OpenBao UI overview
Overview
Each OpenBao Server instance has an available web interface. You can find the links to them in ADCM:
-
On the Clusters page, select your ADPS cluster and head to the Services tab.
-
In the list of services, select OpenBao.
-
Head to the Info tab. The links are available in the Web links section.
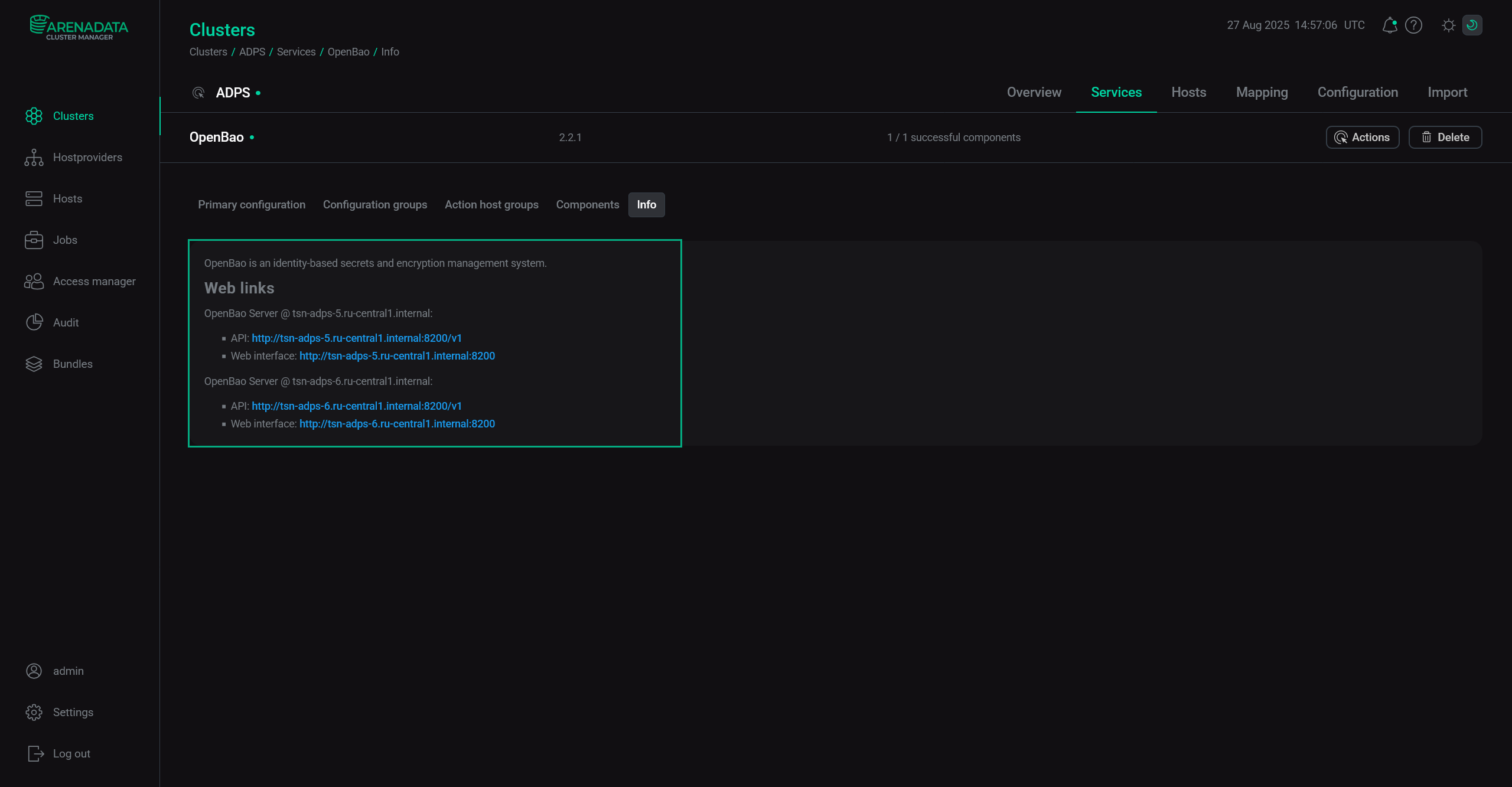 OpenBao web links in case of two OpenBao Server instances
OpenBao web links in case of two OpenBao Server instances
Secrets engines
Secret engines is the main page that appears right after you log into the OpenBao web interface.
Here, you can find a list of secret engines (cubbyhole is created by default) and create a new engine.
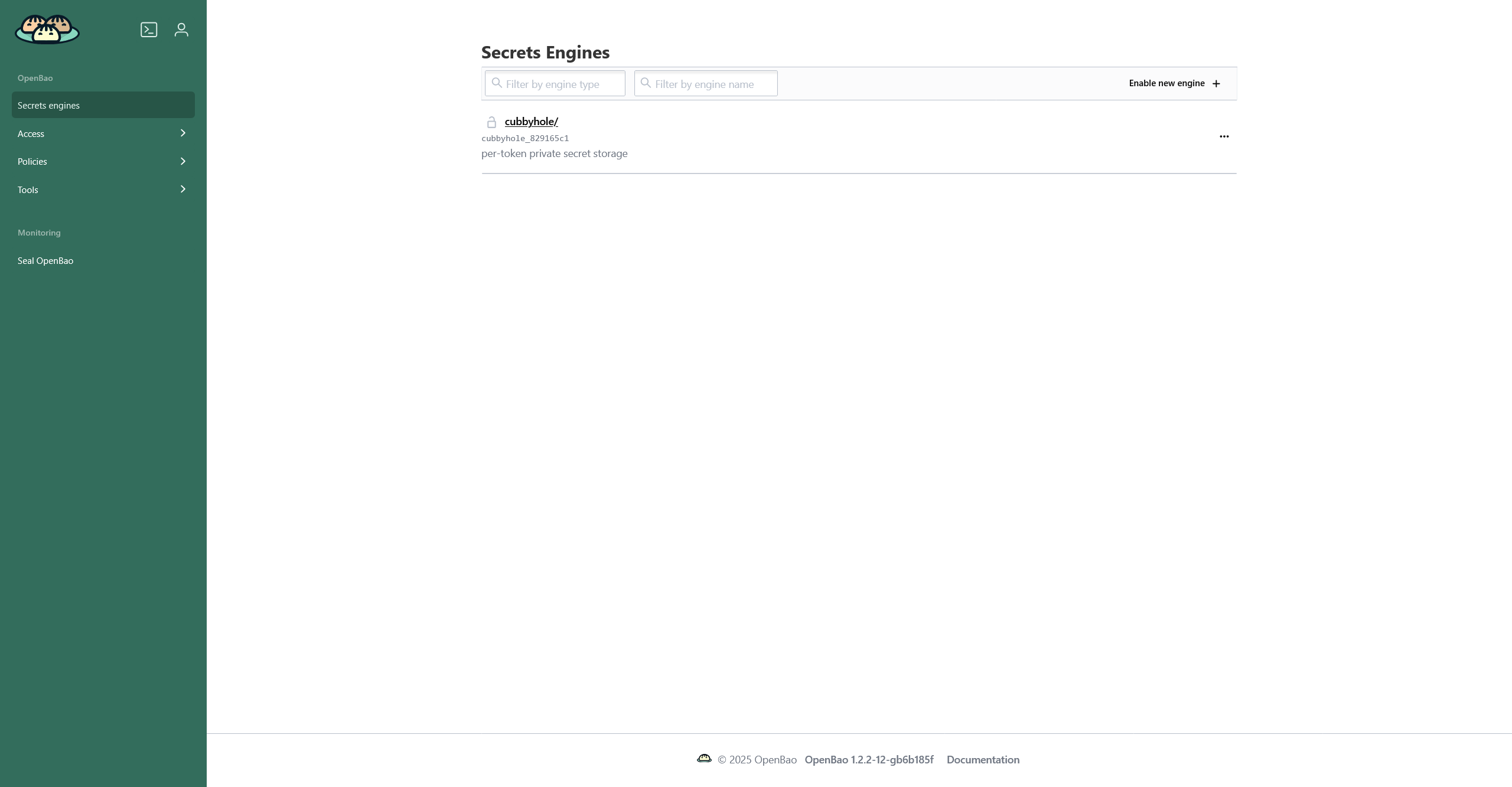
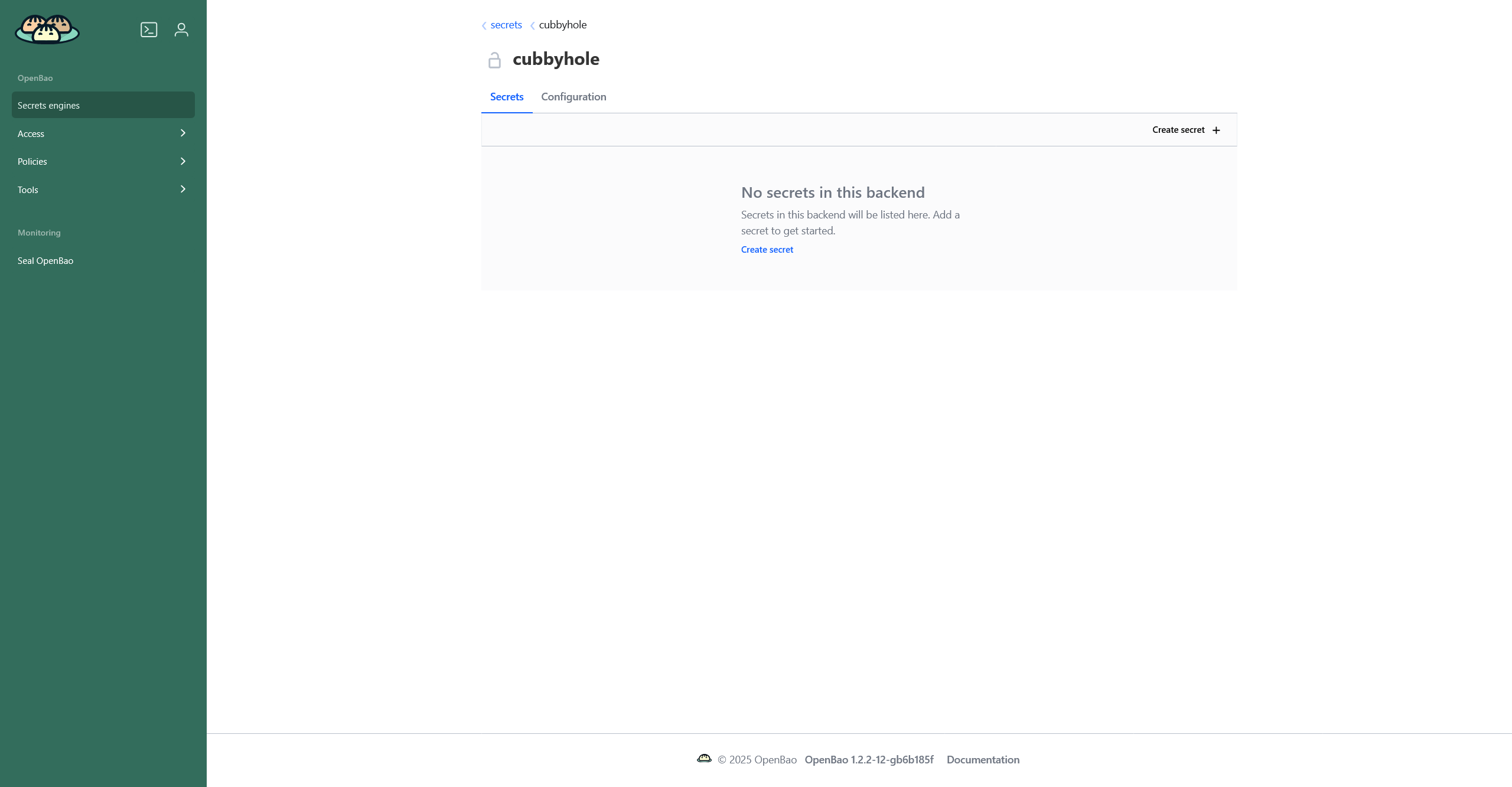
When you click on a secret engine, a page with two tabs appears:
-
Secrets — a tab with a list of kept secrets.
-
Configuration — a tab with the engine configuration, where you can find such information as the engine’s path, description, accessor, and default lease TTLs.
Also, each page has a sidebar which has two buttons on top:
-
— opens a OpenBao Browser CLI, which is essentially a shell where you can execute common OpenBao CLI commands.
-
— displays your username, allows you to copy your access token, and to log out of the system.
Access
The Authentication methods page displays a list of the available authentication methods. By default, it’s only token, which allows users to log in using a special token. Other possible methods are Username, LDAP, JWT, OIDC, and RADIUS. Clicking on an authentication method opens a page where you can view or change the method’s configuration.
