

SSL encryption
ADB Control
You can secure communication between ADB Control web server and clients using the HTTPS protocol, which is based on SSL encryption. To configure access to ADB Control via HTTPS, follow the steps:
-
Open the ADB Control service configuration page in ADCM.
-
Set the Show advanced flag.
-
Activate the SSL switcher.
-
Fill in the following fields if you need to use your own certificates.
IMPORTANTIf no settings are filled in, ADB Control will create certificates by itself.
Parameter Description Default value CA certificate
Server certificate authority (CA) file contents in the CRT format (*.crt file)
—
Server certificate
Server certificate contents in the CRT format (*.crt file)
—
Server private key
Server private key contents (*.key file)
—
Verify system endpoints' certificates
A flag that indicates whether to verify certificates of system endpoints.
When using the Verify system endpoints' certificates option in the ADB Control configuration with self-signed certificates, ensure that you added the root and intermediate CA certificates to the OS trusted root certificate stores.
In order to use the Verify system endpoints' certificates option with your own certificates, for proper verification, add the ADB Control IP address to the
CNfield of the san.cnf file (SAN) and exclude DNS from thealt_namessection (leave only IP)false
Server JKS keystore path
A path to the keystore file in the JKS format for the ADB Control server part. For example, /opt/adcc/ssl/keystore.jks
—
Server JKS keystore password
A password that is used for connecting to Server JKS keystore path
—
Server JKS truststore path
A path to the truststore file in the JKS format for the ADB Control server part. For example, /opt/adcc/ssl/truststore.jks
—
Server JKS truststore password
A password that is used for connecting to Server JKS truststore path
—
Client JKS keystore path
A path to the keystore file in the JKS format for the ADB Control client part (ADB Control/ADBM agents). For example, /opt/ssl/keystore.jks
—
Client JKS keystore password
A password that is used for connecting to Client JKS keystore path
—
Client JKS truststore path
A path to the truststore file in the JKS format for the ADB Control client part (ADB Control/ADBM agents). For example, /opt/ssl/truststore.jks
—
Client JKS truststore password
A password that is used for connecting to Client JKS truststore path
—
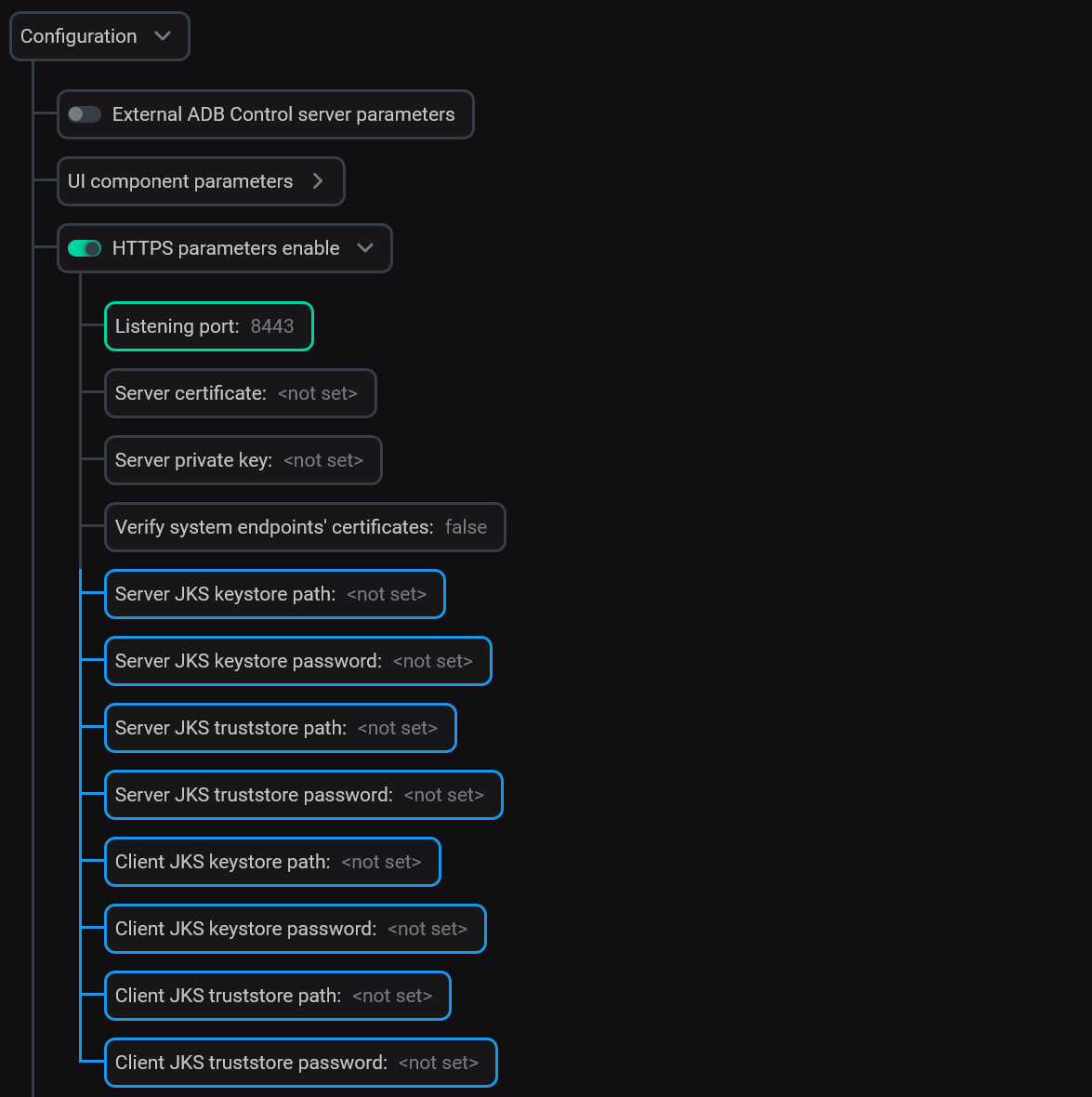 Fill in the SSL parameters
Fill in the SSL parameters
-
Click Save.
