

LDAP authentication in ADB
ADB (as well as Greenplum) supports Lightweight Directory Access Protocol (LDAP) user authentication. When LDAP authentication is used, user accounts and passwords are checked on the selected LDAP server. The steps for configuring LDAP authentication in ADB via ADCM are described below.
Configure LDAP authentication
To configure LDAP authentication in ADB, follow the steps:
-
Ensure the target LDAP server is configured and available. ADB supports two LDAP implementations: Microsoft Active Directory (MS AD) and 389 Directory server as a part of FreeIPA.
-
Open the ADB service configuration page in ADCM.
-
Switch on the UI LDAP authentication toggle.
-
Field Description Default value Example in MS AD Type
A type of the LDAP server. Possible values:
-
MSAD— Microsoft Active Directory; -
FreeIPA— 389 Directory server as a part of FreeIPA.
MSAD
MSAD
LDAP Host
A domain name or an IPv4 address of the LDAP server
—
10.92.12.49
LDAP Port
A port number on the LDAP server to connect to
—
389
Users baseDN
A limitation of the search scope of objects in the LDAP directory that is used in user search requests
—
ou=Peoples,dc=ad,dc=ranger-test
Groups baseDN
A limitation of the search scope of objects in the LDAP directory that is used in group search requests
—
ou=Groups,dc=ad,dc=ranger-test
Users filter
An LDAP filter that is used to search users. Should be specified according to the RFC 2254
(&(|(objectClass=person)(objectClass=inetOrgPerson))(cn=*))
(&(objectClass=person)(objectClass=organizationalPerson)(givenName=*)(sn=*)(sAMAccountName=*))
Groups filter
An LDAP filter that is used to search groups. Should be specified according to the RFC 2254
(&(|(objectClass=group)(objectClass=groupofnames)(objectClass=groupOfUniqueNames))(cn=*))
(cn=*)
SA Login
A user name that is used for service requests to the LDAP server
—
cn=admin,dc=ad,dc=ranger-test
Password
A user password that is used for service requests to the LDAP server
—
A password of the
adminuserLowercase login
Defines whether to convert user names to lowercase
false
false
Lowercase group
Defines whether to convert group names to lowercase
false
false
Sync interval
A
cronexpression that defines how often synchronization of ADB users and groups with an LDAP server should be performed. The pg-ldap-sync utility, which comes with the ADB bundle, is used for synchronization0 * * * *
0 * * * *
NOTEVarious LDAP implementations use different names for object types and identifiers. It is recommended to refine the settings format for a specific LDAP implementation from the LDAP server administrator.
-
-
Click Save. Then apply the Reconfigure action to the ADB service.
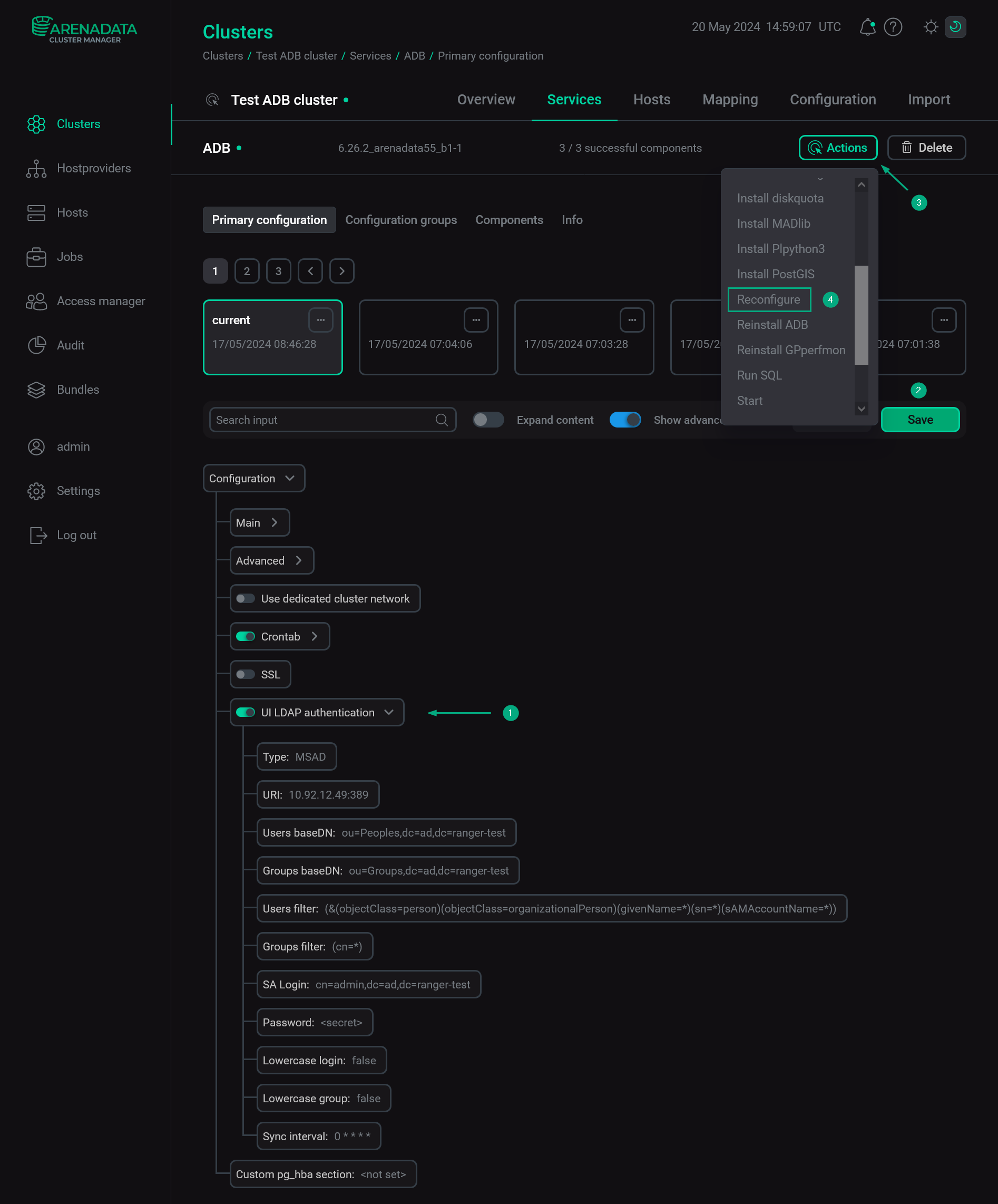 Configure LDAP authentication for ADB via ADCM
