

Enable SSL on ADPS cluster with Knox
Prerequisites
Before you move on to enable SSL for your ADPS cluster, follow the steps below:
-
Make sure that your hosts have the truststore.jks and keystore.jks files.
-
Create a certificate for each node using the RSA algorithm. The key length should be 2048 bit, CN should be the FQDN of the corresponding node. It is not recommended to use the DSA algorithm. It is also not recommended to use the ECDSA algorithm due to this algorithm not being widely supported by certification centers.
You can use the script below to generate and place self-signed certificates where they need to be.
#!/bin/bash
# Script for generating and import self-signed certificates to java keystore and openssl ca-bundle
# Edit NUMHOSTS and HOSTS as it will be suitable for your case.
declare -a NUMHOSTS
declare -a HOSTS
SSH_OPTS='-o GlobalKnownHostsFile=/dev/null -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no'
NUMHOSTS=(1 2 3)
HOSTS=$(for i in "${NUMHOSTS[@]}"; do echo "adps-$i.ru-central1.internal"; done)
echo Generate keystore.jks on each host
for HOST in $HOSTS; do
echo "Generating keypair"
ssh $SSH_OPTS $HOST "keytool -genkeypair -noprompt -keyalg RSA \
-alias $HOST -dname \"CN=$HOST, OU=AD, O=AD, L=MSK, S=MO, C=RU\" \
-keystore /tmp/keystore.jks -storepass bigdata -keypass bigdata -validity 360 -keysize 2048";
done
echo
echo Export certificates
for HOST in $HOSTS;do
ssh $SSH_OPTS $HOST "keytool -exportcert -file /tmp/$HOST.crt -keystore /tmp/keystore.jks -storepass bigdata -alias $HOST -rfc";
done
echo
echo Collect all certificates
for HOST in $HOSTS; do
scp $SSH_OPTS $HOST:/tmp/$HOST.crt /tmp/
done
echo
echo Transfer certificates on hosts
for HOST in $HOSTS; do
scp $SSH_OPTS /tmp/*.crt $HOST:/tmp/
done
echo
echo Import certificates on each host
for HOST in $HOSTS; do
ssh $SSH_OPTS $HOST "for CERT in $(echo ${HOSTS[*]}); do
keytool -importcert -noprompt -alias \$CERT -file /tmp/\$CERT.crt -keystore /tmp/truststore.jks -storepass bigdata;
sudo bash -c \"cat /tmp/\$CERT.crt >> /etc/pki/tls/certs/ca-bundle.crt\";
done";
done
echo
echo Import truststore to Java CA store
for HOST in $HOSTS; do
ssh $SSH_OPTS $HOST "sudo keytool -importkeystore -noprompt -srckeystore /tmp/truststore.jks \
-destkeystore /etc/pki/java/cacerts -deststorepass changeit -srcstorepass bigdata"
done
echo
echo Create and import OpenSSL cert for Nginx
for HOST in $HOSTS; do
ssh $SSH_OPTS $HOST "sudo openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 \
-subj \"/C=RU/ST=Denial/L=MSK/O=AD/CN=$HOST\" \
-keyout /etc/ssl/host_cert.key -out /etc/ssl/certs/host_cert.cert"
ssh $SSH_OPTS $HOST "sudo bash -c \"cat /etc/ssl/certs/host_cert.cert >> /etc/pki/tls/c
erts/ca-bundle.crt\""
doneEnable SSL
To enable SSL on ADPS cluster, follow these steps:
-
On the Clusters page, click the name of the installed ADPS cluster.
 Switch to cluster page
Switch to cluster page -
Open the Services tab and choose Knox.
