorization audit page |
Access to the Audit → Authorizations page where information on user authorizations in ADB Control/ADB is displayed |
No |
No |
Yes |
Yes |
No |
View ADB jobs |
Access to the Jobs → ADB Control page where information on scheduled (Schedule) and completed (Audit) jobs in ADB Control is displayed |
No |
No |
Yes |
Yes |
No |
View backup manager jobs |
Access to the Jobs → Backup manager page where information on scheduled (Schedule) and completed (Audit) jobs in ADB Backup Manager is displayed |
No |
No |
Yes |
Yes |
Yes |
View backup manager page |
Access to the Backup manager page with the ability to view information on clusters, actions, backups, and restores |
No |
No |
Yes |
Yes |
Yes |
Run backup manager actions |
Ability to run actions in ADB Backup Manager |
No |
No |
Yes |
Yes |
Yes |
Create backup manager configuration |
Ability to create and edit configurations in ADB Backup Manager |
No |
No |
Yes |
Yes |
Yes |
View ADB information page |
Access to the Information → ADB Control page where the current status of ADB Control components is displayed |
No |
No |
Yes |
Yes |
No |
View backup manager information page |
Access to the Information → Backup manager page where the current status of ADB Backup Manager components is displayed |
No |
No |
Yes |
Yes |
Yes |
View configuration page |
Access to the Configuration page with the ability to manage clusters and configure policies for jobs and security |
No |
No |
No |
Yes |
No |
View users page |
Access to the Users page with the ability to manage users (create, edit, block, delete), set mappings with LDAP groups, and set advanced permissions |
No |
No |
No |
Yes |
No |
View sessions |
Access to the Monitoring → Sessions page functionality |
No |
No |
Yes |
Yes |
No |
Manage user sessions |
Ability to terminate sessions of ADB Control users on the Users → Active sessions page |
No |
No |
Yes |
Yes |
No |
Configure role mappings with LDAP groups
If basic authentication is used, roles are assigned to users at the creation step. However, if LDAP authentication is configured, you need to map user groups of the selected LDAP server to roles in ADB Control. It allows users to get appropriate permissions in the monitoring system.
You can manage such mappings on the Users → LDAP group mapping tab in the ADB Control web interface.
Add a mapping
To add a new mapping, follow the steps:
-
Click Create new mapping on the Users → LDAP group mapping tab.
 Switch to adding a mapping
Switch to adding a mapping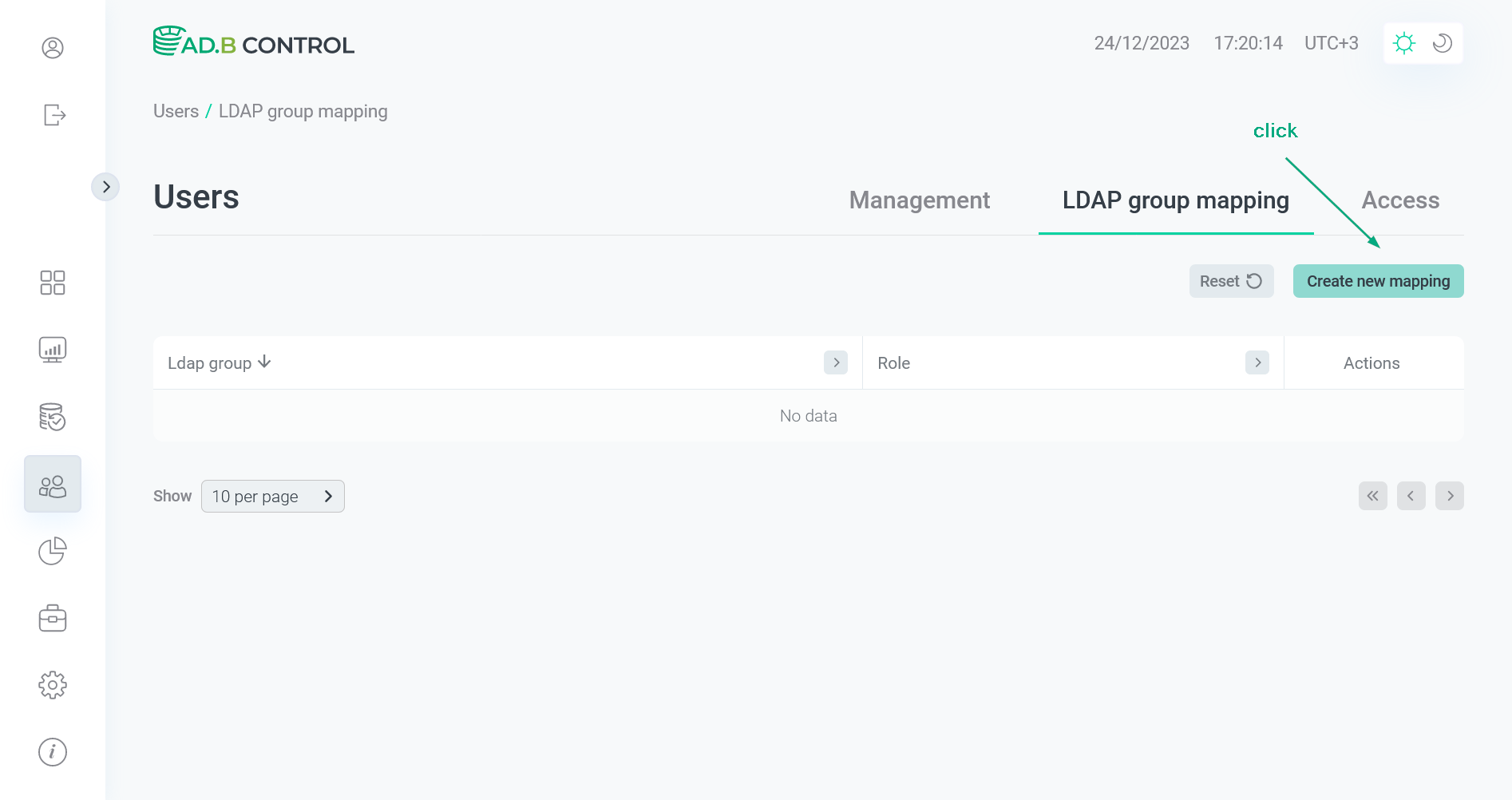 Switch to adding a mapping
Switch to adding a mapping -
In the window that opens, fill in the following fields:
-
Group — a user group name on the LDAP server. A drop-down list with group names becomes available after the LDAP authentication is successfully configured.
-
Role — a role in ADB Control.
IMPORTANTEach LDAP group can be mapped only to one role in ADB Control.
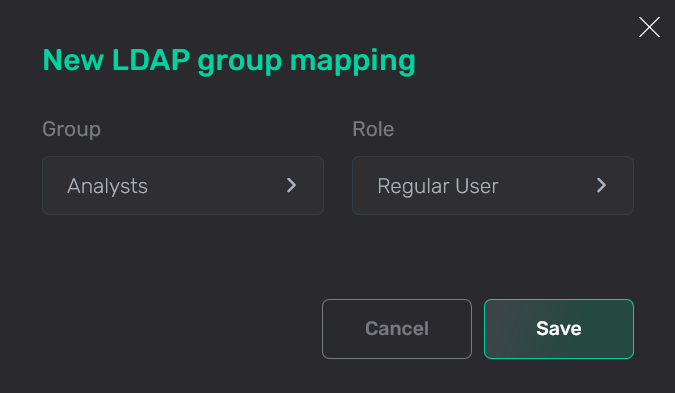 Fill in the fields
Fill in the fields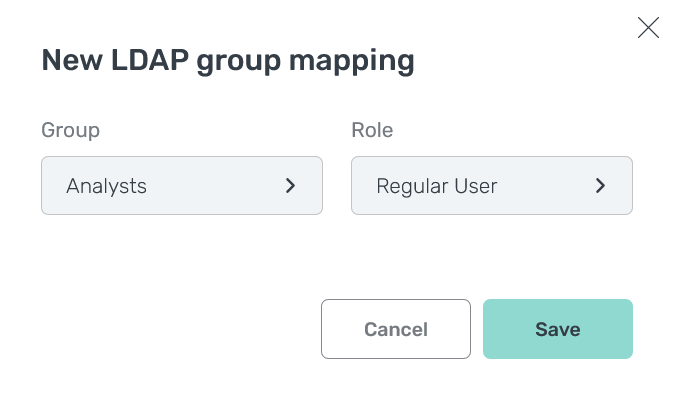 Fill in the fields
Fill in the fields
-
-
Click Save. As a result, a new mapping is displayed on the Users → LDAP group mapping tab.