Configure LDAP authentication for ADB via ADCM
Synchronize ADB and LDAP
If LDAP authentication is configured successfully, the following operations are performed in ADB automatically:
-
Update of the pg_hba.conf file. The following entry about LDAP authentication is added to the pg_hba.conf file, which is located in the data directory of the coordinator host (/data1/master/gpseg-1/ in the following example):
# BEGIN LDAP host all +ldap_users 0.0.0.0/0 ldap ldapserver=<LDAP Host> ldapport=<LDAP Port> ldapbasedn="<Users baseDN>" ldapbinddn="<SA Login>" ldapbindpasswd="<Password>" ldapsearchattribute="<attribute>" # END LDAP
where:
-
ldap_users— a name of the ADB role, to which all LDAP users will be added. -
<LDAP Host>,<LDAP Port>,<Users baseDN>,<SA Login>,<Password>— values of the eponymous parameters of the ADB service. -
<attribute>— the LDAP attribute whose value will be used as a name of each role in ADB when synchronizing users. Possible values:-
sAMAccountName— for MS AD. -
uid— for FreeIPA.
-
-
-
Synchronization of ADB users and groups with LDAP. Information about LDAP users and groups, which meet the selection criteria specified in the configuration step, is added to the ADB database. Synchronization is performed via the pg-ldap-sync utility. To ensure successful synchronization, you can run the following query against the
pg_rolestable:SELECT rolname FROM pg_roles;As the SQL command output shows, the following roles are automatically created in ADB after successful LDAP synchronization:
-
ldap_users— a role into which all LDAP users are added (by running theCREATE ROLE … LOGIN IN ROLE ldap_users …command automatically). -
ldap_groups— a role into which all LDAP groups are added (by running theCREATE ROLE … NOLOGIN IN ROLE ldap_groups …command automatically). -
ffedorov,ppetrov,ssemenov,zeptest— all users received from the LDAP server and added to theldap_usersrole. -
ADCM,ADH,Adccadmins,Analysts,Managers— all groups received from the LDAP server and added to theldap_groupsrole. The membership of users in these groups is set automatically by runningGRANT.
rolname ------------- gpadmin gpmon ldap_users ldap_groups ADCM ADH Adccadmins Analysts Managers ffedorov ppetrov ssemenov zeptest (13 rows)
-
Check LDAP authentication
To check that LDAP authentication is properly configured in ADB, you can run psql to connect to ADB using the name of any LDAP user as the -U argument (ffedorov in the following example).
$ psql adb -h bds-mdw -U "ffedorov"If LDAP authentication is configured successfully, you will be prompted to enter the user password. After entering the correct password (assigned on the LDAP server side), the user can access the database.
Password for user ffedorov: psql (12.22) Type "help" for help. adb=>