

Use MIT Kerberos KDC in ADB
- Step 1. Install and configure MIT Kerberos KDC
- Step 2. Create principals for ADB in MIT Kerberos KDC
- Step 3. Configure the ADB coordinator and check authentication
- Step 4. Map Kerberos principals to ADB roles
- Step 5. Configure Kerberos authentication for client applications
- Step 6. Configure JDBC connections
Step 1. Install and configure MIT Kerberos KDC
|
TIP
For information on Kerberos authentication, see the MIT Kerberos documentation. |
Below you can find an example of installing and configuring MIT Kerberos KDC on the bds-kerberos.ru-central1.internal host with Ubuntu 22.04. The realm name is RU-CENTRAL1.INTERNAL. Note that the Kerberos realm name should be uppercase:
-
Install Kerberos server and client packages:
$ sudo apt install krb5-kdc krb5-admin-server -
Edit the following Kerberos configuration files using the
vi(orvim) editor.-
In the /etc/krb5.conf file, fill in the
realms,domain_realmsections and thedefault_realmfield of thelibdefaultssection:$ sudo vi /etc/krb5.confThe file example is given below. In the
kdcandadmin_serverfields of therealmssection, specify the host where Kerberos KDC is being installed (with a port number). You can use IP addresses instead of host names:[libdefaults] default_realm = RU-CENTRAL1.INTERNAL dns_lookup_realm = false dns_lookup_kdc = false ticket_lifetime = 24h renew_lifetime = 7d forwardable = true default_tgs_enctypes = aes128-cts des3-hmac-sha1 des-cbc-crc des-cbc-md5 default_tkt_enctypes = aes128-cts des3-hmac-sha1 des-cbc-crc des-cbc-md5 permitted_enctypes = aes128-cts des3-hmac-sha1 des-cbc-crc des-cbc-md5 [realms] RU-CENTRAL1.INTERNAL = { kdc = bds-kerberos.ru-central1.internal:88 admin_server = bds-kerberos.ru-central1.internal:749 default_domain = ru-central1.internal } [domain_realm] .ru-central1.internal = RU-CENTRAL1.INTERNAL ru-central1.internal = RU-CENTRAL1.INTERNAL [appdefaults] pam = { debug = false ticket_lifetime = 36000 renew_lifetime = 36000 forwardable = true krb4_convert = false } -
In the /etc/krb5kdc/kdc.conf file, update the realm name in the
realmssection:$ sudo vi /etc/krb5kdc/kdc.confThe file example:
[kdcdefaults] kdc_ports = 750,88 [realms] RU-CENTRAL1.INTERNAL = { database_name = /var/lib/krb5kdc/principal admin_keytab = FILE:/etc/krb5kdc/kadm5.keytab acl_file = /etc/krb5kdc/kadm5.acl key_stash_file = /etc/krb5kdc/stash kdc_ports = 750,88 max_life = 10h 0m 0s max_renewable_life = 7d 0h 0m 0s #master_key_type = aes256-cts #supported_enctypes = aes256-cts:normal aes128-cts:normal default_principal_flags = +preauth }
-
-
Use the kdb5_util utility to create a Kerberos KDC database. This database is used to store keys for the Kerberos realms that are managed by the current KDC server. Use the
-soption to create a stash file: without that file, you will be requested a password every time the KDC server starts.$ sudo kdb5_util create -sAfter running the command, enter and confirm a password:
Loading random data Initializing database '/var/kerberos/krb5kdc/principal' for realm 'RU-CENTRAL1.INTERNAL', master key name 'K/M@RU-CENTRAL1.INTERNAL' You will be prompted for the database Master Password. It is important that you NOT FORGET this password. Enter KDC database master key: Re-enter KDC database master key to verify:
-
Create the
gpadmin/adminprincipal with administrative privileges in Kerberos KDC. To do this, use the kadmin.local utility:$ sudo kadmin.local -q "addprinc gpadmin/admin"After running the command, enter and confirm a password:
Authenticating as principal root/admin@RU-CENTRAL1.INTERNAL with password. WARNING: no policy specified for gpadmin/admin@RU-CENTRAL1.INTERNAL; defaulting to no policy Enter password for principal "gpadmin/admin@RU-CENTRAL1.INTERNAL": Re-enter password for principal "gpadmin/admin@RU-CENTRAL1.INTERNAL": Principal "gpadmin/admin@RU-CENTRAL1.INTERNAL" created.