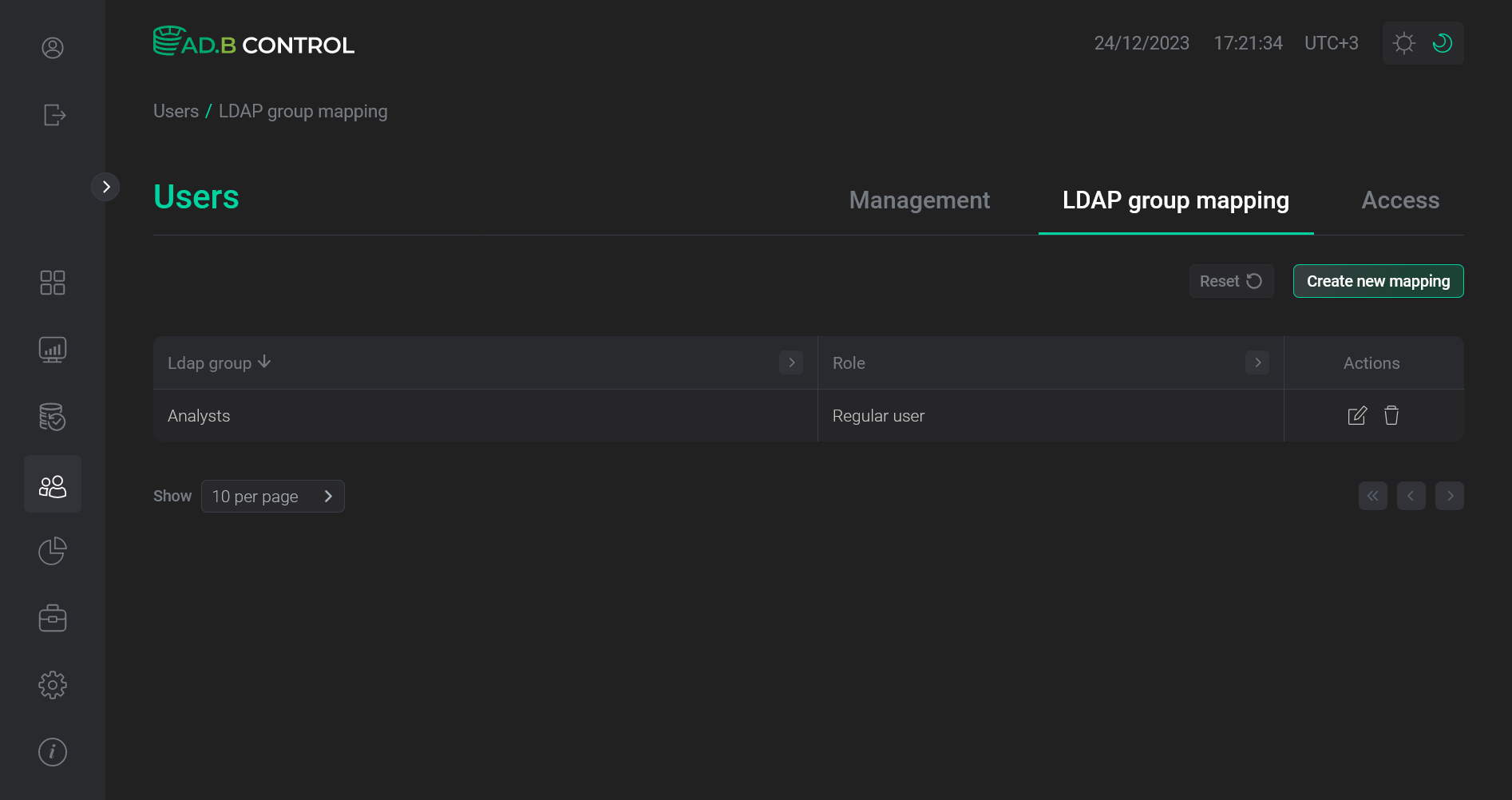 Mapping is added
Mapping is added Mapping is added
Mapping is added
Edit a mapping
To edit an existing mapping, follow the steps:
-
Click the
icon in the Actions column on the Users → LDAP group mapping tab.
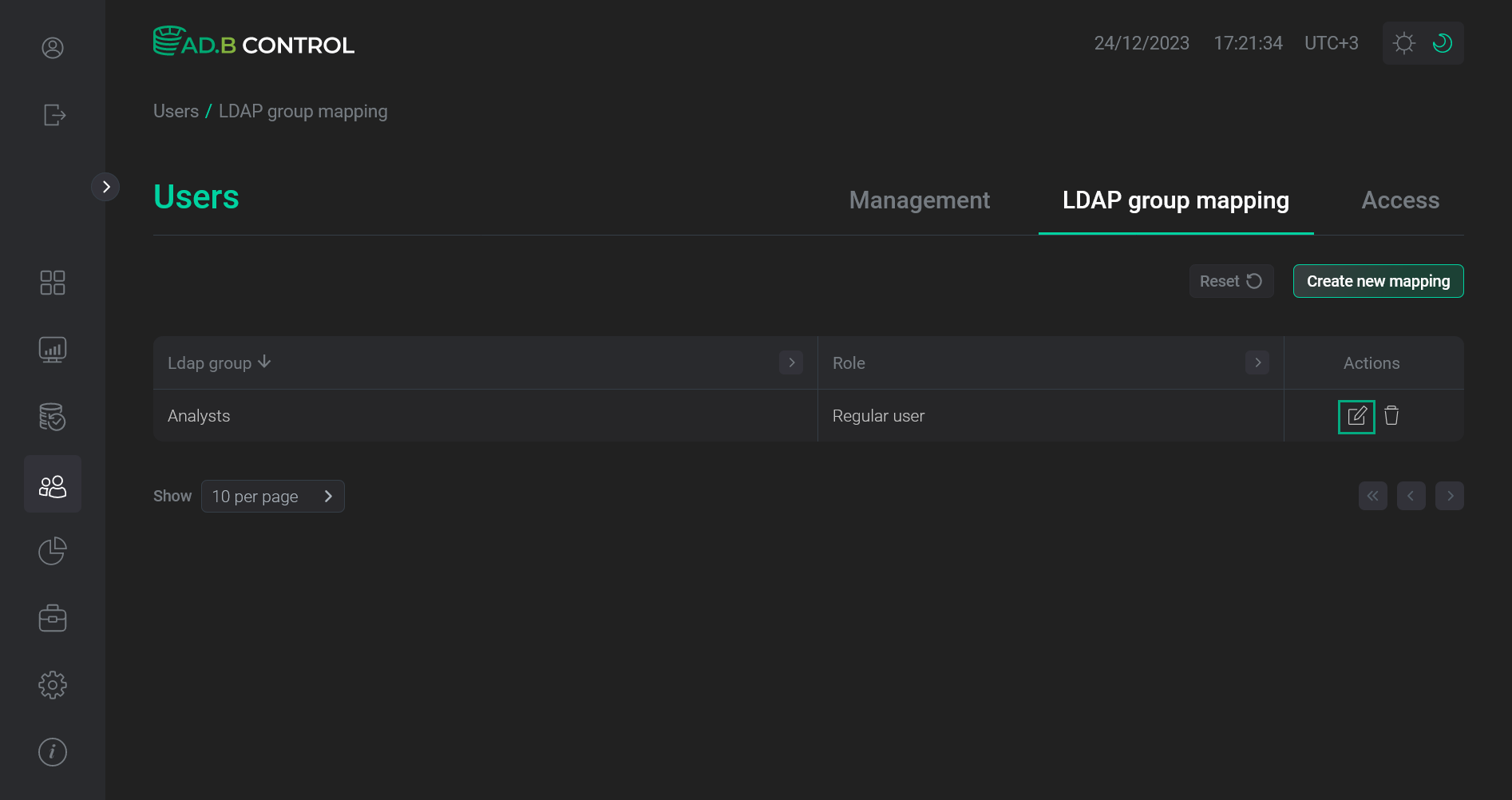 Switch to editing a mapping
Switch to editing a mapping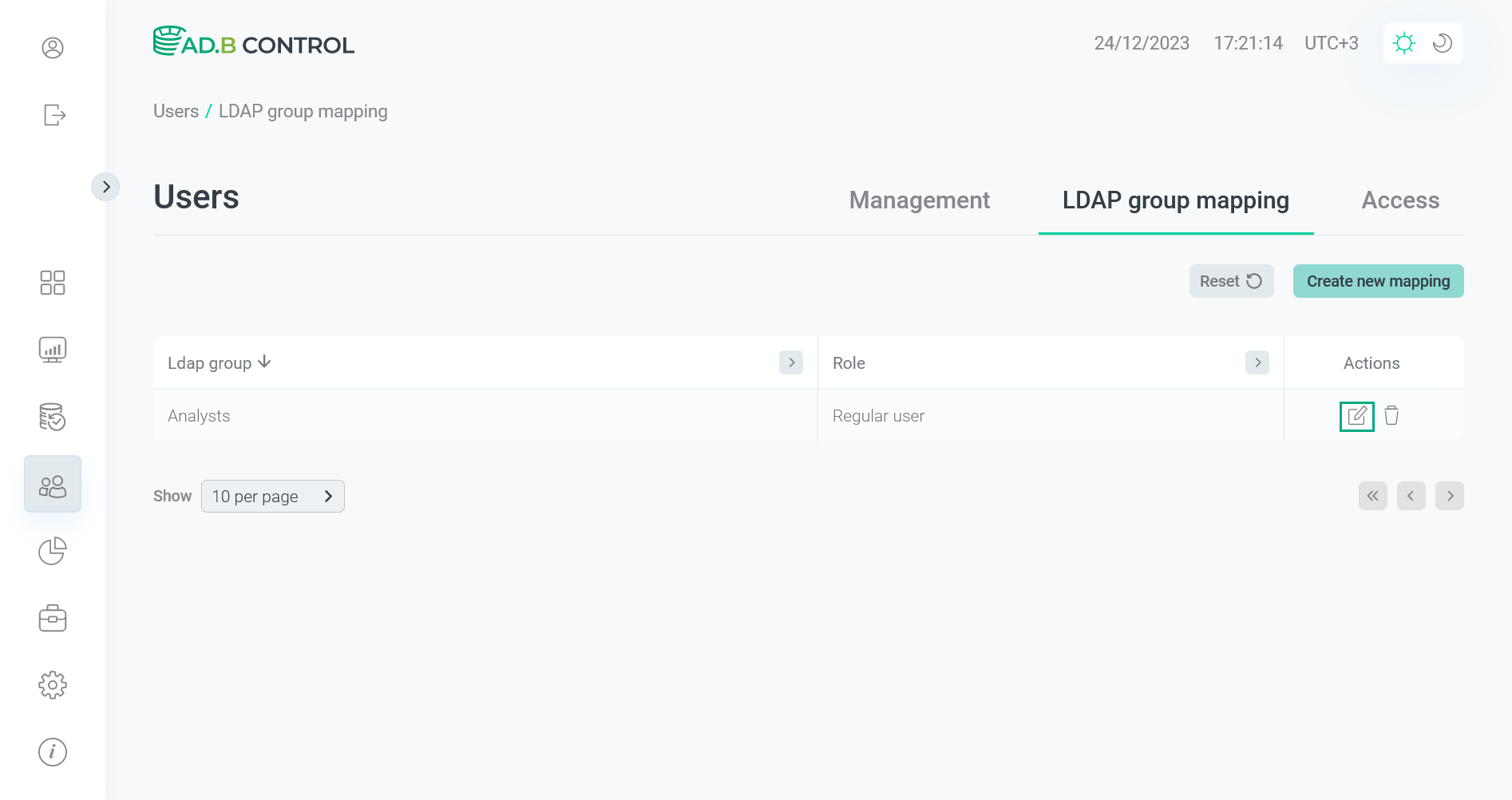 Switch to editing a mapping
Switch to editing a mapping -
In the window that opens, edit necessary fields. All fields are the same as described above. The Group field value cannot be changed.
