

Configure a cluster
|
IMPORTANT
There is usually no need to change cluster configuration parameters. You can leave all parameters at the default values.
|
After creation a new cluster, you can configure it by performing the following steps:
-
Select a cluster on the Clusters page. To do this, click a cluster name in the Name column.
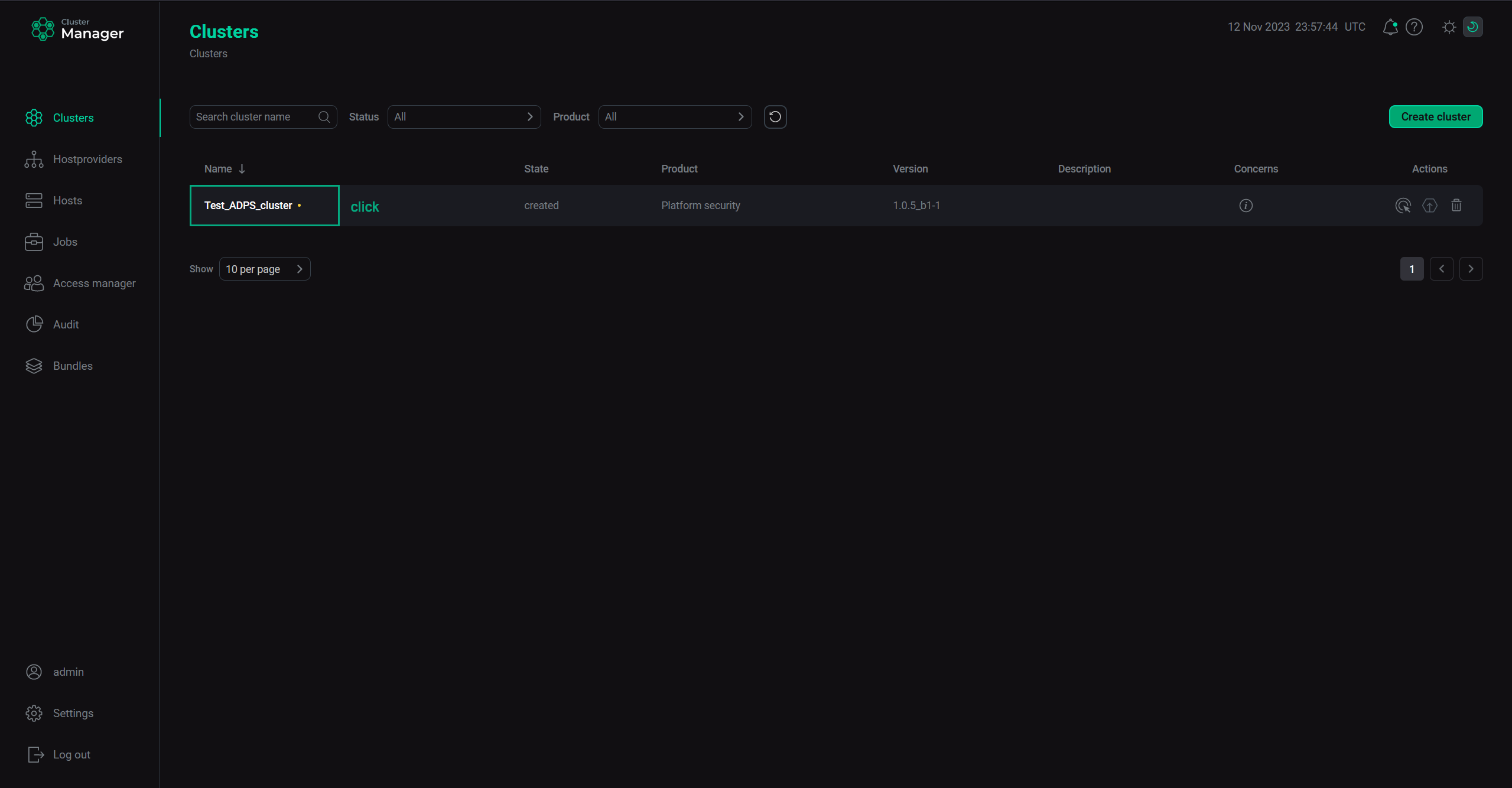 Select a cluster
Select a cluster -
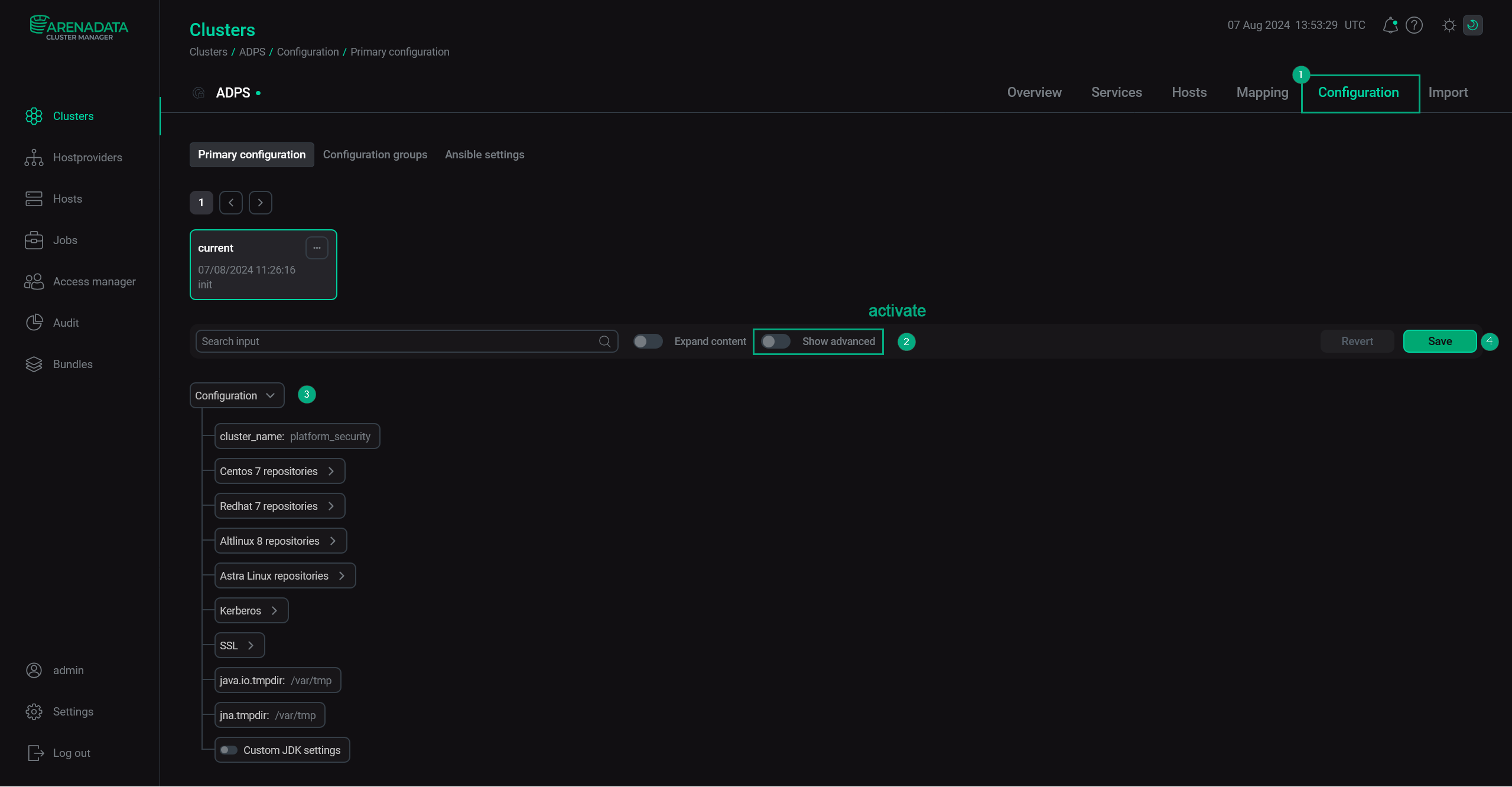
Open the Configuration tab on the cluster page. The Configuration tab includes the following sections: Primary configuration, Configuration groups, Ansible settings.
-
Fill in all necessary parameters on the selected tab and click Save.
Primary configuration
The Configuration → Primary configuration tab allows you to configure the general cluster settings.
Available configuration parameters are listed below:
-
Paths to the repositories for CentOS, Red Hat, ALT Linux 8, and Astra Linux that are used in the process of installing — depending on the cluster operation system:
-
monitoring — monitoring components repository;
-
zookeeper_repo — Arenadata Zookeeper YUM repository;
-
arenadata — Arenadata YUM repository.