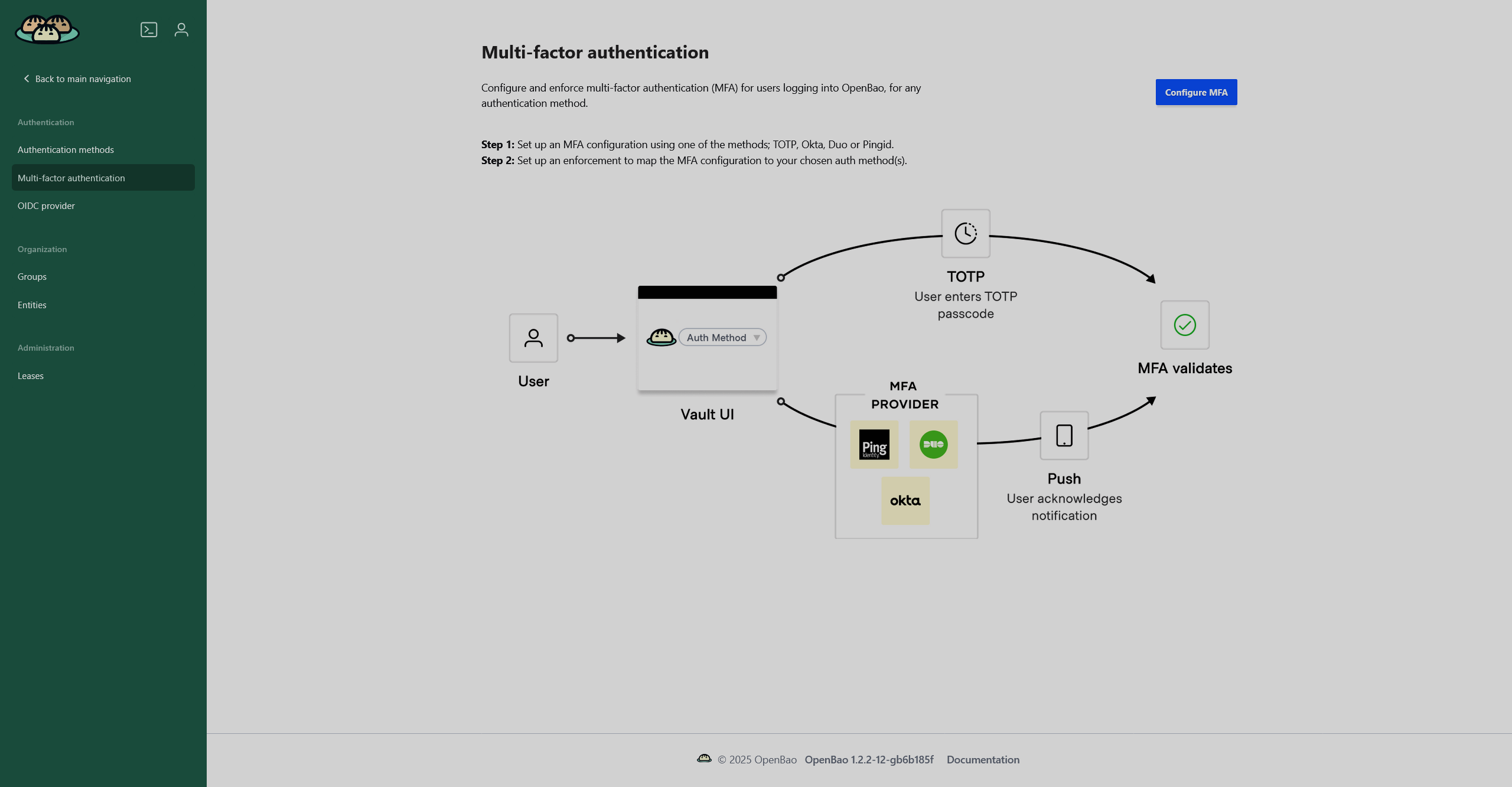
The Multi-factor authentication page displays configured MFA methods and allows you to configure a new one. The available methods are TOTP (time-based one-time password), Duo, Okta, and PingID. If you have no MFA methods configured, a short instruction will be displayed.
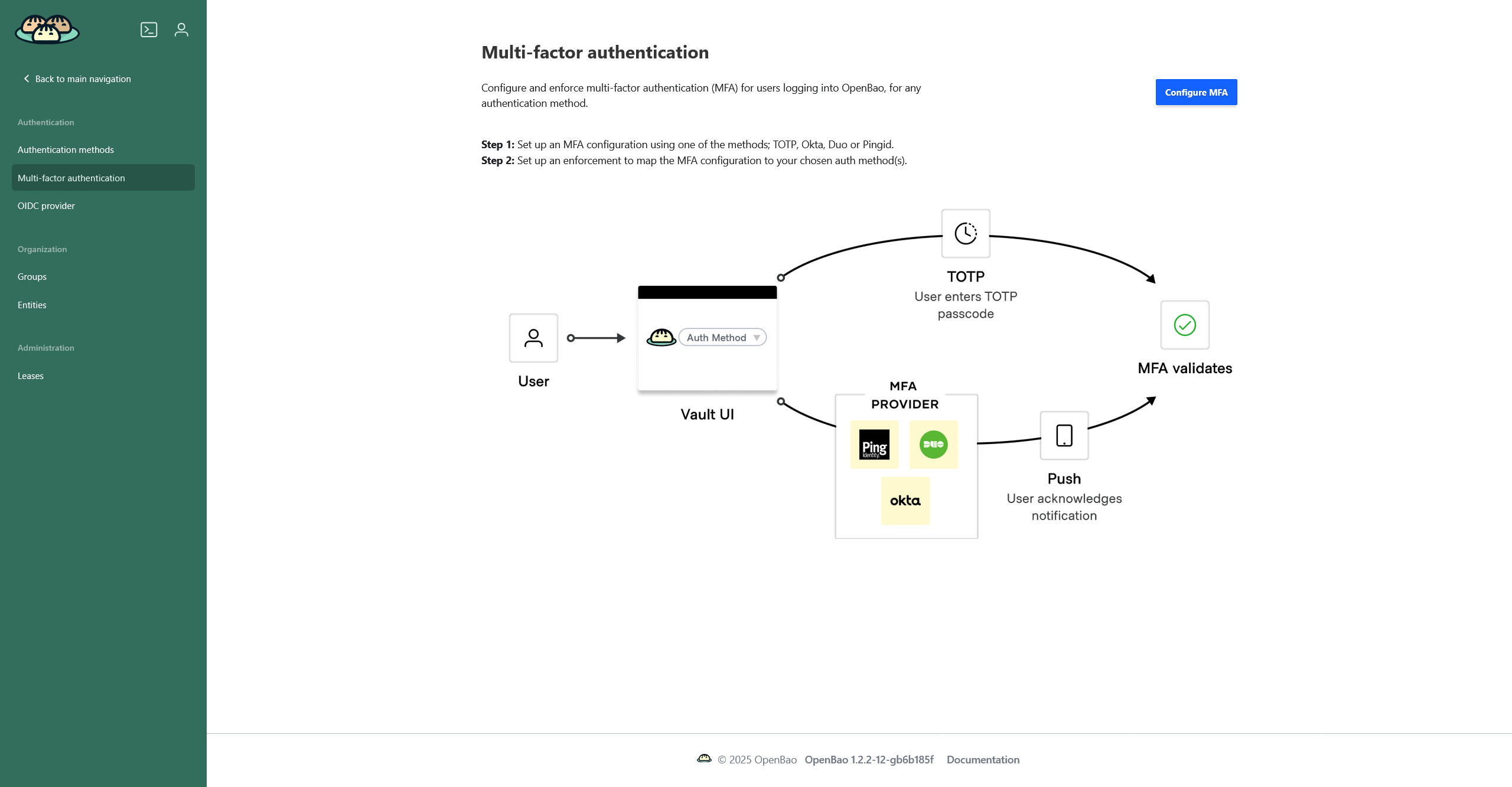
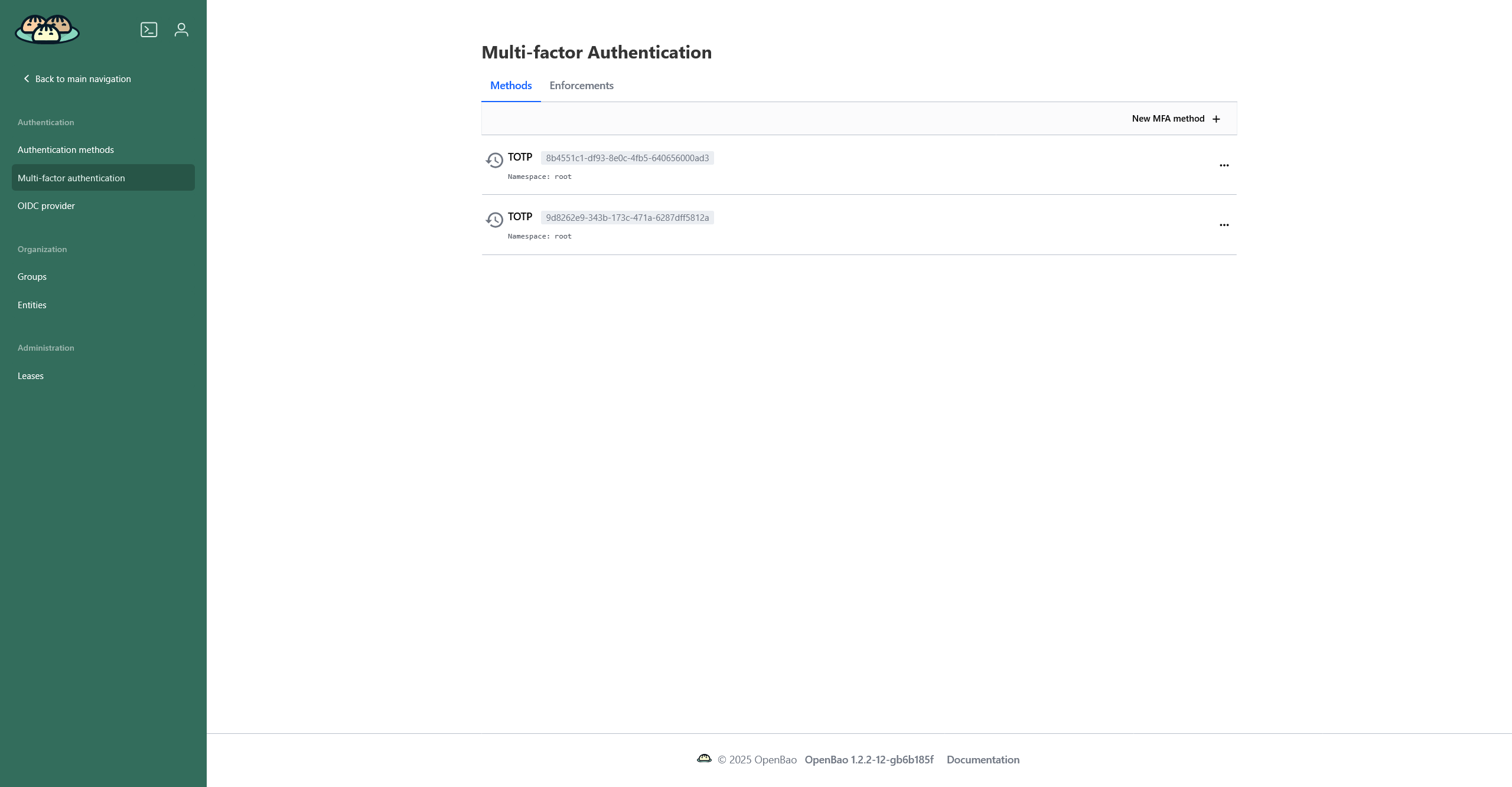
If you have at least one method configured, you will see a page with two tabs:
-
Methods — list of configured authentication methods. If one method (e.g.