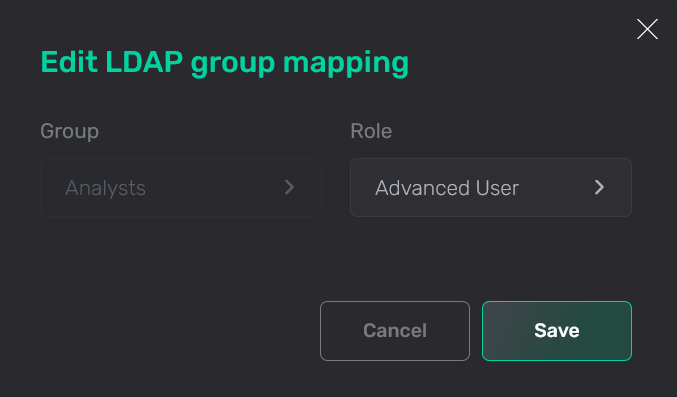 Edit a mapping
Edit a mapping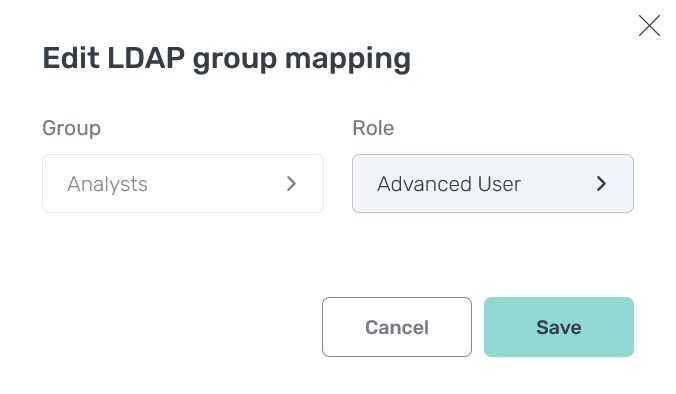 Edit a mapping
Edit a mapping -
Click Save. As a result, the mapping data is updated on the Users → LDAP group mapping tab.
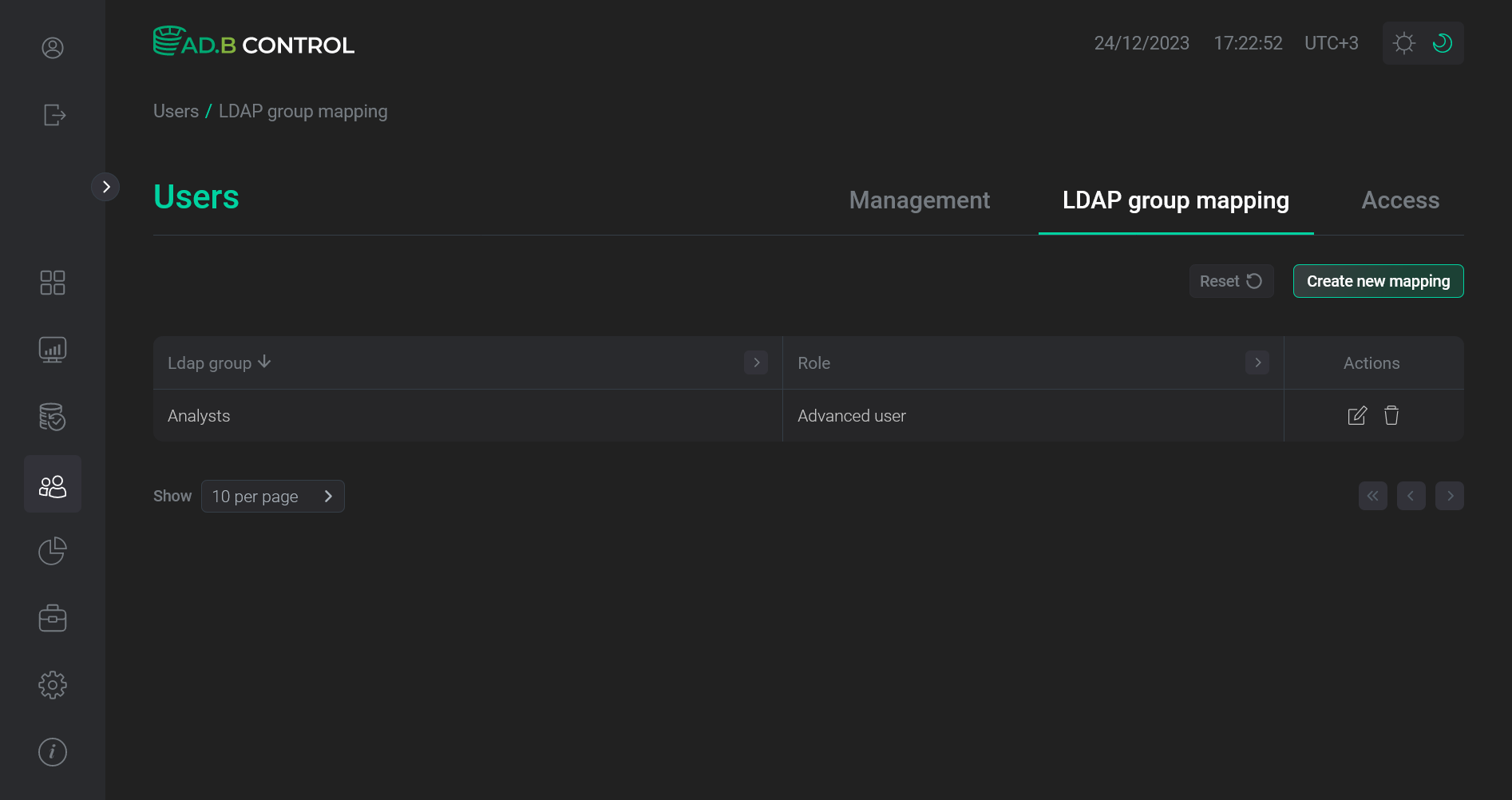 Mapping is updated
Mapping is updated Mapping is updated
Mapping is updated
Delete a mapping
To delete an existing mapping, follow the steps:
-
Click the
icon in the Actions column on the Users → LDAP group mapping tab.
 Switch to deleting a mapping
Switch to deleting a mapping Switch to deleting a mapping
Switch to deleting a mapping -
In the window that opens, confirm the operation by clicking Delete.
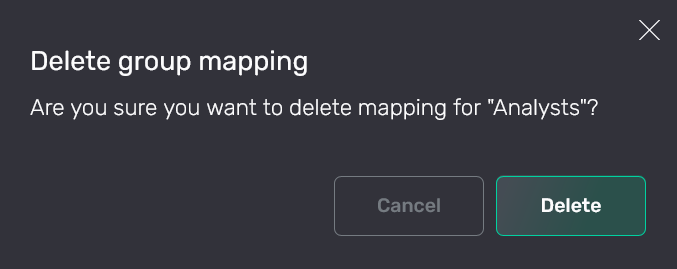 Confirm the operation
Confirm the operation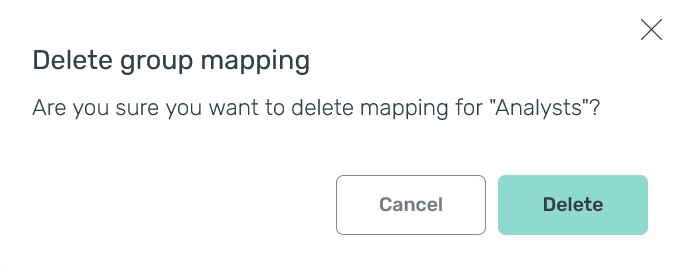 Confirm the operation
Confirm the operationAs a result, the mapping is removed from the Users → LDAP group mapping tab.