-
To grant the appropriate permissions to the created principal, edit the /etc/krb5kdc/kadm5.acl file:
$ sudo vi /etc/krb5kdc/kadm5.aclFor example, the following file record means that any principal in the
RU-CENTRAL1.INTERNALrealm with a name ending with/adminhas all administrative privileges except key extraction:*/admin@RU-CENTRAL1.INTERNAL * -
Start Kerberos services by running the following commands:
$ sudo systemctl start krb5-admin-server $ sudo systemctl start krb5-kdc -
To check the status of Kerberos services, you can use these commands:
$ systemctl status krb5-admin-server $ systemctl status krb5-kdcThe result of the first command is shown below:
● krb5-admin-server.service - Kerberos 5 Admin Server Loaded: loaded (/lib/systemd/system/krb5-admin-server.service; enabled; vendor preset: enabled) Active: active (running) since Tue 2025-11-18 08:03:48 UTC; 2h 7min ago Main PID: 140489 (kadmind) Tasks: 1 (limit: 19050) Memory: 644.0K CPU: 38ms CGroup: /system.slice/krb5-admin-server.service └─140489 /usr/sbin/kadmind -nofork -
To make Kerberos start automatically upon the host restart, run the commands:
$ sudo systemctl enable krb5-admin-server $ sudo systemctl enable krb5-kdcThe result of the first command is shown below:
Synchronizing state of krb5-admin-server.service with SysV service script with /lib/systemd/systemd-sysv-install. Executing: /lib/systemd/systemd-sysv-install enable krb5-admin-server
Step 2. Create principals for ADB in MIT Kerberos KDC
In addition to the principal with administrative permissions (the creation of which is described above), you need to add Kerberos principals for all ADB users who will use Kerberos authentication. Since ordinary users do not need administrative access to the Kerberos server in most cases, you can use the kadmin utility to manage them (instead of kadmin.local). Examples in the following sections will use only one principal for demonstration purposes — gpadmin/admin@RU-CENTRAL1.INTERNAL (with one corresponding role in ADB — gpadmin/admin).
You should also add a service principal to Kerberos KDC, which corresponds not to the role, but to the postgres process on the ADB coordinator host. This principal is required when using Kerberos authentication with ADB. A principal name is formed according to the following template:
postgres/<coordinator_hostname>@<REALM>
where:
-
<coordinator_hostname>— a name of the ADB coordinator host, which can be obtained via thehostnamecommand. If this command returns the fully qualified domain name (FQDN), use it as the parameter value. -
<REALM>— a realm name in Kerberos.
Below is an example of adding a service principal:
$ sudo kadmin.local -q "addprinc postgres/bds-mdw@RU-CENTRAL1.INTERNAL"Result:
Authenticating as principal root/admin@RU-CENTRAL1.INTERNAL with password. WARNING: no policy specified for postgres/bds-mdw@RU-CENTRAL1.INTERNAL; defaulting to no policy Enter password for principal "postgres/bds-mdw@RU-CENTRAL1.INTERNAL": Re-enter password for principal "postgres/bds-mdw@RU-CENTRAL1.INTERNAL": Principal "postgres/bds-mdw@RU-CENTRAL1.INTERNAL" created.
When all required principals (including the service principal) are created, add them to the keytab file using the following command. This keytab file should be copied to the coordinator host of ADB later.
$ sudo kadmin.local -q "ktadd -k bds-kerberos.keytab postgres/bds-mdw@RU-CENTRAL1.INTERNAL gpadmin/admin@RU-CENTRAL1.INTERNAL"Result:
Authenticating as principal root/admin@RU-CENTRAL1.INTERNAL with password. Entry for principal postgres/bds-mdw@RU-CENTRAL1.INTERNAL with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:bds-kerberos.keytab. Entry for principal postgres/bds-mdw@RU-CENTRAL1.INTERNAL with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:bds-kerberos.keytab. Entry for principal gpadmin/admin@RU-CENTRAL1.INTERNAL with kvno 3, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:bds-kerberos.keytab. Entry for principal gpadmin/admin@RU-CENTRAL1.INTERNAL with kvno 3, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:bds-kerberos.keytab.
Step 3. Configure the ADB coordinator and check authentication
-
Install Kerberos client libraries on the ADB coordinator host:
$ sudo apt install krb5-user sssd-krb5 -
Copy the /etc/krb5.conf file contents from the Kerberos server to the /etc/krb5.conf file on the ADB coordinator host.
