

Password encryption
Overview
JCEKS is an improved file-based keystore format introduced with the Java Cryptography Extension (JCE). It provides a stronger protection due to Triple DES encryption, which makes it a better alternative to JKS. Even if a store is not protected by a password (in ADCM, password are used by default), an adversary would be unable to extract plaintext data from it.
|
IMPORTANT
Starting with ADPS 1.1.1.b1, all ADPS passwords are stored in JCEKS files (i.e. credential stores) instead of configuration files.
|
Below, you can find more details about this feature for each service.
Ranger
Ranger has two options to deal with a credstore password: use a password file or use no password. By default, the password file is used. You can change this parameter in ADCM.
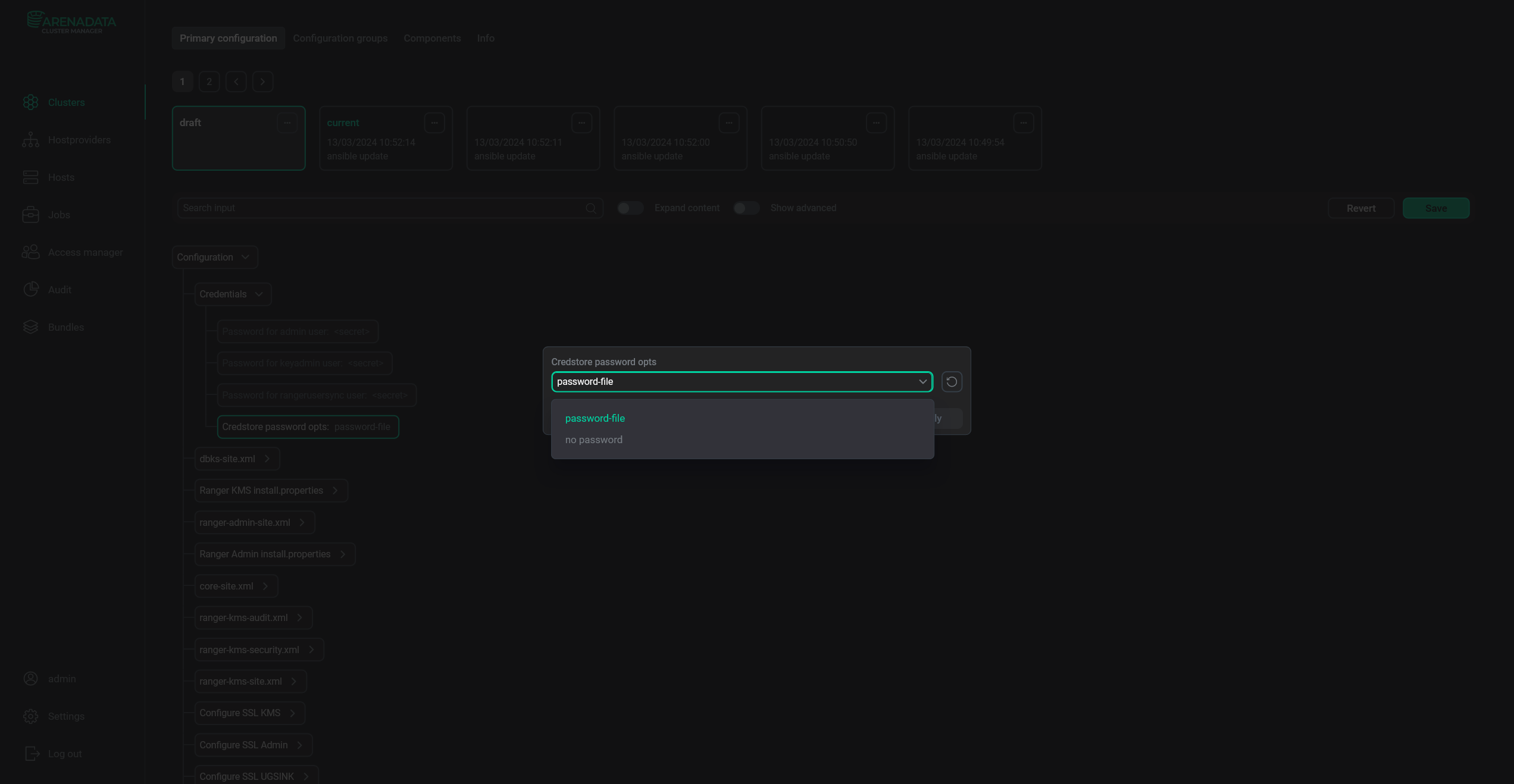
A credential store password is autogenerated and stored in a password file defined separately for each service. Its location is /etc/ranger/<service_name>/conf/encrypt_pass, where <service_name> is the name of a Ranger service.