 Mapping is removed
Mapping is removed Mapping is removed
Mapping is removed
Actualize LDAP group names
|
NOTE
If LDAP authentication is configured, LDAP groups are synchronized automatically each time when ADB Control is being started. The following feature is designed for on-demand updates of LDAP group names. |
Starting with ADB Control 4.7.5, you can actualize LDAP group names in the previously created mappings by running synchronization with an LDAP server on the Users → LDAP group mapping page. To run synchronization:
-
Ensure that LDAP authentication for ADB Control is successfully configured and ADB Control roles are mapped to LDAP groups on the Users → LDAP group mapping page.
-
Click Actualise.
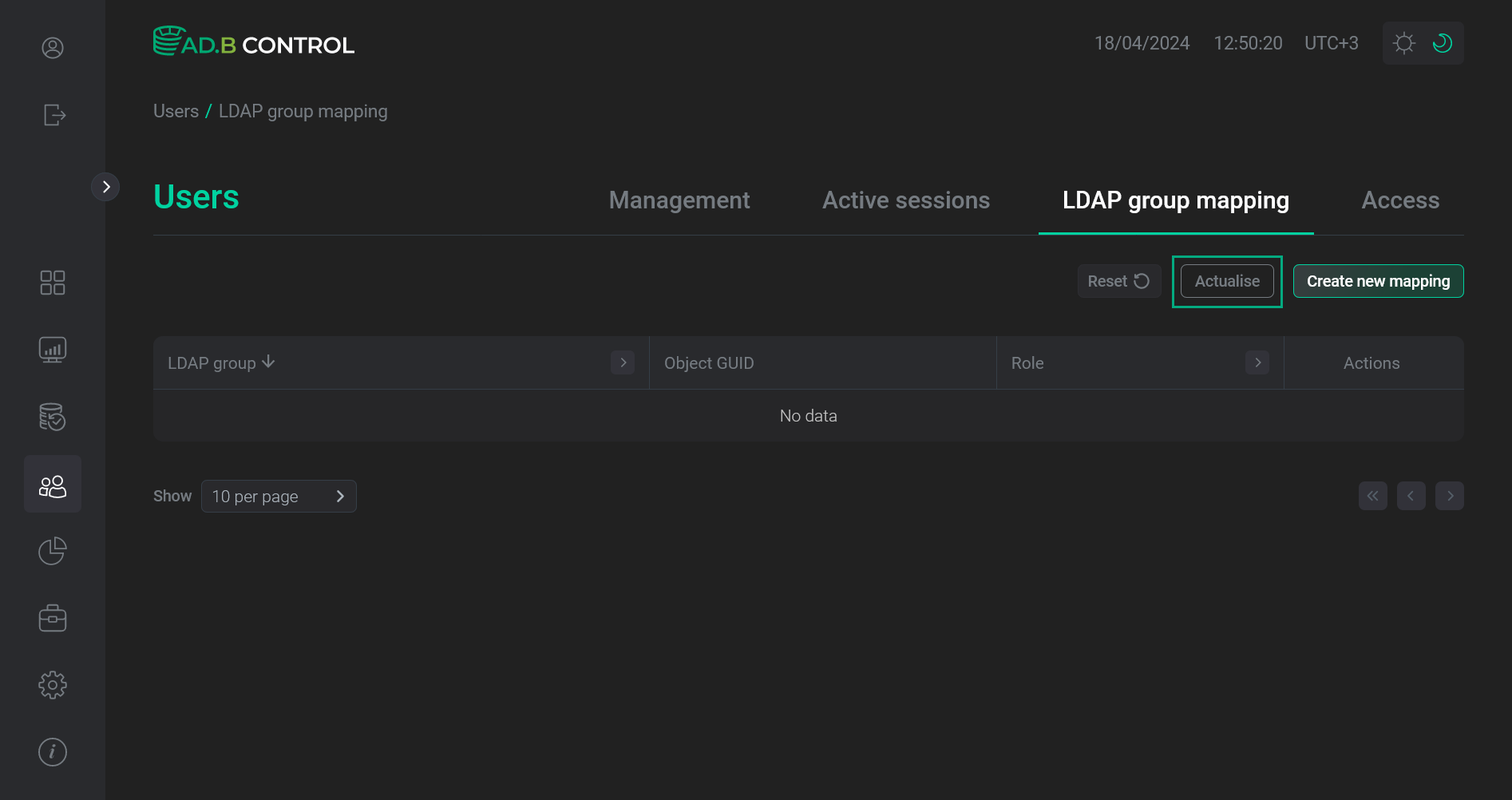 Go to actualization of LDAP group names
Go to actualization of LDAP group names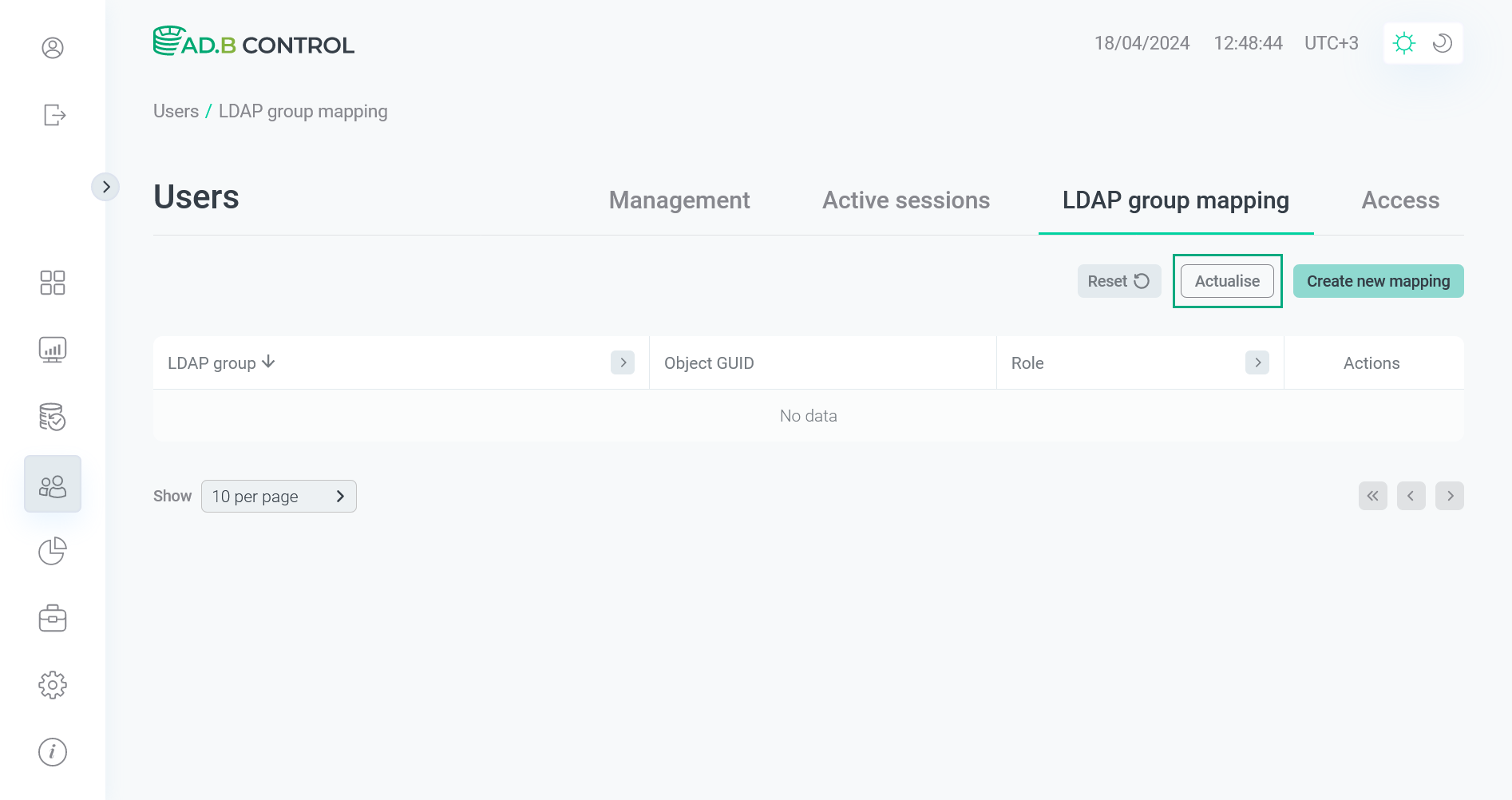 Go to actualization of LDAP group names
Go to actualization of LDAP group names -
Read the information in the window that opens and confirm the action by clicking Actualise.
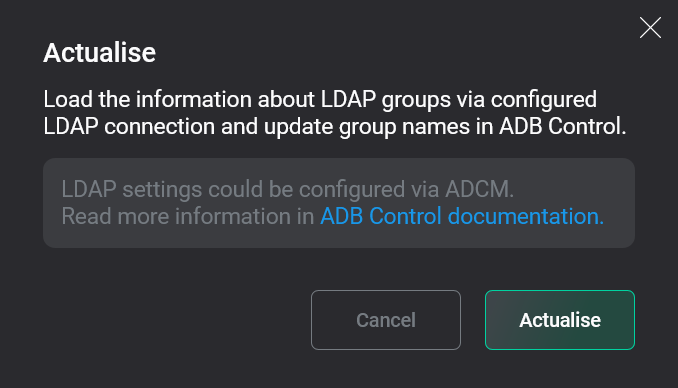 Confirm the action
Confirm the action Confirm the action
Confirm the action
Set advanced permissions
Users with the Advanced User role can be granted extended access rights to specific ADB databases. With such rights, users are able to view all transactions and commands running in the respective databases (regardless of who launched them) and interrupt or cancel them if necessary (see View some queries and Kill some queries permissions in the table above).