-
Copy the keytab file that was generated on the Kerberos server (bds-kerberos.keytab in the given example) to the /home/gpadmin/ directory on the ADB coordinator host. Set the ownership and permissions of the keytab file you copied as follows:
$ sudo chown gpadmin:gpadmin /home/gpadmin/bds-kerberos.keytab $ sudo chmod 400 /home/gpadmin/bds-kerberos.keytab -
Log in to the ADB coordinator host under the
gpadminuser and save a path to the keytab file in the server configuration parameter (GUC)krb_server_keyfile:$ sudo su - gpadmin $ gpconfig -c krb_server_keyfile -v '/home/gpadmin/bds-kerberos.keytab'Result:
20240523:10:50:32:008181 gpconfig:bds-mdw:gpadmin-[INFO]:-completed successfully with parameters '-c krb_server_keyfile -v /home/gpadmin/bds-kerberos.keytab'
-
Open the ADB service configuration page in ADCM. In the Custom pg_hba section field, add information about Kerberos authentication using the following format:
host all all 0.0.0.0/0 gss include_realm=0 krb_realm=RU-CENTRAL1.INTERNAL
For more information on the pg_hba.conf file format that is used for Kerberos authentication, see Step 4. Map Kerberos principals to ADB roles. The abovementioned entry allows connecting to all ADB databases from all hosts for those ADB roles whose names coincide with the principal names in the
RU-CENTRAL1.INTERNALrealm. Theinclude_realm=0option means the realm should be stripped from principal names before mapping with ADB role names.To apply changes, click Save and run the ADB service action Reconfigure.
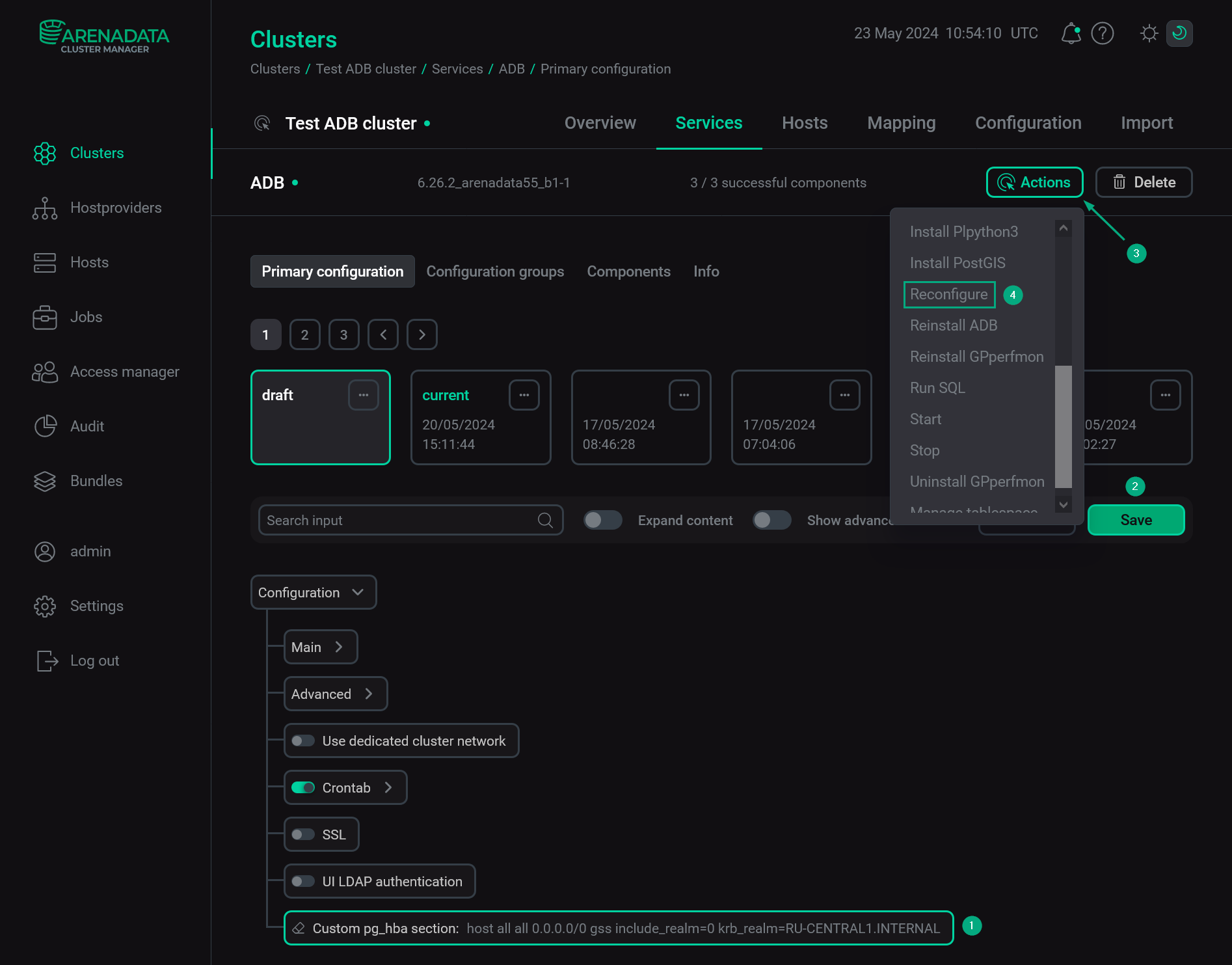 Configure Kerberos authentication for ADB via ADCMNOTEThe
Configure Kerberos authentication for ADB via ADCMNOTEThe0.0.0.0/0address is used for test needs only. It is not recommended for production environments. -
Create the
gpadmin/adminsuperuser role in ADB. This role will be mapped to the gpadmin/admin@RU-CENTRAL1.INTERNAL principal in Kerberos:$ createuser gpadmin/admin --superuser -