TOTP) is configured with different settings, it will be displayed multiple times. -
Enforcements — a list of enforcements that define which authentication types, authentication mounts, groups, and/or entities will require an MFA method.
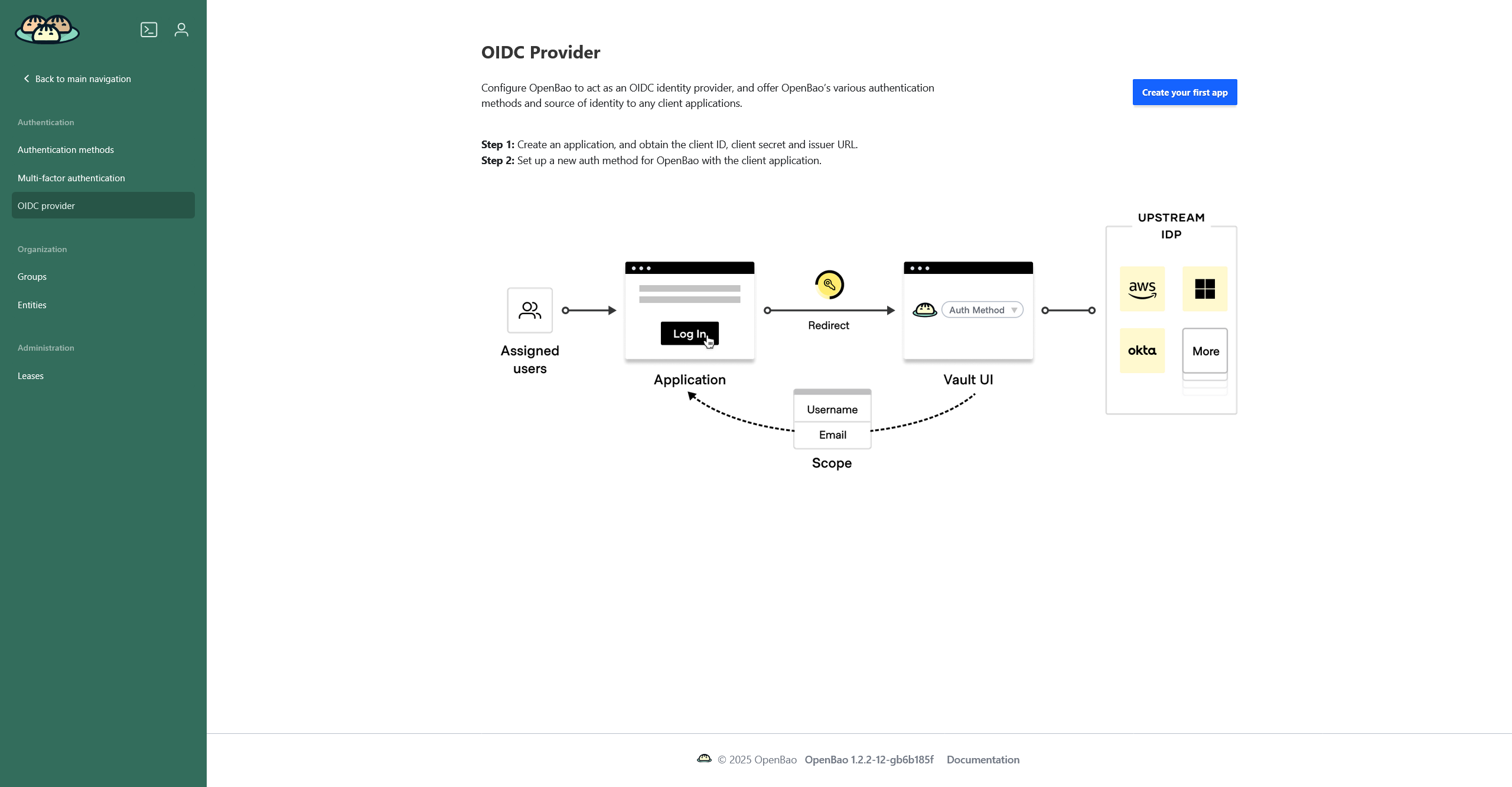
The OIDC provider page displays which applications use OpenBao as an OpenID Connect (OIDC) provider and allows you to configure an application to do so. If you have no apps configured, a short instruction will be displayed.
