

Configure custom roles
In some cases, the functionality of the built-in ADCM roles is not enough to grant the users sufficiently granular access. In this case, you can create a new role with appropriate permissions.
The process of creating a new role is described on the Create roles page.
Example
Suppose you need a role that only allows to run any check action on a cluster. To create this role, do the following:
-
In the Create role window on the Roles tab enter
Cluster action checkas the role name and include theCluster Action: CheckandService Action: Checkpermissions. -
Click Create.
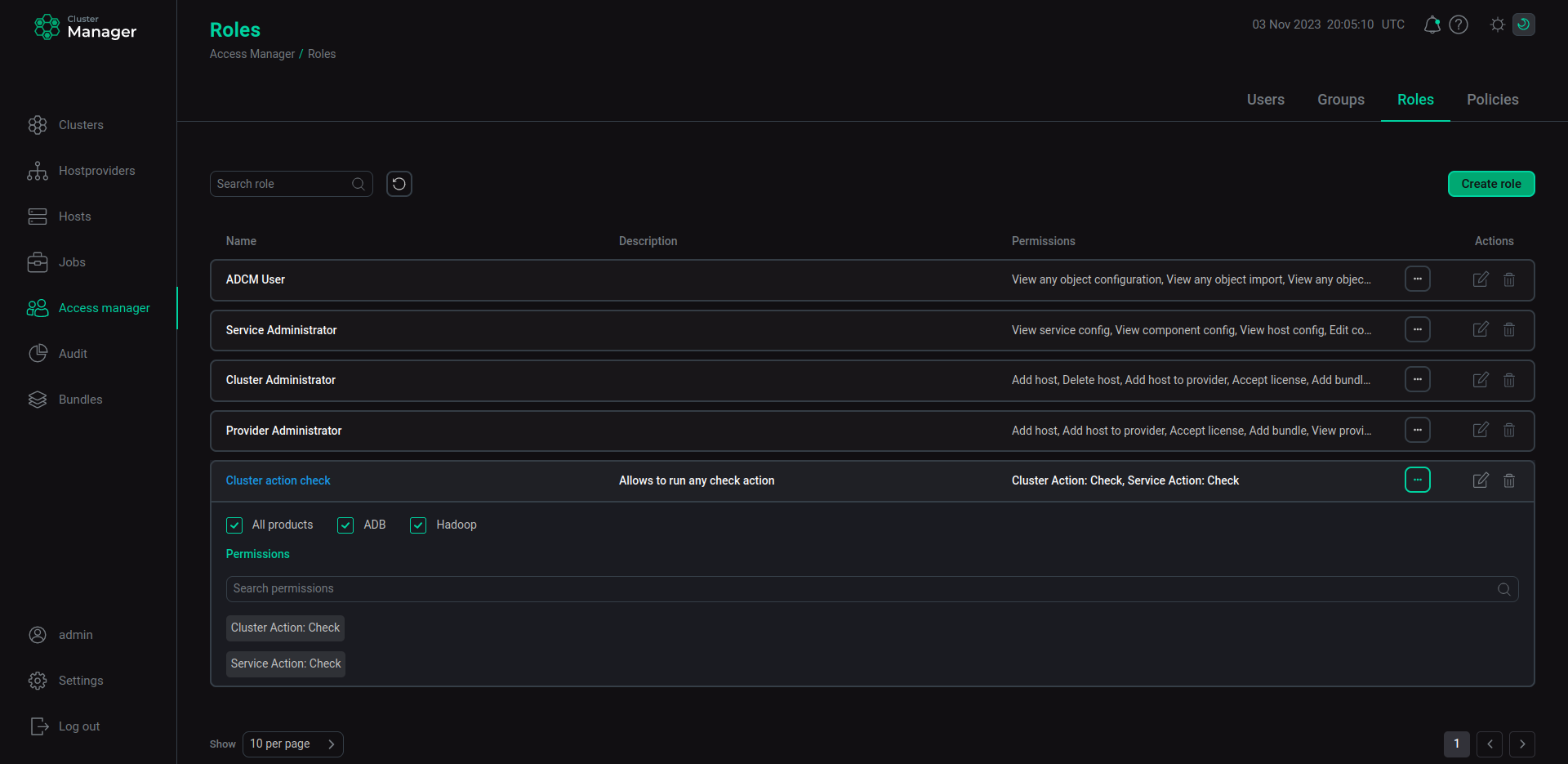 The Cluster action check role
The Cluster action check role
To implement the Cluster action check role, create a new policy by following the steps below:
-
In the Create new policy window on the Policies tab enter
Action checkas a policy name. -
Select the
useruser to be affected by this policy. -
Click Next.