Using the kinit command, create a ticket granting ticket (TGT) for the
gpadmin/admin@RU-CENTRAL1.INTERNALprincipal:$ kinit -k -t /home/gpadmin/bds-kerberos.keytab gpadmin/admin@RU-CENTRAL1.INTERNALNOTEIn this and the following examples, the previously created keytab file is used when a ticket is requested (see the-kand-toptions). In practice, keytab files are most commonly used for service accounts. Ordinary users can callkinitwithout arguments — in this case, they need to enter the password specified for the corresponding principals in Kerberos. The next steps are the same. -
Check the ticket existence in the ticket cache via the klist command:
$ klistThe result contains the obtained TGT:
Ticket cache: FILE:/tmp/krb5cc_2042 Default principal: gpadmin/admin@RU-CENTRAL1.INTERNAL Valid starting Expires Service principal 05/23/2024 15:23:38 05/24/2024 15:23:37 krbtgt/RU-CENTRAL1.INTERNAL@RU-CENTRAL1.INTERNAL
-
Log in to the
adbdatabase under thegpadmin/adminrole viapsql:$ psql adb -U "gpadmin/admin" -h bds-mdw -
Select the current user name to verify that authentication is successful:
SELECT current_user;Result:
current_user --------------- gpadmin/admin
-
If you quit
psqland runklistagain, the command result will contain not only a TGT, but also a ticket granting service (TGS), which is needed to implement the Kerberos authentication protocol in ADB (see postgres/bds-mdw@RU-CENTRAL1.INTERNAL):Ticket cache: FILE:/tmp/krb5cc_2042 Default principal: gpadmin/admin@RU-CENTRAL1.INTERNAL Valid starting Expires Service principal 05/23/2024 15:23:38 05/24/2024 15:23:37 krbtgt/RU-CENTRAL1.INTERNAL@RU-CENTRAL1.INTERNAL 05/23/2024 15:24:03 05/24/2024 15:23:37 postgres/bds-mdw@ 05/23/2024 15:24:03 05/24/2024 15:23:37 postgres/bds-mdw@RU-CENTRAL1.INTERNAL
NOTEThe additional entry with the empty realm name (postgres/bds-mdw@) is not an error. This is an artifact of the way how host referrals were introduced in krb5 later than 1.6.