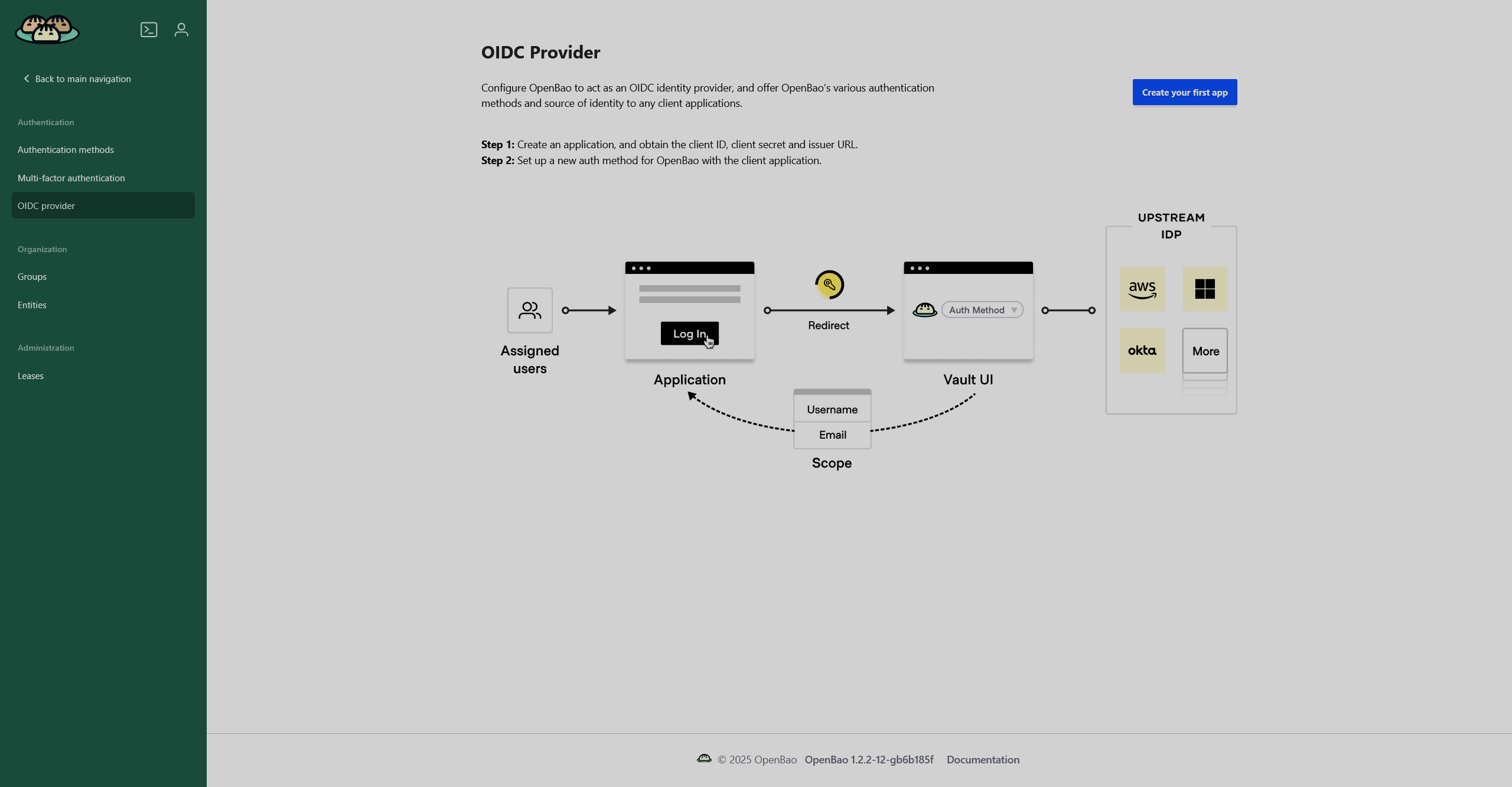
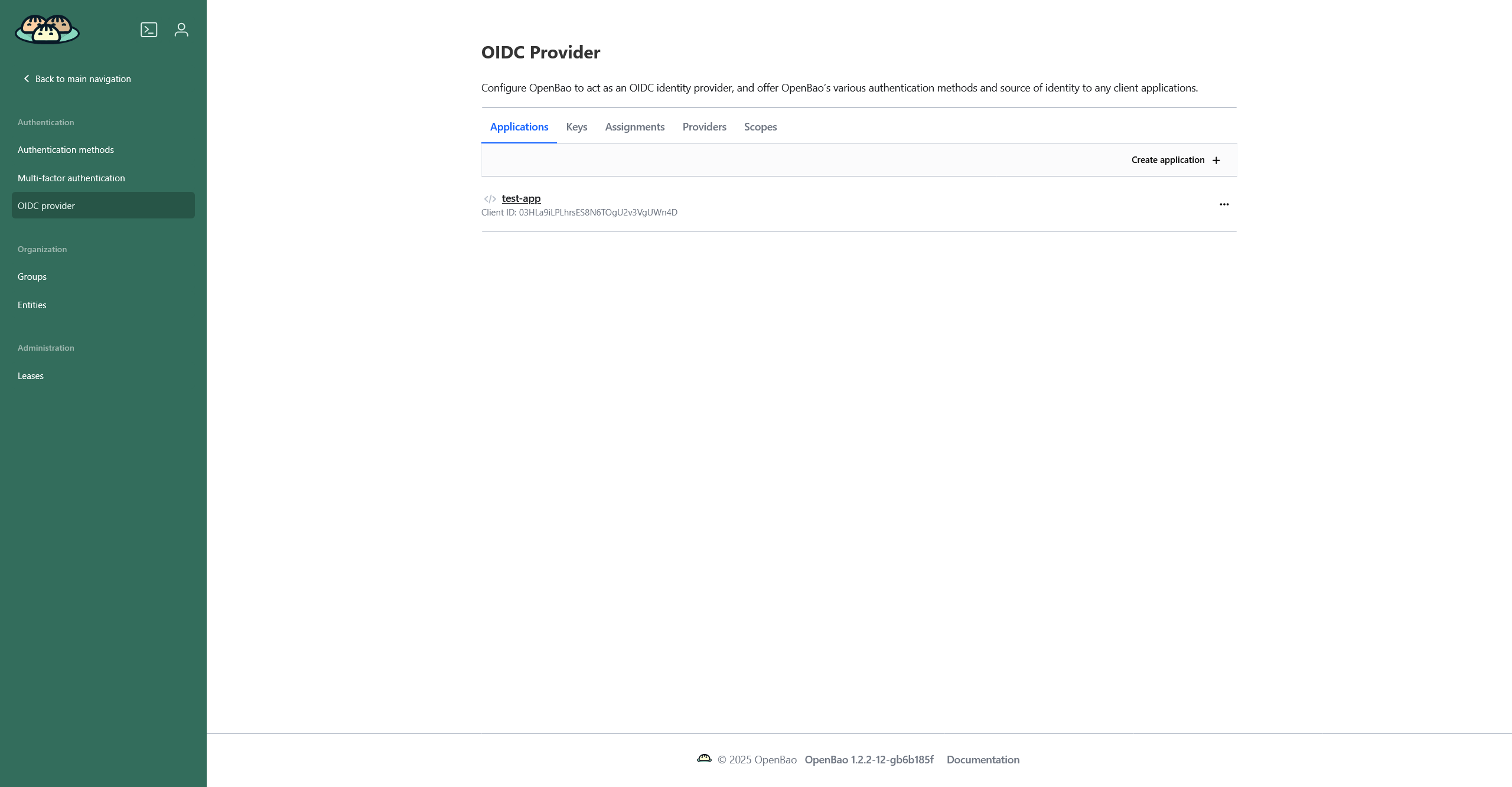
If you have at least one application configured, you will see a page with five tabs:
-
Applications — a list of applications that have OpenBao as an OIDC provider.
-
Keys — a list of keys to sign and verify the JSON Web Tokens.
-
Assignments — a list of assignments: parameters that limit which OpenBao users are allowed to authenticate.