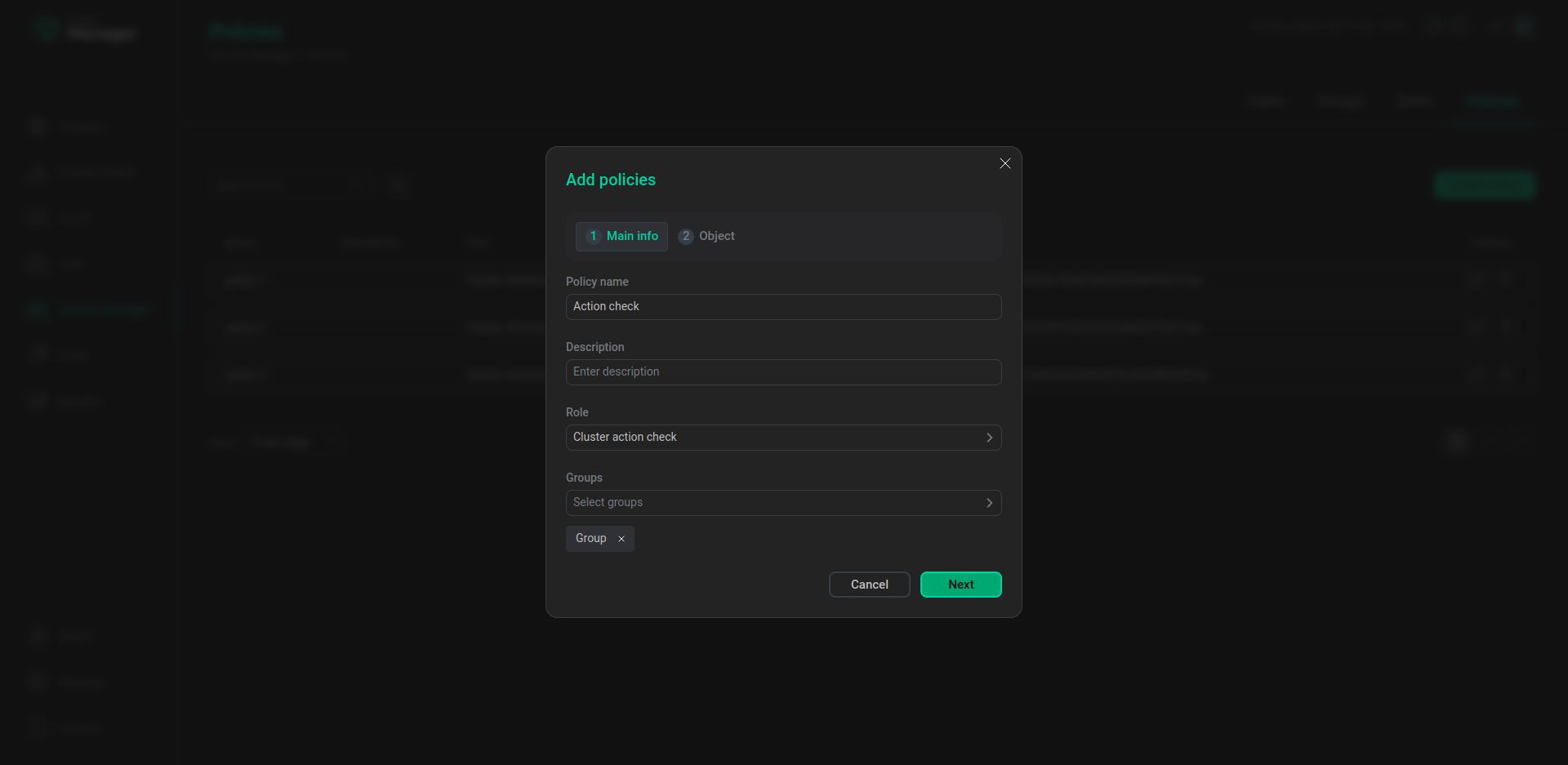 The first step of creating the Action check policy
The first step of creating the Action check policy -
Select the
Hiveservice and theADHcluster for theAction checkpolicy. -
Click Create.