You can manage such advanced permissions on the Users → Access tab in the ADB Control web interface.
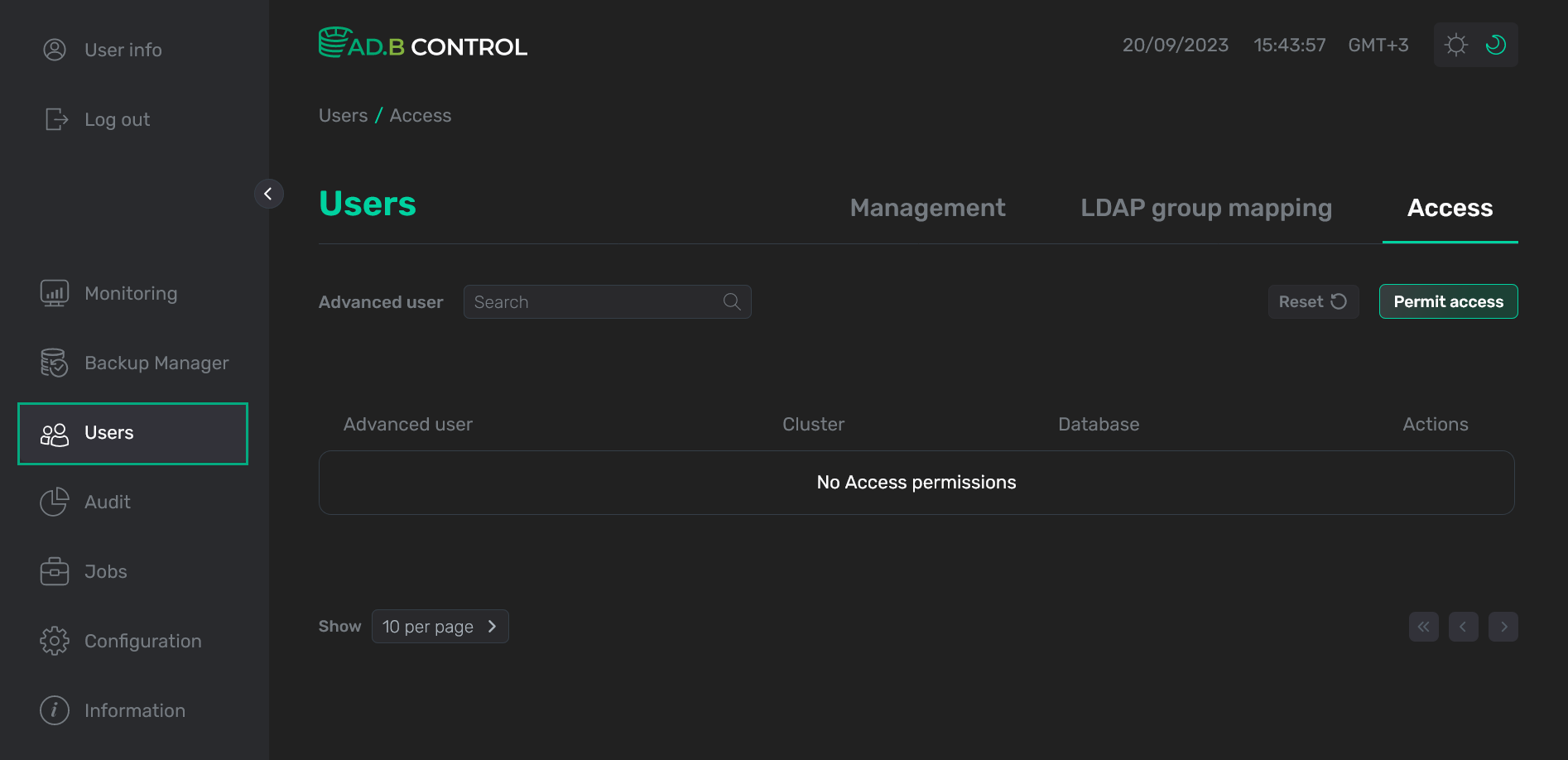
Add a permission
To add a new permission, follow the steps:
-
Click Permit access on the Users → Access tab.
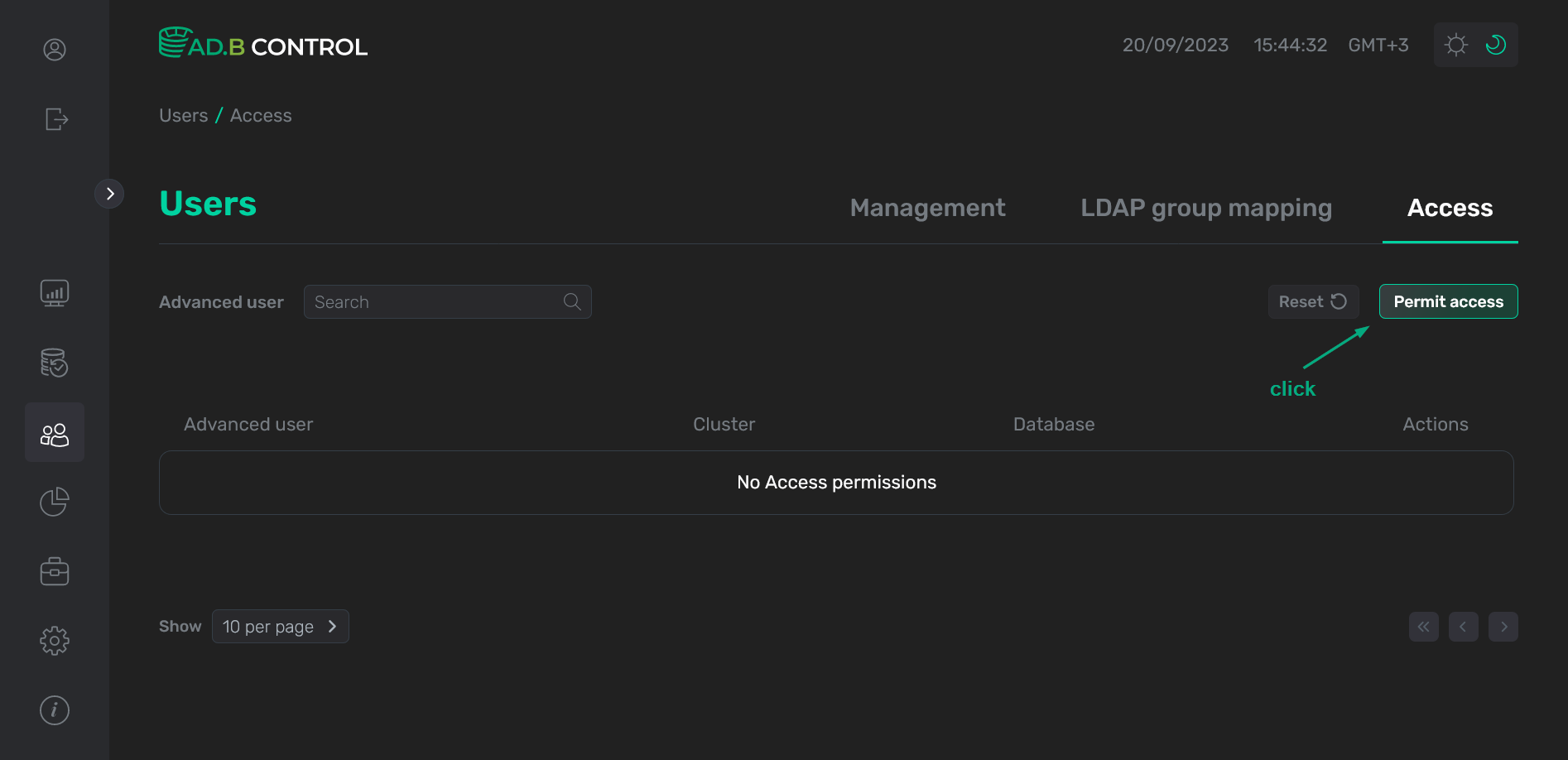 Switch to adding a permission
Switch to adding a permission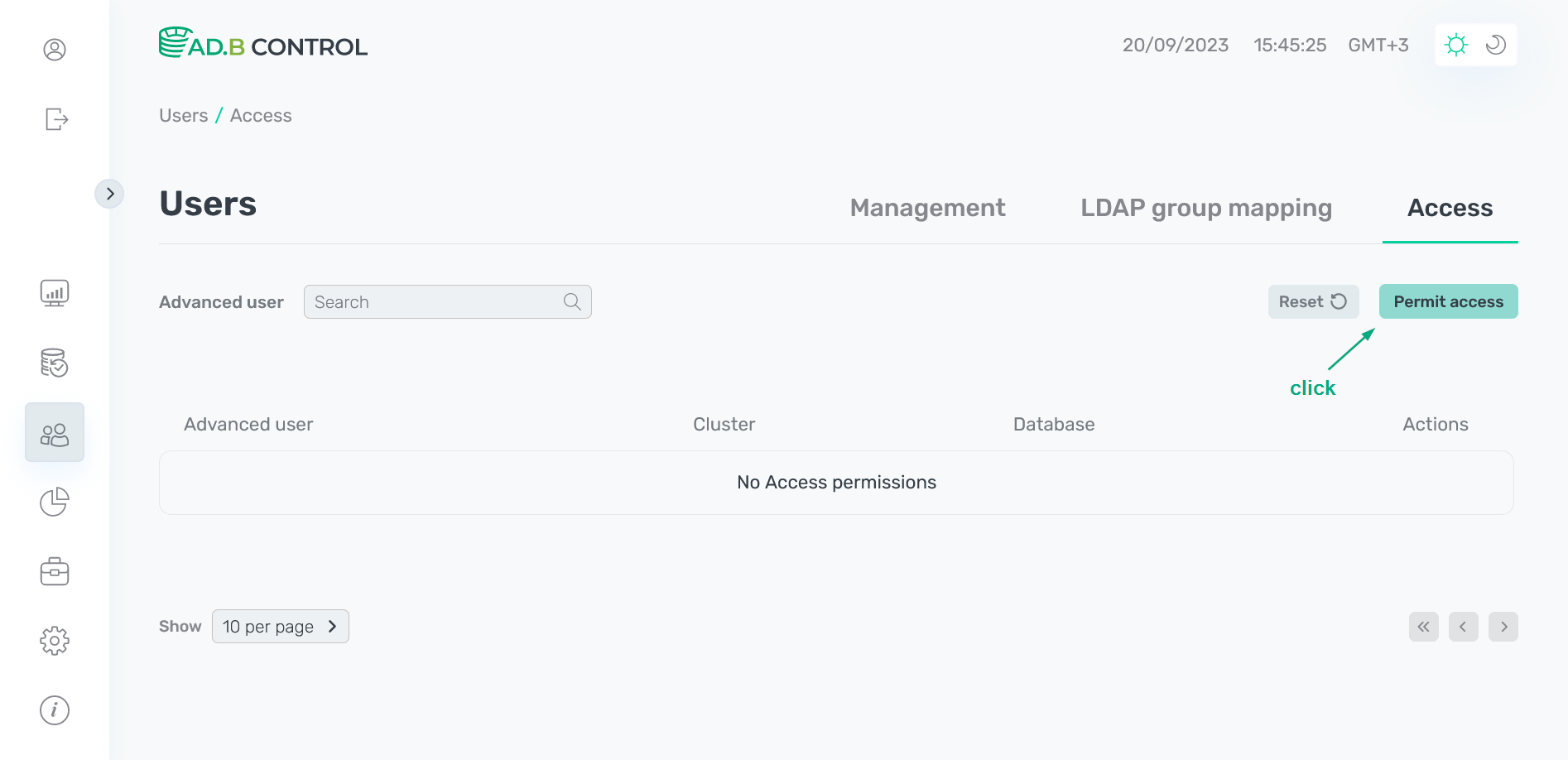 Switch to adding a permission
Switch to adding a permission -
In the window that opens, fill in the following information:
-
In the Username field, specify one or several users. To add each user, add a user name and then click +. As a result, a list of users is displayed under the Username field. You can delete wrong records if necessary.