 Switch to Knox
Switch to Knox -
In the service menu, choose Configuration and scroll down to the Configure SSL Knox Gateway section. Find the gateway.tls.key.alias parameter and change its default value (
gateway-identity) to the actual alias for Knox host (e.g. FQDN of Knox). You can also clear the field (click theicon on the left so that the parameter value becomes
<not set>) to configure the value automatically. After that click Save.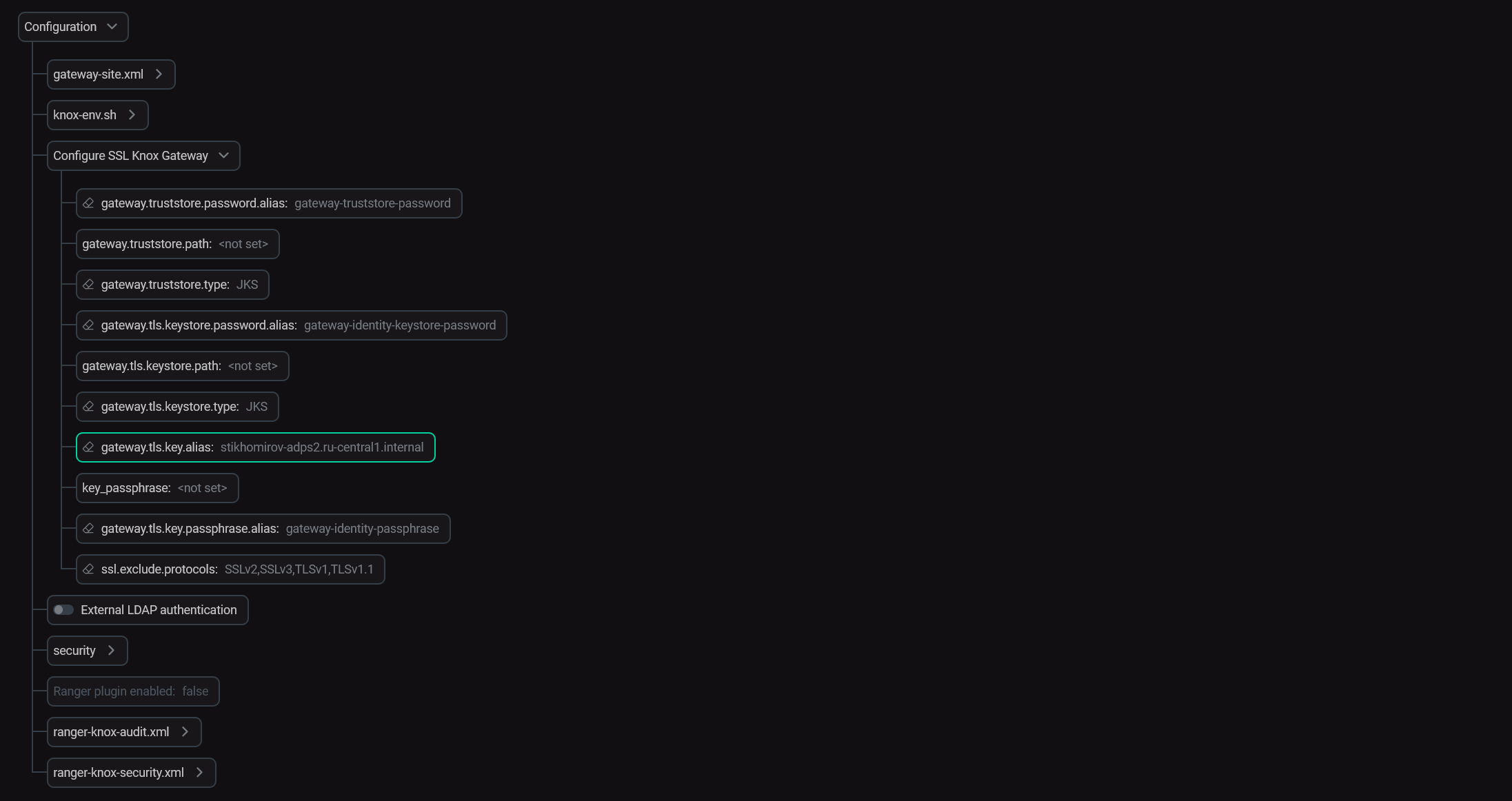 Configure KnoxTIPYou can read more about these parameters in the Configuration parameters article in the Knox → Configure SSL Knox Gateway section.
Configure KnoxTIPYou can read more about these parameters in the Configuration parameters article in the Knox → Configure SSL Knox Gateway section. -
Go to the Clusters page and choose the Manage SSL action for your ADPS cluster.
