

Use FreeIPA for Kerberos
FreeIPA is a free open source identity management system for Linux/UNIX environments. FreeIPA relies on Linux (Fedora), 389 Directory Server, MIT Kerberos, NTP, DNS, Dogtag (certificate system) and its main purpose is to provide centralized account management and authentication.
To ensure security, ADQM uses Kerberos, LDAP, SSL certificates/keys, and other related technologies. For such set of tools, FreeIPA is a good fit as an identity management system.
To enable FreeIPA for an ADQM cluster, use ADCM. During kerberization, ADCM installs IPA clients on each cluster node and connects clients to the FreeIPA server using the provided FreeIPA Kerberos parameters.
In this tutorial, a sample single-noded FreeIPA server is used to demonstrate an example. It is deployed on the freeipa-server.ru-central1.internal host with the CentOS operating system. This is a basic FreeIPA installation (yum install ipa-server) with default installation parameters.
Start FreeIPA on ADQM cluster
To kerberize a cluster using FreeIPA, follow the steps below:
-
On the Clusters page of the ADCM interface, select the installed and prepared ADQM cluster.
-
Enable Kerberos for the cluster — click the Actions
icon and select the Manage Kerberos action.
 Manage Kerberos action
Manage Kerberos action -
Turn on the Existing FreeIPA option and specify FreeIPA Kerberos parameters.
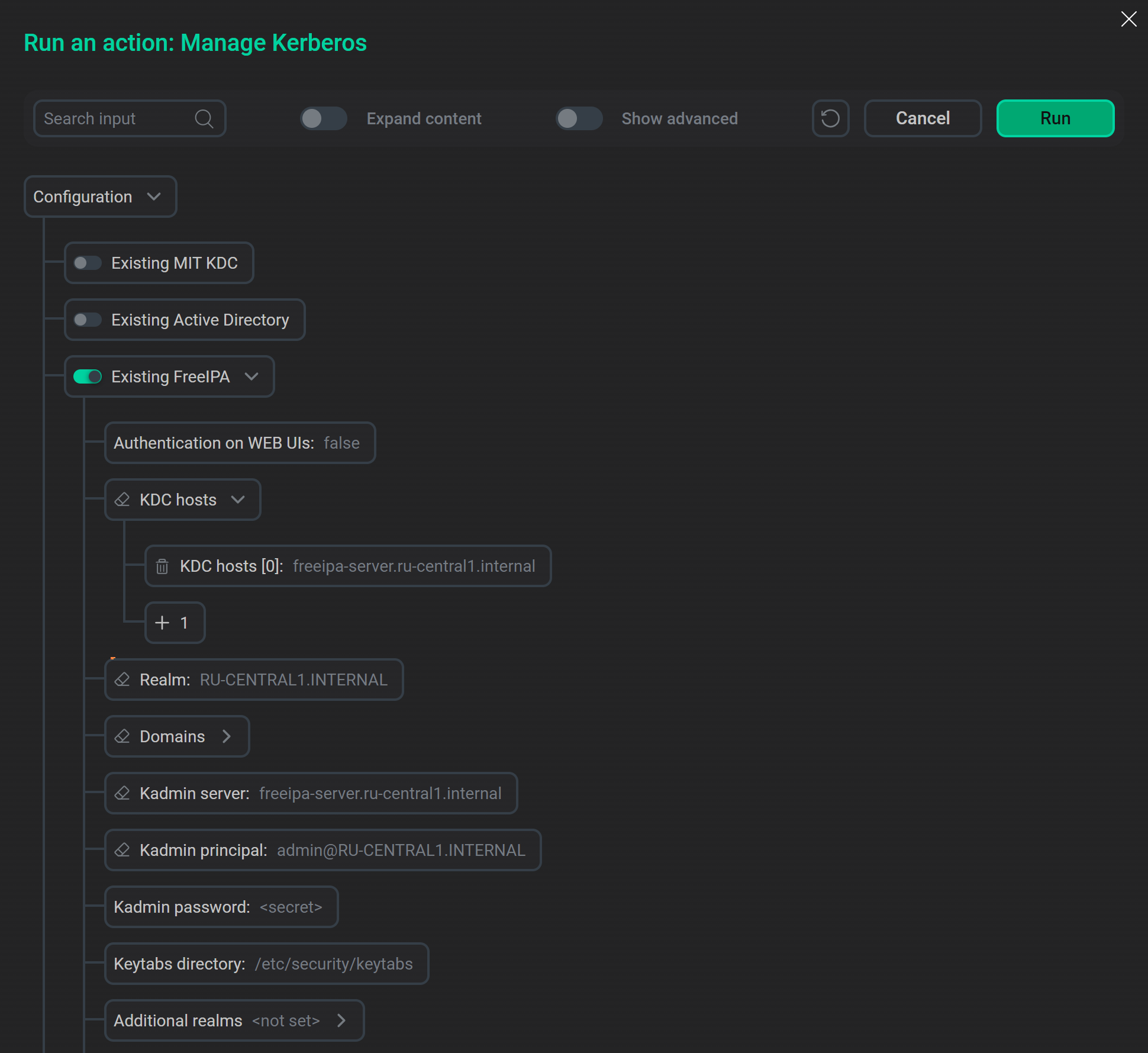 FreeIPA parameters
FreeIPA parameters -
Click Run and wait for the cluster kerberization to complete. On the Jobs page, you can monitor the progress and result of the Manage Kerberos task execution.
After Kerberos is successfully installed on the ADQM cluster, the corresponding settings appear on the cluster configuration page (in the Kerberos section) and on the ADQMDB service configuration page (in the Kerberos configuration section).
FreeIPA Kerberos parameters