-
Providers — a list of OIDC providers. Initially, there’s only the
defaultprovider, which can be edited but not deleted. -
Scopes — a list of scopes. Providers may reference a set of scopes to make specific identity information available as claims.
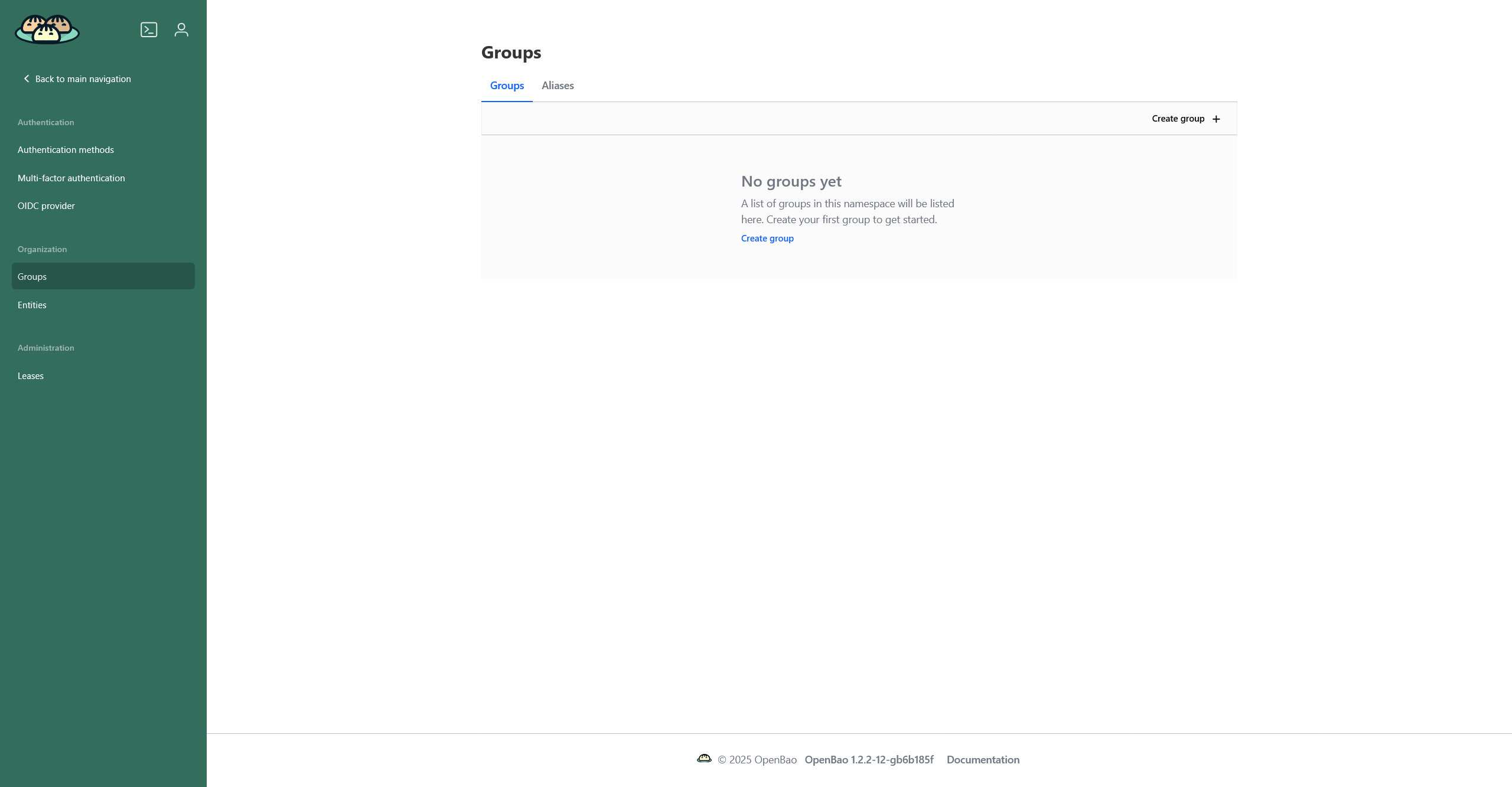
The Groups page displays two tabs:
-
Groups — a list of available groups (both internal and external).