Step 4. Map Kerberos principals to ADB roles
In the example listed above, the following template is used to add credentials for the Kerberos authentication to the pg_hba.conf file:
host <database> <user> <address> <auth-method> [<auth-options>]For detailed information on each attribute of this entry, as well as for other possible attributes, see The pg_hba.conf File article in the PostgreSQL documentation. Below, we will focus only on the <auth-options> specific for the GSSAPI protocol, which is used for Kerberos authentication. By combining these options, you can choose the most appropriate way to map Kerberos principals to ADB users:
-
include_realm— if set to0, a realm name is excluded from Kerberos principal names before being passed through the mapping with ADB role names; if set to1— a realm name is included. The usage of0is not secure in multi-realm environments (unless thekrb_realmoption is used). It is recommended to setinclude_realm=1and use themapoption to convert Kerberos principal names to ADB role names based on the pg_ident.conf file. -
krb_realm— a name of the Kerberos realm. If this parameter is set, only principals of that realm will be accepted. -
map— a name of the custom mapping that allows you to explicitly map Kerberos principals to ADB roles in the pg_ident.conf file of the ADB coordinator data directory. Each mapping requires the following format:# MAPNAME SYSTEM-USERNAME PG-USERNAME <map_name> <principal_name> <role_name>where:
-
<map_name>— a mapping name that should be specified in the pg_hba.conf file:map=<map_name>. -
<principal_name>— a name of the Kerberos principal. Should include the realm name (after@) ifinclude_realm=1. -
<role_name>— a role name in ADB.
-
The following example shows how to map Kerberos principals to ADB roles via the map option:
-
Connect to the coordinator host under the
gpadminuser and create a new usermyadmin:$ createuser "myadmin" --superuser; -
In the coordinator data directory, open the pg_ident.conf file:
$ cd /data1/master/gpseg-1 $ vi pg_ident.conf -
Add the
mymapmapping to the file:# MAPNAME SYSTEM-USERNAME PG-USERNAME mymap gpadmin/admin@RU-CENTRAL1.INTERNAL myadmin -
Open the ADB service configuration page in ADCM. In the Custom pg_hba section field, replace the previously added value of the Custom pg_hba section field by the following record:
host all all 0.0.0.0/0 gss include_realm=1 krb_realm=RU-CENTRAL1.INTERNAL map=mymapNote that
include_realm=1. If the option value is0, the previous step would require to use another record:# MAPNAME SYSTEM-USERNAME PG-USERNAME mymap gpadmin/admin myadmin -
Click Save to save changes and run the Reconfigure action of the ADB service.
CAUTIONYou should run the Reconfigure action each time you edit the pg_ident.conf file or the Custom pg_hba section value. -
Remove existing tickets (if any) via the kdestroy command:
$ kdestroy -
Using the
kinitcommand, create a TGT for thegpadmin/admin@RU-CENTRAL1.INTERNALprincipal:$ kinit -k -t /home/gpadmin/bds-kerberos.keytab gpadmin/admin@RU-CENTRAL1.INTERNAL -
Ensure you can connect to the database using the
myadminrole:$ psql adb -U "myadmin" -h bds-mdw -
After you successfully connected to ADB, quit
psqland runklistto ensure the service ticket is available:$ klistResult:
Ticket cache: FILE:/tmp/krb5cc_2042 Default principal: gpadmin/admin@RU-CENTRAL1.INTERNAL Valid starting Expires Service principal 05/24/2024 07:21:57 05/25/2024 07:21:57 krbtgt/RU-CENTRAL1.INTERNAL@RU-CENTRAL1.INTERNAL 05/24/2024 07:22:15 05/25/2024 07:21:57 postgres/bds-mdw@ 05/24/2024 07:22:15 05/25/2024 07:21:57 postgres/bds-mdw@RU-CENTRAL1.INTERNAL
Step 5. Configure Kerberos authentication for client applications
After Kerberos authentication is configured, client applications need Kerberos tickets for connecting to ADB. On the client side, the kinit utility is used to generate tickets. To make this utility work, you should copy the krb5-conf configuration file and the keytab file from the Kerberos side and install Kerberos client libraries on the host, where the ADB connection is being configured. The following is an example of configuring a host with Ubuntu 22.04 and connecting from that host to ADB via psql:
-
Install Kerberos client libraries on the host, from which you need to connect to the ADB database:
$ sudo apt install krb5-user sssd-krb5 -
Copy the /etc/krb5.conf contents from Kerberos to the /etc/krb5.conf file on the client host.
-
Copy the keytab file previously created on the Kerberos server (bds-kerberos.keytab) to the home directory of the current user (/home/gpadmin/ in the given example).