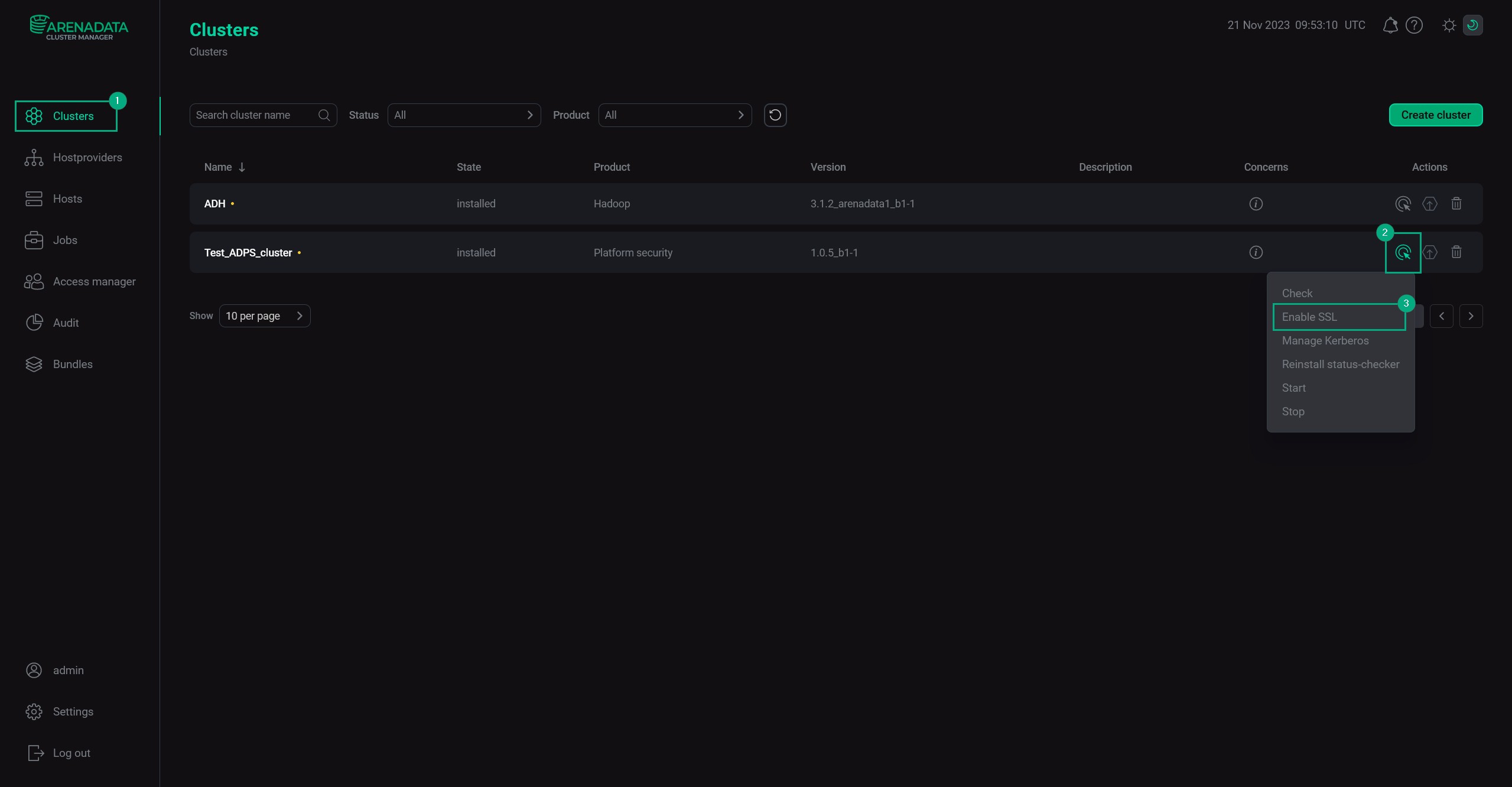 Enable SSL
Enable SSL -
In the pop-up window, specify the keystore and truststore parameters. Then, click Run.
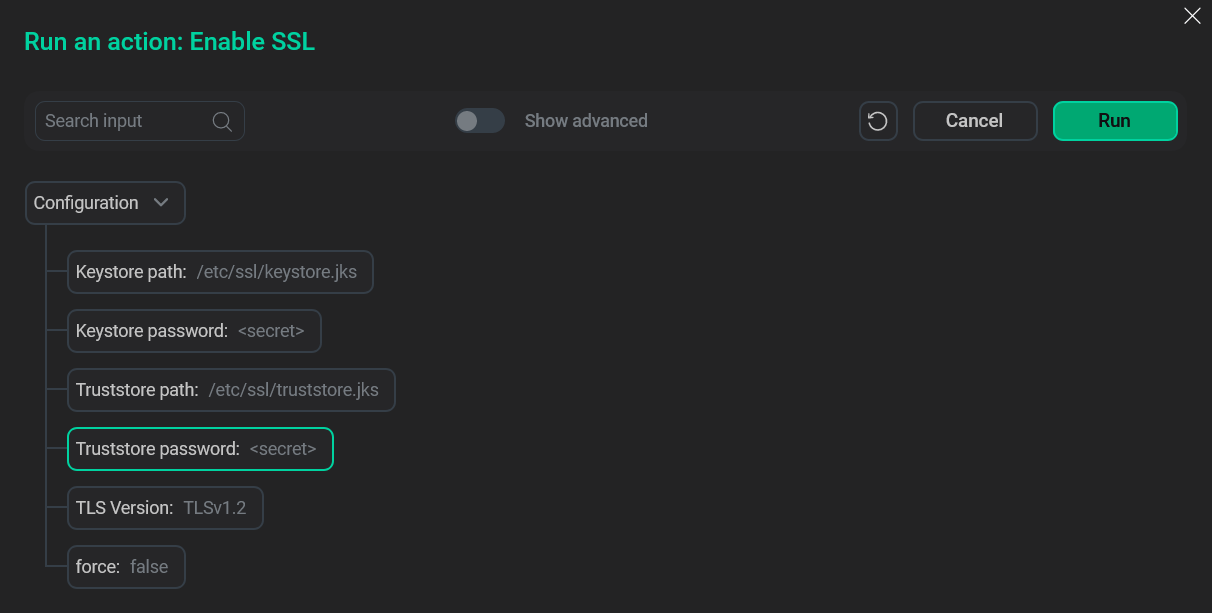 Specify the keystore and truststore parameters
Specify the keystore and truststore parameters -
You can monitor the process on the Jobs page and once it’s finished successfully — SSL will be enabled.