-
Aliases — a list of aliases for external groups.
On this page, you can also create a new group or edit an existing one. If you click on an external group, you will be able to create an alias for it.
The Entities page displays two tabs:
-
Entities — a list of entities.
-
Aliases — a list of aliases for entities.
On this page, you can create a new entity, edit an existing one, or merge one entity into another. If you click on an entity, you will be able to create an alias for it.
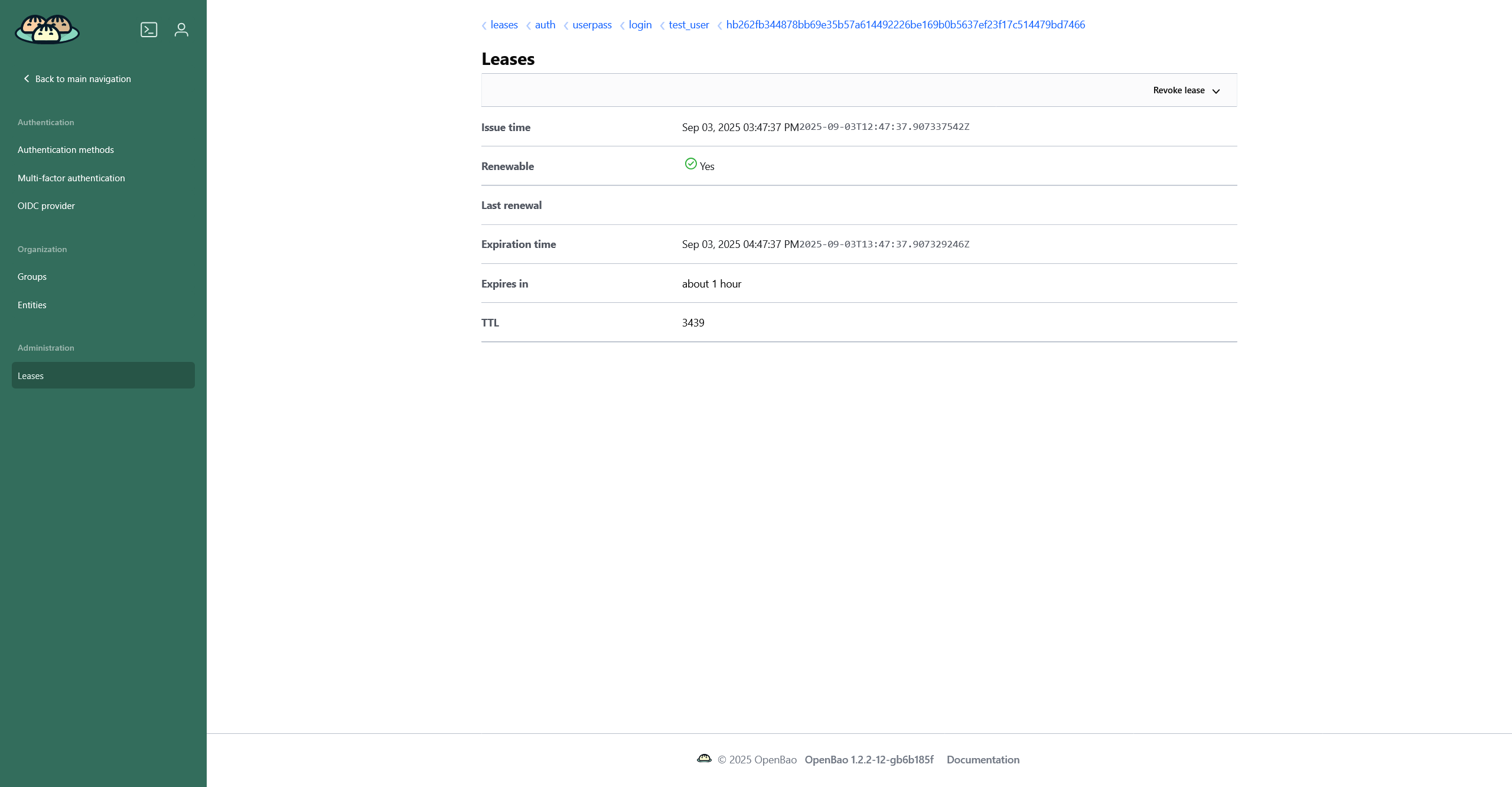
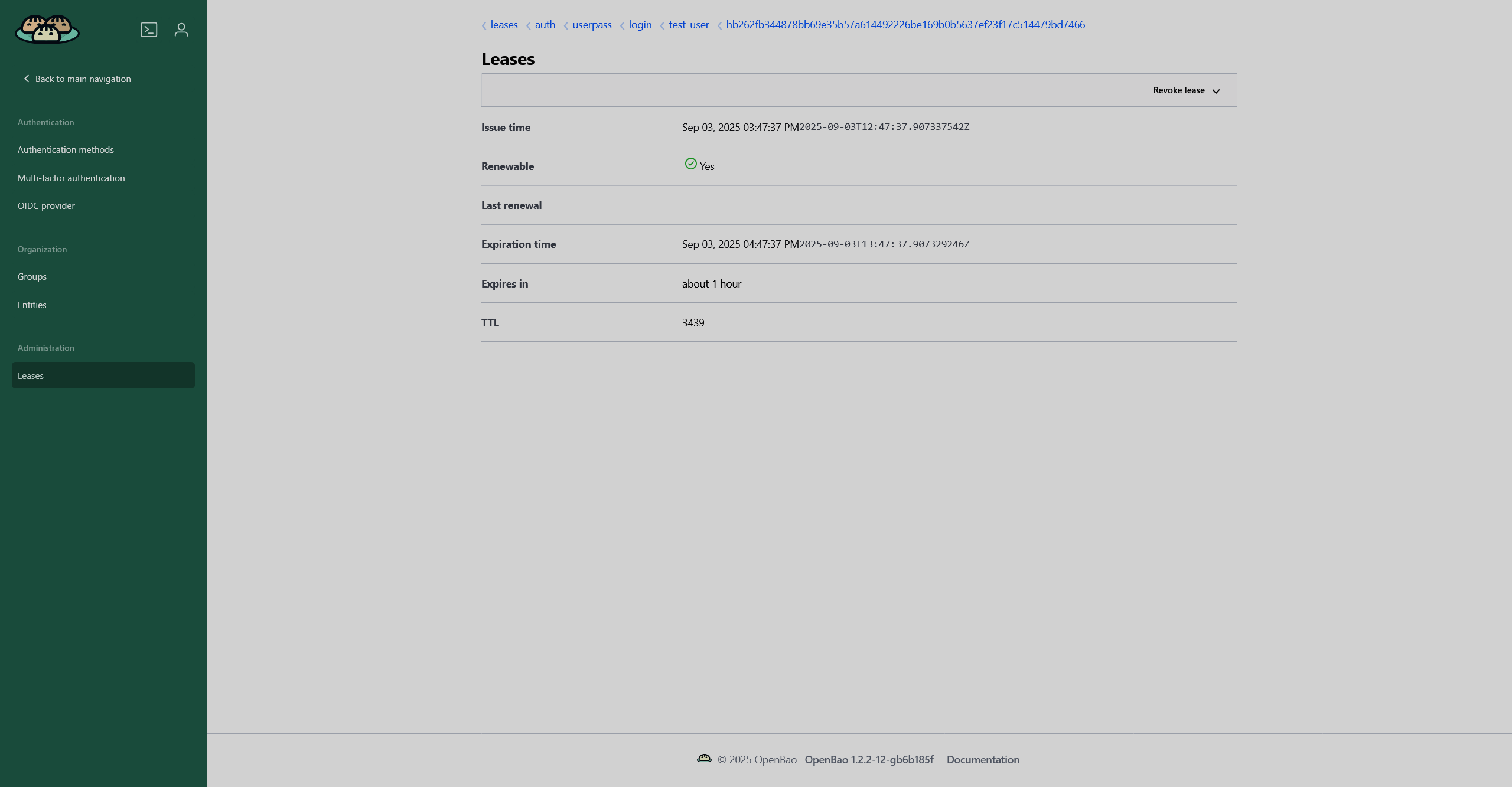
The Leases page displays a list of leases, time-limited grants of permission. Each list entry is a path to a certain lease, which contains authentication method and username, whose lease is active. Among the displayed information you can see when the lease expires.