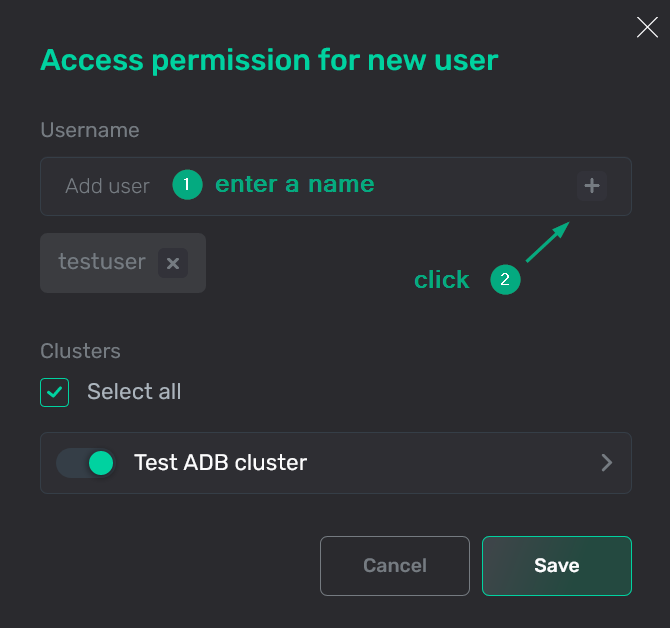 Enter user names
Enter user names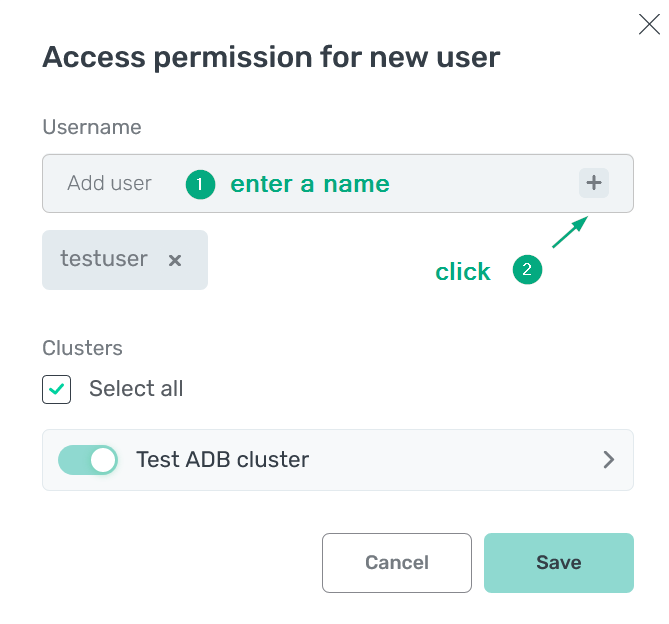 Enter user names
Enter user names -
In the Clusters section, select ADB clusters and databases to be accessed by the users added in the previous step. To select all clusters with all databases, set the Select all flag (it is set by default).
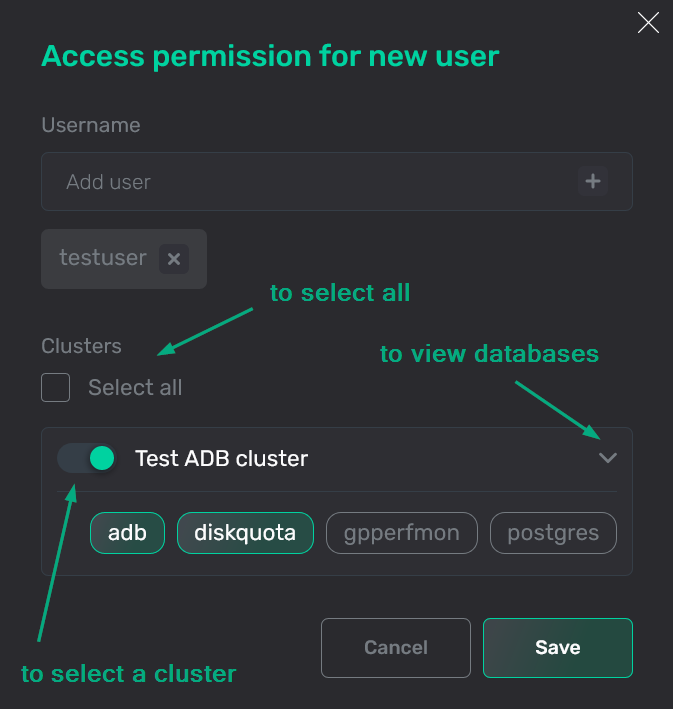 Select clusters and databases
Select clusters and databases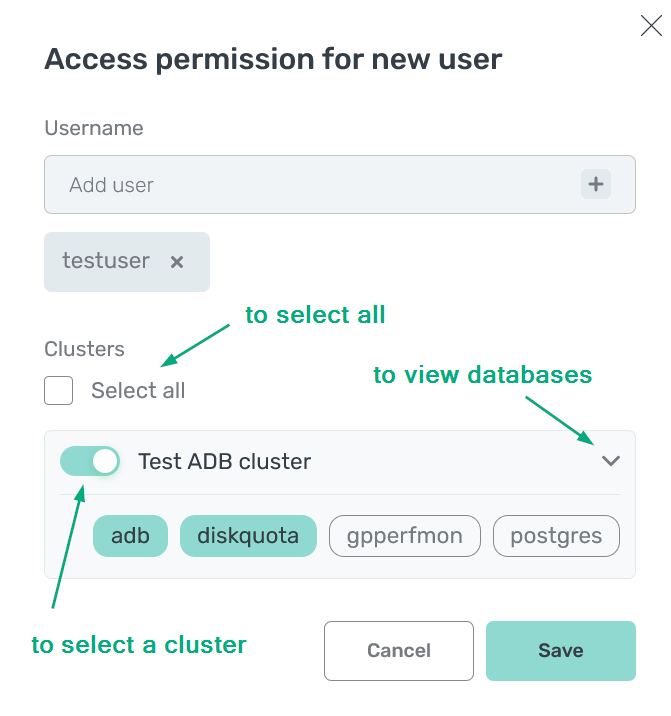 Select clusters and databases
Select clusters and databases
-
-
Click Save. As a result, a new permission is displayed on the Users → Access tab.