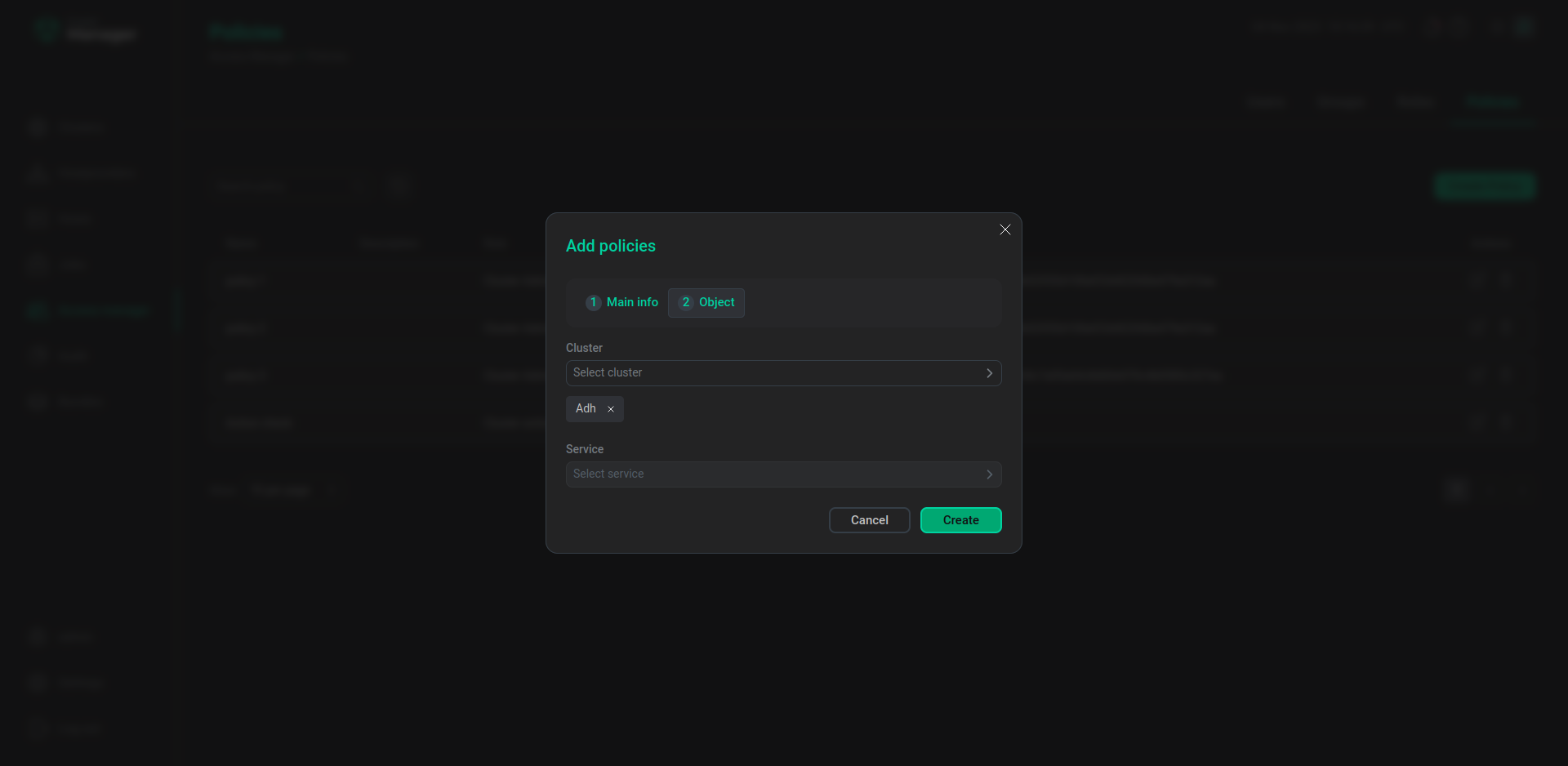 The second step of creating the Action check policy
The second step of creating the Action check policy
After the Action check policy is created, the user is able to run check actions for the ADH cluster and the Hive service.
If the Service Action: Check permission was not included into the Cluster action check role, you will not be able to select any service when creating the Action check policy. The objects available for selection when creating a new policy depend on the permissions included in the role a new policy is based on.