Tools
The Wrap page presents a tool that allows you to wrap your JSON data into a secret engine token.
The Lookup page presents a tool that allows you to get details of a certain secret engine token. It provides the following information:
-
Creation path — path where a token was created (e.g. sys/wrapping/wrap).
-
Creation time — time when a token was created (e.g.
2025-09-03T17:49:47.563425828Z). -
Creation TTL — time-to-live (TTL) of a token in seconds (e.g.
1800). -
Expiration date — date when a token will expire (e.g.
Wed Sep 03 2025 21:19:47 GMT+0300 (Moscow Standard Time)). -
Expires in — approximate countdown to the token expiration time (e.g.
30 minutes).
The Unwrap page presents a tool that allows you to unwrap your secret engine token into JSON data.
The Rewrap page presents a tool that allows you to rewrap the data in your secret engine token into a new token.
The Random page presents a tool that generates a sequence of bytes of custom length in the base64 or hex formats.
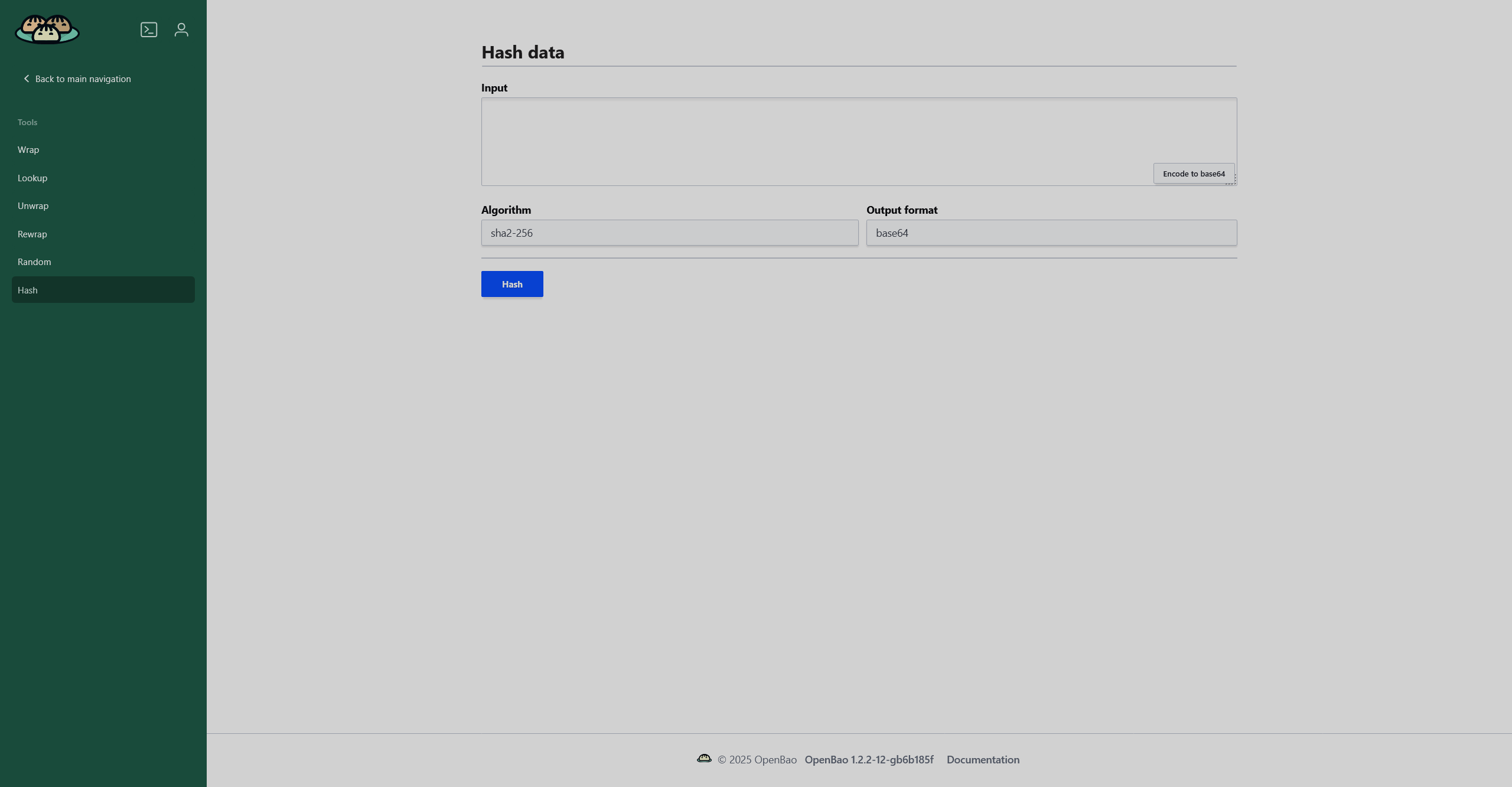
The Hash page presents a tool that allows you to generate a cryptographic hash of any input data. It can generate the output in base64 or hex while using one of the available algorithms: sha2-224, sha2-256, sha2-384, and sha2-512.
Seal OpenBao
The Seal OpenBao page allows you to seal OpenBao. When OpenBao is sealed, it means its core data storage (where all your secrets are kept) is encrypted and inaccessible. The server cannot read any stored secrets, authenticate users, or perform any cryptographic operations until it is unsealed again with the unseal CLI command or via the API.