The following parameters are required to kerberize an ADQM cluster with FreeIPA. To obtain actual values for these parameters, you can run ipa user-find <ipa_admin> on your FreeIPA server, where <ipa_admin> is the IPA Admin username.
| Parameter | Description |
|---|---|
KDC hosts |
One or more KDC hosts with running FreeIPA server(s) |
Realm |
Kerberos realm to connect to the FreeIPA server |
Domains |
One or more domains associated with FreeIPA |
Kadmin server |
Host where |
Kadmin principal |
Principal name used to connect via |
Kadmin password |
IPA Admin password |
IpaClient No NTP Autoconf |
Disables the NTP configuration during the IPA client installation |
IpaClient No DNS Lookup |
Disables the DNS lookup for FreeIPA server during the IPA client installation |
Check FreeIPA integration
After a successful kerberization, ADQM commands can only run on cluster nodes after getting a Kerberos ticket. Below is an example that demonstrates how to access the cluster kerberized with FreeIPA:
-
Create an ADQM user that matches an account existing in the FreeIPA domain. To do this, use the
IDENTIFIED WITH kerberosclause in theCREATE USERquery:CREATE USER adqm_kerb_freeipa IDENTIFIED WITH kerberos; -
Create a Kerberos ticket for the user principal:
$ kinit adqm_kerb_freeipa@RU-CENTRAL1.INTERNALEnter a password:
Password for adqm_kerb_freeipa@RU-CENTRAL1.INTERNAL:The kinit article of the MIT Kerberos documentation describes all available options of the
kinitcommand. -
Check the ticket:
$ klistTicket cache: FILE:/tmp/krb5cc_1000 Default principal: adqm_kerb_freeipa@RU-CENTRAL1.INTERNAL Valid starting Expires Service principal 05/10/2023 10:20:30 05/11/2023 10:20:30 krbtgt/RU-CENTRAL1.INTERNAL@RU-CENTRAL1.INTERNAL
-
To test authentication via Kerberos, send some command to ADQM using the
curlutility version that supports the SPNEGO mechanism:$ echo "select currentUser()" | curl --negotiate -u : http://<host_name>:8123/ --data-binary @-In case of successful authentication, the command should return the kerberized user name:
adqm_kerb_freeipa