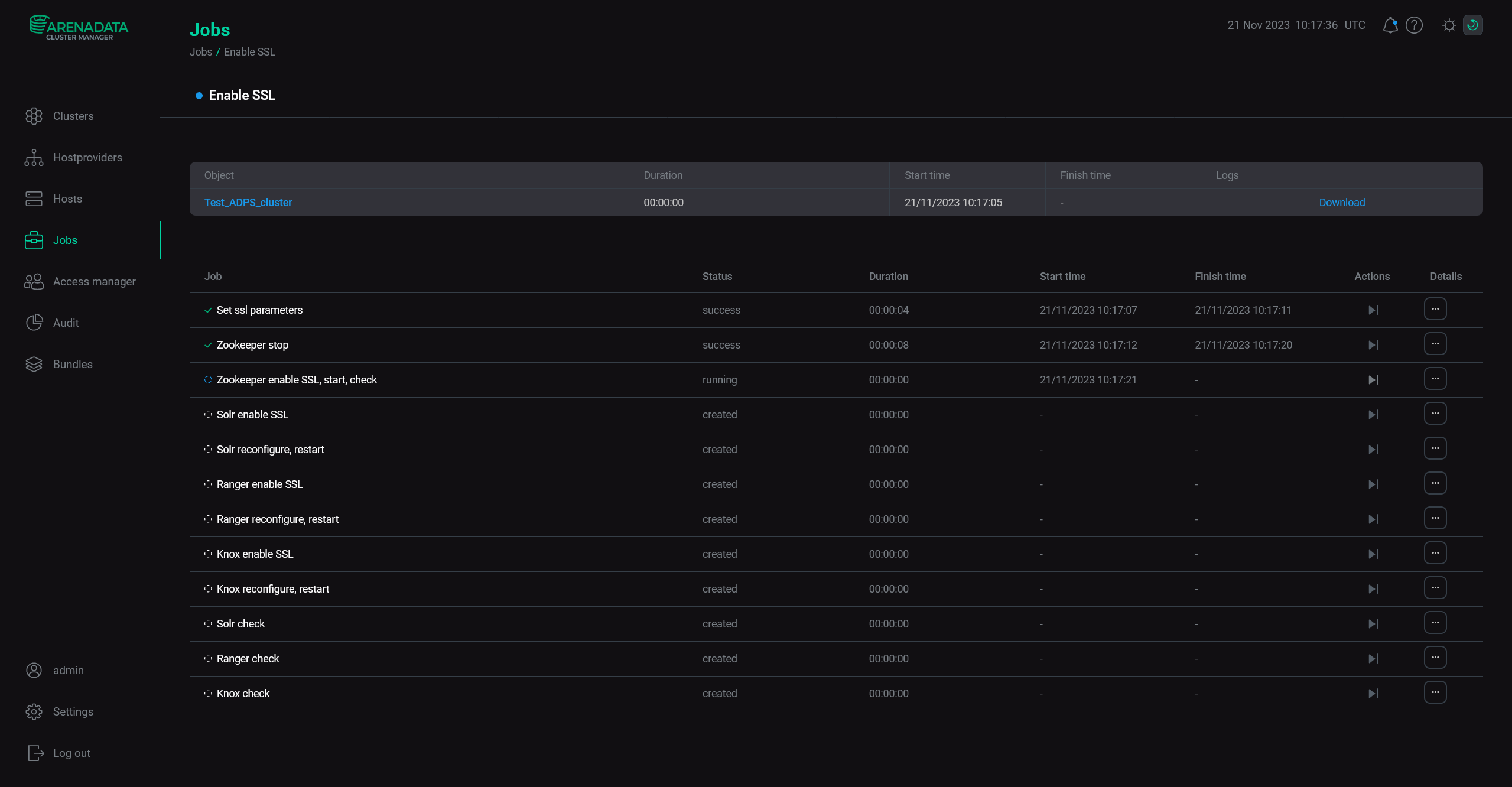 Monitor the job
Monitor the job
|
NOTE
If the process fails, try restarting Knox and retrying the failed action. |