-
-
The Kerberos section that includes settings listed in the table below.
Parameter Description Default value Enable Kerberos
Enables the Kerberos authentication
False
Authentication on WEB UIs
Enables the Kerberos authentication on WEB UIs
False
SPNEGO Signature Value
A secret key that is used to generate and verify the signature in the HTTP authentication protocol SPNEGO (in the Base64 format)
—
Kerberos KDC type
A KDC type. For more information, see Kerberos
MIT
KDC hosts
One or more KDC hosts with running FreeIPA server(s)
—
Realm
A Kerberos realm to connect to the FreeIPA server
—
Domains
One or more domains associated with FreeIPA
—
Kadmin server
A host where
kadminis running—
Kadmin principal
A principal name used to connect via
kadmin, for exampleadmin@RU-CENTRAL1.INTERNAL—
Kadmin password
An IPA Admin password
—
Keytabs directory
A directory with keytab files
/etc/security/keytabs
Additional realms
Additional Kerberos realms
—
Delay between kinit invocation attempts
Time to wait before attempting another kinit operation if the previous one has failed
5
Number of retries for kinit invocation attempts
Number of attempts to launch the kinit command if it fails
10
Trusted Active Directory server
An Active Directory server for one-way cross-realm trust from the MIT Kerberos KDC
—
Trusted Active Directory realm
An Active Directory realm for one-way cross-realm trust from the MIT Kerberos KDC
—
Custom krb5.conf
Enables adding custom parameters to the krb5.conf file
False
krb5.conf
Additional parameters to write to the krb5.conf file
—
Admin DN
A full DistinguishedName of the admin user with rights to
create/modify/delete/pwdchangeuser accounts in the target Organizational Unit—
LDAP URL
LDAP URL that consists of the
ldap://orldaps://protocol prefix, hostname or IP address and port of an AD server. For example,ldaps://192.168.4.2:636—
Container DN
A container distinguished name
—
TLS CA certificate Path
A CA certificate path on the host filesystem that is pre-located or should be written from the TLS CA certificate field
—
TLS CA certificate (optional)
A CA certificate that is written on a host by the path from TLS CA certificate Path during the execution of the Enable Kerberos action. The certificate is not saved in ADCM
—
Custom ldap.conf
Enables adding custom parameters to the ldap.conf file
False
ldap.conf
Additional parameters that are written to the ldap.conf file
—
IpaClient No NTP Autoconf
Disables the NTP configuration during the IPA client installation
False
IpaClient No DNS Lookup
Disables the DNS lookup for the FreeIPA server during the IPA client installation
True
Set up Kerberos utils
Defines whether to install or remove the Kerberos client and utils
True
Configure Kerberos on hosts
Cluster configuration including krb5.conf and ldap.conf
True
Set up principals and keytabs
Defines whether to create, re-create, or remove principals and keytabs
True
Configure services and clients
Defines whether to update the services and clients configuration
True
Run service checks
Defines whether to run the service checks
True
-
The SSL section with the settings listed in the table below.
Parameter Description Default value Enable SSL
Indicates whether SSL is enabled or not
False
Keystore path
A path to the keystore file
/tmp/keystore.jks
Keystore password
A password for the keystore file
—
Truststore path
A path to the truststore file
/tmp/truststore.jks
Truststore password
A password for the truststore file
—
TLS Version
Version of the TLS protocol
TLSv1.2
Run service checks
Defines whether to run the service checks
True
-
The Advanced SSL section with the settings listed in the table below.
Parameter Description Default value Java cacerts file location
Path to the cacerts file location of your Java distribution
/etc/pki/ca-trust/extracted/java/cacerts
Java cacerts file password
Password for the cacerts file of your Java distribution
—
-
The java.io.tmpdir parameter that specifies an environment variable to control
java.io.tmpdirfor Solr. -
The jna.tmpdir parameter that specifies an environment variable to control
jna.tmpdirfor Solr. -
The Custom JDK settings group of parameters specifies the custom Java path.
Configuration groups
The Configuration → Configuration groups tab is designed to set cluster configuration groups.
Ansible settings
The Configuration → Ansible settings tab allows you to set Ansible configuration options at the cluster level. The tab is available starting with ADCM 2.2.0.
| Name | Description | Default |
|---|---|---|
forks |
The number of parallel processes to spawn when communicating with remote hosts |
5 |