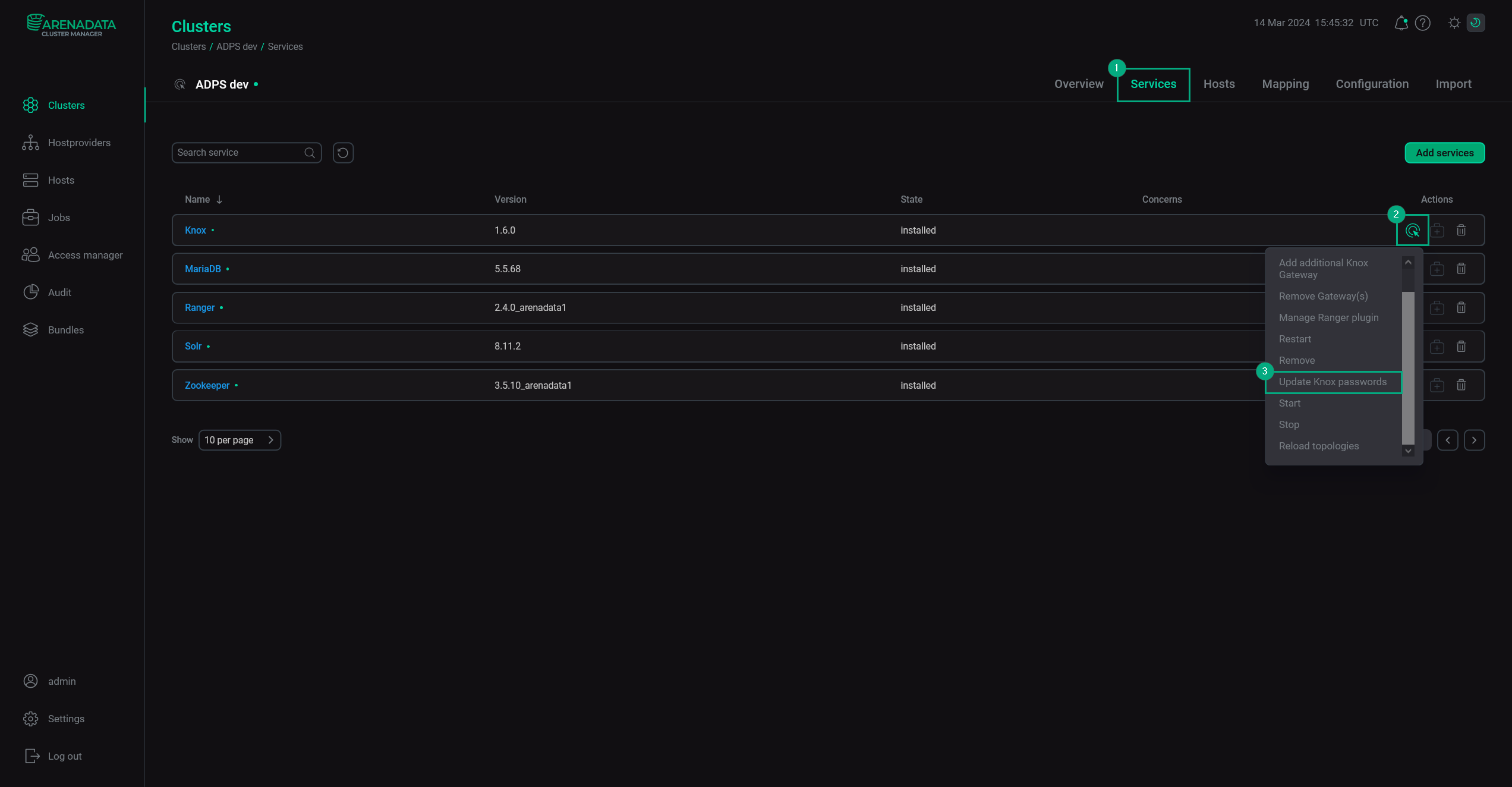
Knox
Passwords for each cluster topology are stored in /usr/lib/knox/data/security/keystores/. All cluster’s JCEKS files are secured by the Knox master password. A password for the Knox Ranger plugin is stored in /etc/knox/conf/ranger-knox.jceks file which is created if both SSL and the Knox Ranger plugin are enabled. To apply Knox passwords that were changed manually (without the Enable SSL action or enabling LDAP), it’s required to run the Update passwords action.
Solr
Solr has all of its passwords in a JCEKS file, while the password for it is stored in the environment.
|
NOTE
By default, the encryption is active for all the services except Solr. To turn it on for Solr, activate the Credential encryption switch in the service configuration and restart Solr with the Update jceks parameter set to true.
|