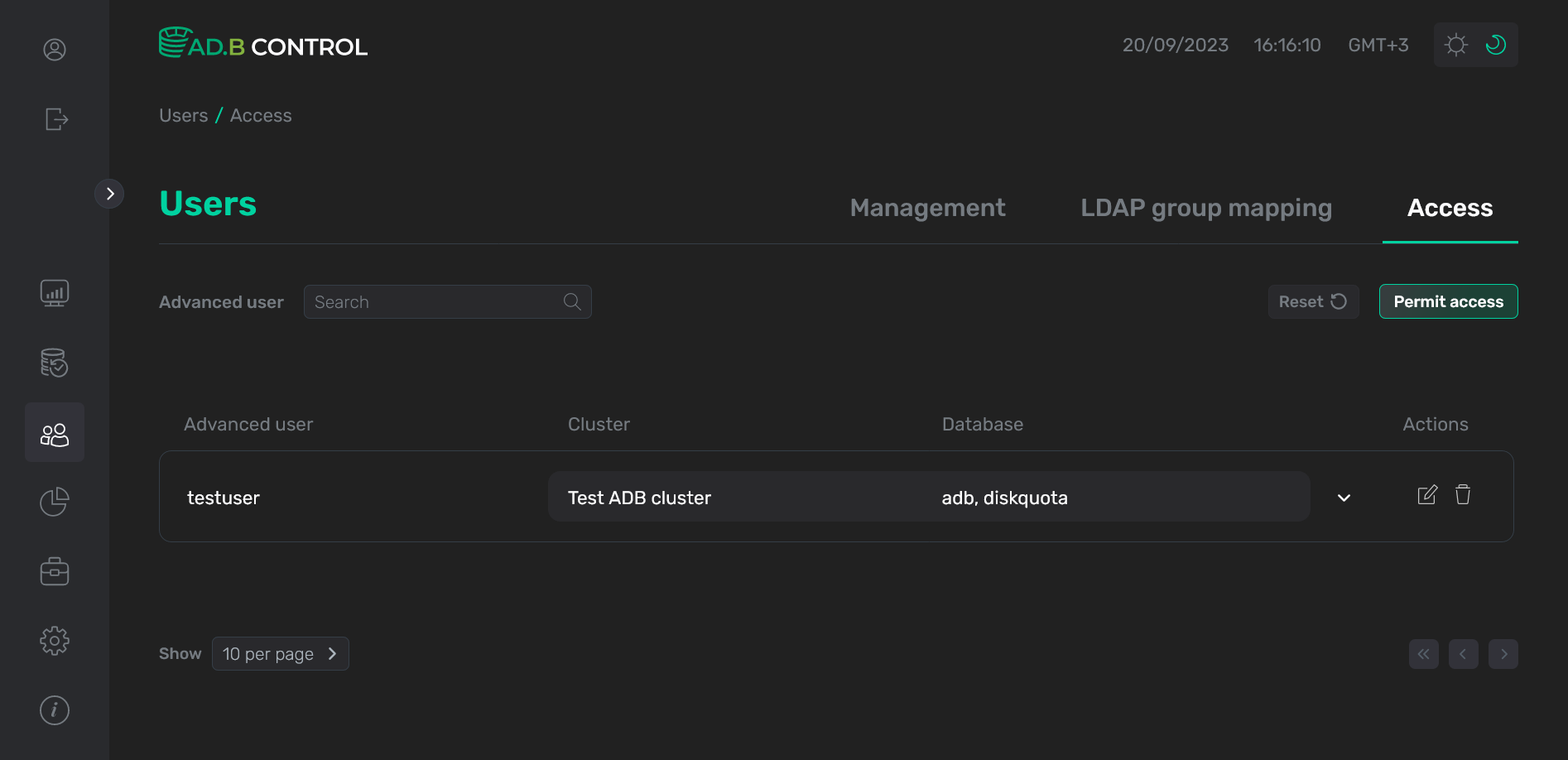 Permission is added
Permission is added Permission is added
Permission is added
Edit a permission
To edit an existing permission, follow the steps:
-
Click the
icon in the Actions column on the Users → Access tab.
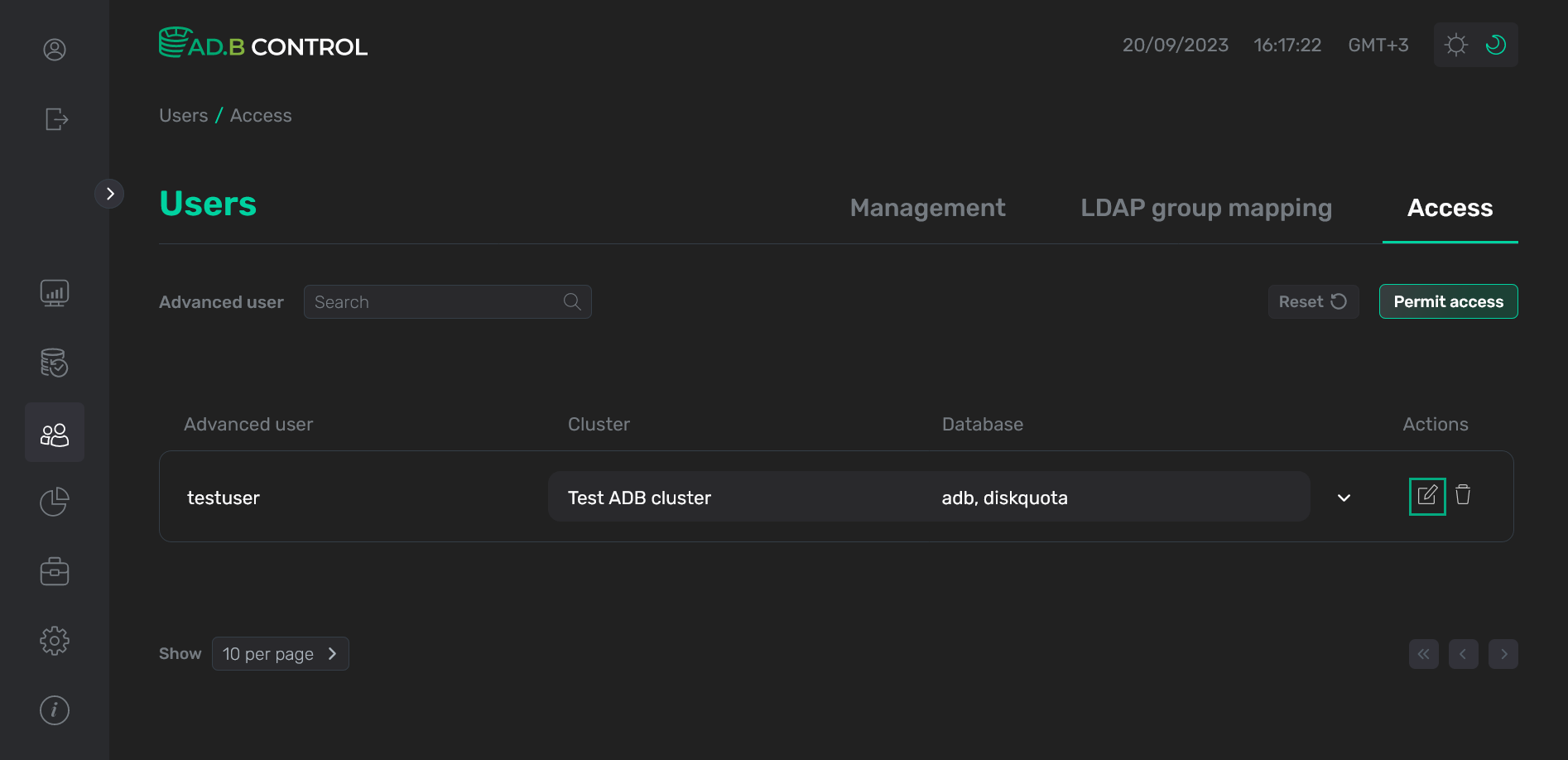 Switch to editing a permission
Switch to editing a permission Switch to editing a permission
Switch to editing a permission -
In the window that opens, edit necessary fields. All fields are the same as described above. The Username field value cannot be changed.
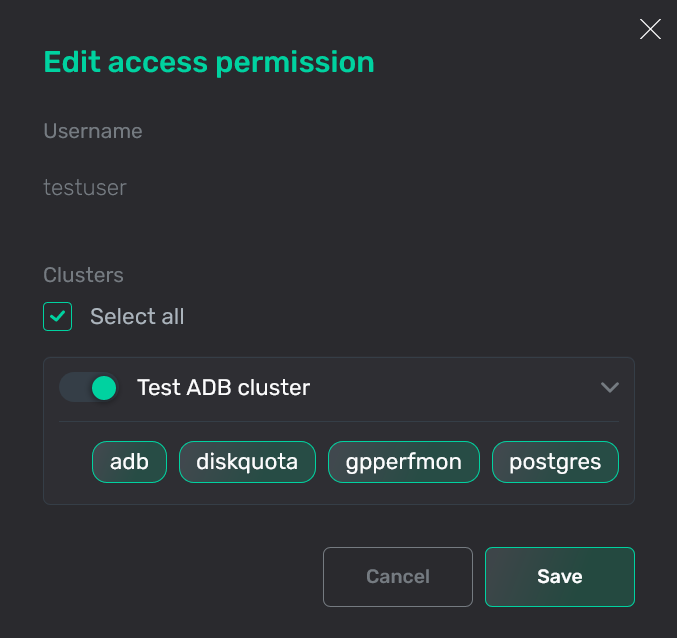 Edit a permission
Edit a permission Edit a permission
Edit a permission -
Click Save. As a result, the permission data is updated on the Users → Access tab.