-
Apply the Reconfigure & Restart action to the ADB Control service.
 Apply changes
Apply changes
After all steps are completed successfully, the ADB Control server port (by default, 81) will be used for SSL. The ADB Control address will look as follows: https://<ADB Control IP address>:81.
External databases
Starting with ADB Control 4.11.0, after you enable SSL as described above, SSL encryption is automatically used for connections to internal databases of ADB Control and ADBM. If external databases are used in ADB Control (Metrics DB (ClickHouse), Query DB (PostgreSQL), or Offload DB (PostgreSQL)) and/or external PostgreSQL is used in ADBM, you should manually enable SSL encryption in these databases.
PostgreSQL
-
Add the following options to the postgresql.conf file:
ssl = on ssl_cert_file = '<server_crt_path>' ssl_key_file = '<server_key_path>'where:
-
<server_crt_path>— a path to the server certificate on the PostgreSQL server. For example, /pg_data1/adpg14/server.crt. -
<server_key_path>— a path to the server private key on the PostgreSQL server. For example, /pg_data1/adpg14/server.key.
-
-
Add the following entry to the pg_hba.conf file:
hostssl all all 0.0.0.0/0 md5
-
Restart PostgreSQL to apply changes.
-
To ensure that SSL is successfully configured, you can connect to PostgreSQL via
psql. When connecting, define the following options:-U— user name,-d— database,-h— host IP:$ psql -U adcc -d metrics -h 10.92.41.125After you enter the user password, the following information should be displayed:
SSL connection (protocol: TLSv1.2, cipher: ECDHE-RSA-AES256-GCM-SHA384, bits: 256, compression: off)
-
Perform standard actions to configure external PostgreSQL for ADB Control or ADBM. If you configure Offload DB, refer to Configure job policies → Metrics offload.
|
IMPORTANT
|
ClickHouse
For more information on how to configure SSL encryption in ClickHouse, you can see ClickHouse documentation. The minimal configuration steps are listed below:
-
Apply the following changes to the server configuration file config.xml on each node of the ClickHouse cluster:
-
Enable HTTPS ports and comment HTTP ports:
<https_port>8443</https_port> <!--<http_port>8123</http_port>--> <interserver_https_port>9010</interserver_https_port> <!--<interserver_http_port>9009</interserver_http_port>--> -
Configure the
OpenSSLsection as follows:<openSSL> <server> <certificateFile>/etc/clickhouse-server/certs/server.crt</certificateFile> <privateKeyFile>/etc/clickhouse-server/certs/server.key</privateKeyFile> <verificationMode>relaxed</verificationMode> <caConfig>/etc/clickhouse-server/certs/ca.crt</caConfig> <cacheSessions>true</cacheSessions> <disableProtocols>sslv2,sslv3</disableProtocols> <preferServerCiphers>true</preferServerCiphers> </server> <client> <loadDefaultCAFile>false</loadDefaultCAFile> <caConfig>/etc/clickhouse-server/certs/ca.crt</caConfig> <cacheSessions>true</cacheSessions> <disableProtocols>sslv2,sslv3</disableProtocols> <preferServerCiphers>true</preferServerCiphers> <verificationMode>relaxed</verificationMode> <invalidCertificateHandler> <name>RejectCertificateHandler</name> </invalidCertificateHandler> </client> </openSSL>where the following paths are used (can be different in your environment):
-
/etc/clickhouse-server/certs/server.crt — a path to the server certificate on the ClickHouse node.
-
/etc/clickhouse-server/certs/server.key — a path to the server private key on the ClickHouse node.
-
/etc/clickhouse-server/certs/ca.crt — a path to the CA certificate on the ClickHouse node.
-
-
-
Restart ClickHouse to apply changes.
-
Perform standard actions to configure external ClickHouse for ADB Control.
|
IMPORTANT
To fill in the |