-
Connect to the host under the user, whose home directory contains the keytab file (
gpadminin the given example).$ sudo su - gpadmin -
Request a TGT for the
gpadmin/admin@RU-CENTRAL1.INTERNALprincipal via thekinitcommand:$ kinit -k -t /home/gpadmin/bds-kerberos.keytab gpadmin/admin@RU-CENTRAL1.INTERNAL -
Check that you can connect to the ADB database using the
myadminrole, which creation was described in Step 4. Map Kerberos principals to ADB roles:$ psql adb -U "myadmin" -h bds-mdw -
After you successfully connected to ADB, quit
psqland runklistto ensure the service ticket is available:$ klistResult:
Ticket cache: FILE:/tmp/krb5cc_2042 Default principal: gpadmin/admin@RU-CENTRAL1.INTERNAL Valid starting Expires Service principal 05/30/2024 13:07:02 05/31/2024 13:07:00 krbtgt/RU-CENTRAL1.INTERNAL@RU-CENTRAL1.INTERNAL 05/30/2024 13:07:15 05/31/2024 13:07:00 postgres/bds-mdw@ 05/30/2024 13:07:15 05/31/2024 13:07:00 postgres/bds-mdw@RU-CENTRAL1.INTERNAL
Step 6. Configure JDBC connections
The JDBC access from Java applications to ADB databases with Kerberos authentication is performed via the Java authentication and authorization service (JAAS). Below you can find how to configure and run a simple Java application on a host with the Ubuntu 22.04 operating system. The application selects table data from ADB. The PostgreSQL JDBC driver is used to connect to ADB:
-
Connect to the
adbdatabase on the coordinator host and create a test table that will be used in your Java application:CREATE TABLE book_type(id INT PRIMARY KEY, name TEXT UNIQUE NOT NULL) DISTRIBUTED REPLICATED; -
Add some data to the test table:
INSERT INTO book_type VALUES(1,'novel'),(2,'non-fiction'),(3,'fantastic'); -
On the host where you plan to run the Java application, follow all steps described in Step 5. Configure Kerberos authentication for client applications. At the end, check that you are log in under the user for whom the tickets were created (
gpadminin the given example):$ sudo su - gpadmin -
Ensure that Java is installed:
$ java -versionIn the given example, Java 11 is used:
openjdk version "11.0.23" 2024-04-16 LTS OpenJDK Runtime Environment (Red_Hat-11.0.23.0.9-2.el7_9) (build 11.0.23+9-LTS) OpenJDK 64-Bit Server VM (Red_Hat-11.0.23.0.9-2.el7_9) (build 11.0.23+9-LTS, mixed mode, sharing)
-
Create the .java.login.config file in the home directory of the current user (/home/gpadmin in the given example):
$ vi .java.login.configThe file contents are listed below. The purpose of all file options can be found in the Class Krb5LoginModule documentation.
pgjdbc { com.sun.security.auth.module.Krb5LoginModule required doNotPrompt=true useTicketCache=true debug=true client=true; }; -
Create the application file:
$ vi test.javaThe application code is shown below. This program connects to the
adbdatabase on thebds-mdwcoordinator host using the PostgreSQL JDBC driver. Then, thenamecolumn is read from all tuples of thebook_typetable:import java.sql.*; public class Test { public static void main(String []args) throws Exception { Class.forName("org.postgresql.Driver"); String url = "jdbc:postgresql://bds-mdw:5432/adb?kerberosServerName=postgres&jaasApplicationName=pgjdbc&user=myadmin"; try ( Connection conn = DriverManager.getConnection(url) ){ try ( Statement statement = conn.createStatement() ) { try (ResultSet rs = statement.executeQuery( "SELECT name FROM book_type") ){ while (rs.next()) System.out.println( "Get String: " + rs.getString(1)); } } } } } -
Upload the JAR file of the PostgreSQL JDBC driver and specify its location in the
CLASSPATHenvironment variable:$ export CLASSPATH=.:/home/gpadmin/postgresql-42.7.3.jar -
Run the application:
$ java test.javaThe successful result is shown below:
Debug is true storeKey false useTicketCache true useKeyTab false doNotPrompt true ticketCache is /tmp/krb5cc_2042 isInitiator true KeyTab is null refreshKrb5Config is false principal is null tryFirstPass is false useFirstPass is false storePass is false clearPass is false Acquire TGT from Cache Principal is gpadmin/admin@RU-CENTRAL1.INTERNAL Commit Succeeded Get String: novel Get String: non-fiction Get String: fantastic