 Permission is updated
Permission is updated Permission is updated
Permission is updated
Delete a permission
To delete an existing permission, follow the steps:
-
Click the
icon in the Actions column on the Users → Access tab.
 Switch to deleting a permission
Switch to deleting a permission Switch to deleting a permission
Switch to deleting a permission -
In the window that opens, confirm the operation by clicking Delete.
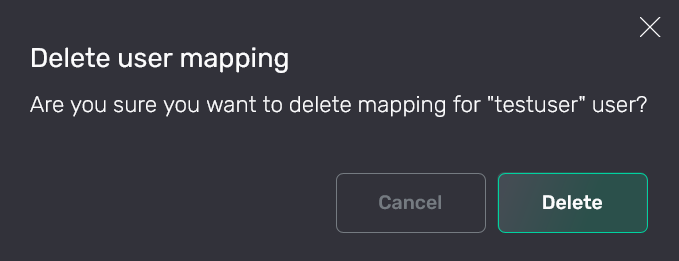 Confirm the operation
Confirm the operation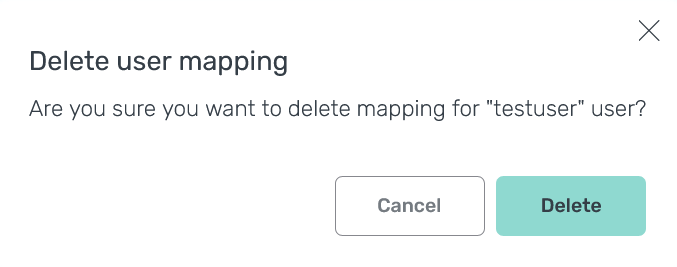 Confirm the operation
Confirm the operationAs a result, permission is removed from the Users → Access tab.
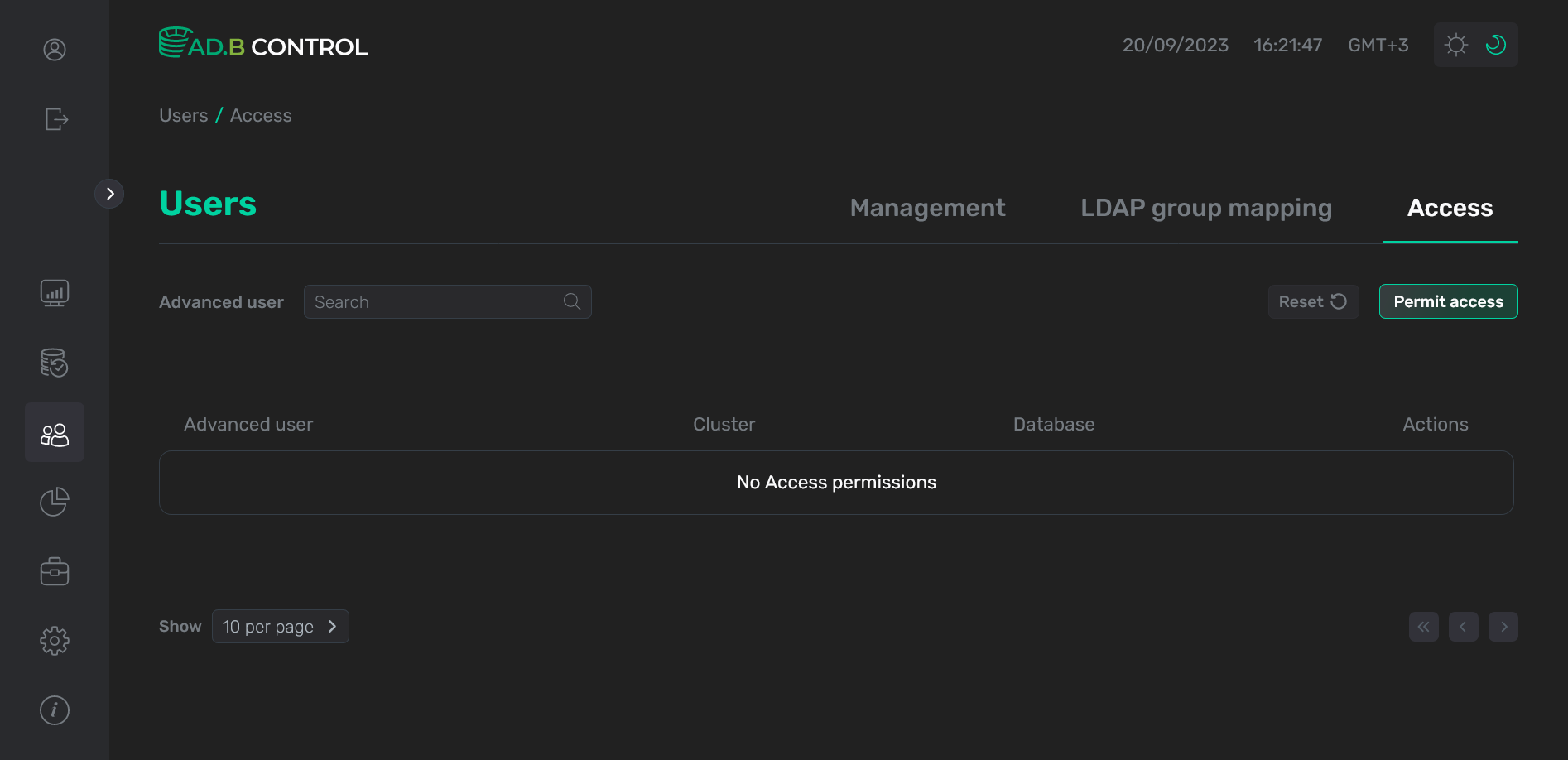 Permission is removed
Permission is removed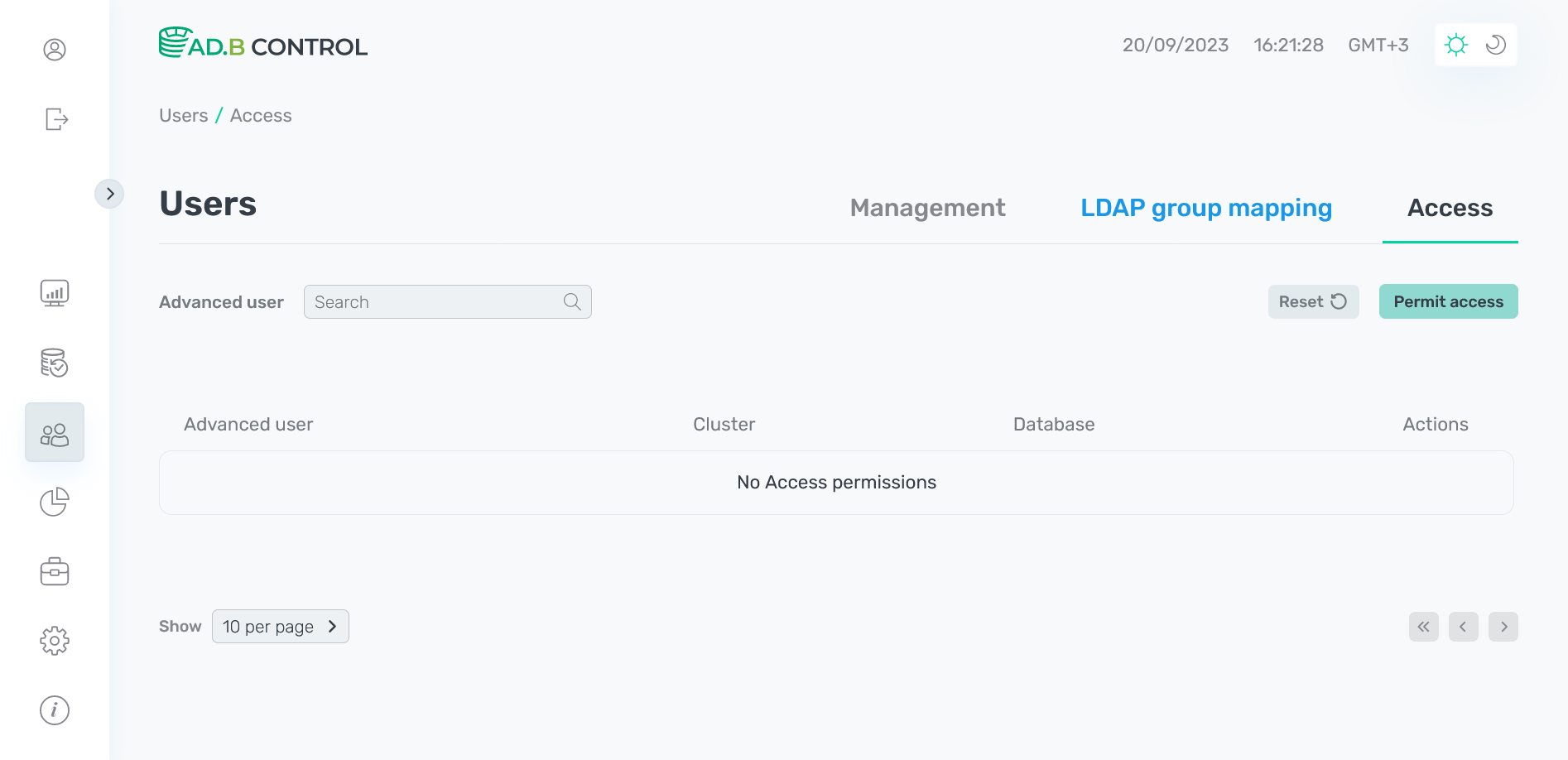 Permission is removed
Permission is removed