

Enable LDAP
Definitions
This page includes the following terminology:
-
Active Directory (AD) is an implementation of directory services that provides all kinds of functionality, such as authentication, group and user management, policy administration, and more.
-
Lightweight Directory Access Protocol (LDAP) is an open cross-platform protocol designed for directory services authentication.
-
OpenLDAP is an open implementation of LDAP that is distributed via its own OpenLDAP Public License.
-
Free Identity, Policy and Audit (FreeIPA) is an open centralized system that is designed to manage user authorizations and to create audit and access policies for the UNIX-based networks.
|
IMPORTANT
|
LDAP description
ADCM provides tools to synchronize its users and groups with external systems that support LDAP (such as Active Directory, OpenLDAP, or FreeIPA). This allows automating the process of creating ADCM user accounts according to the already existing company policies, as well as to apply the existing ADCM access control methods (granting and revoking rights, changing group memberships, and so on) to external users.
After configuring LDAP in ADCM, you are able to do the following:
-
Automatically update user information (such as credentials) in case of it being changed in AD, OpenLDAP, or FreeIPA.
-
Automatically deactivate user accounts in case of them being disabled in AD, OpenLDAP, or FreeIPA with ADCM.
-
Automatically add new users if they are aligned with LDAP configuration settings.
Workflow
To enable LDAP integration, perform the following steps:
-
Navigate to the Settings page.
-
Activate the LDAP integration switch.
-
Configure LDAP settings that are listed in the Configuration settings table below.
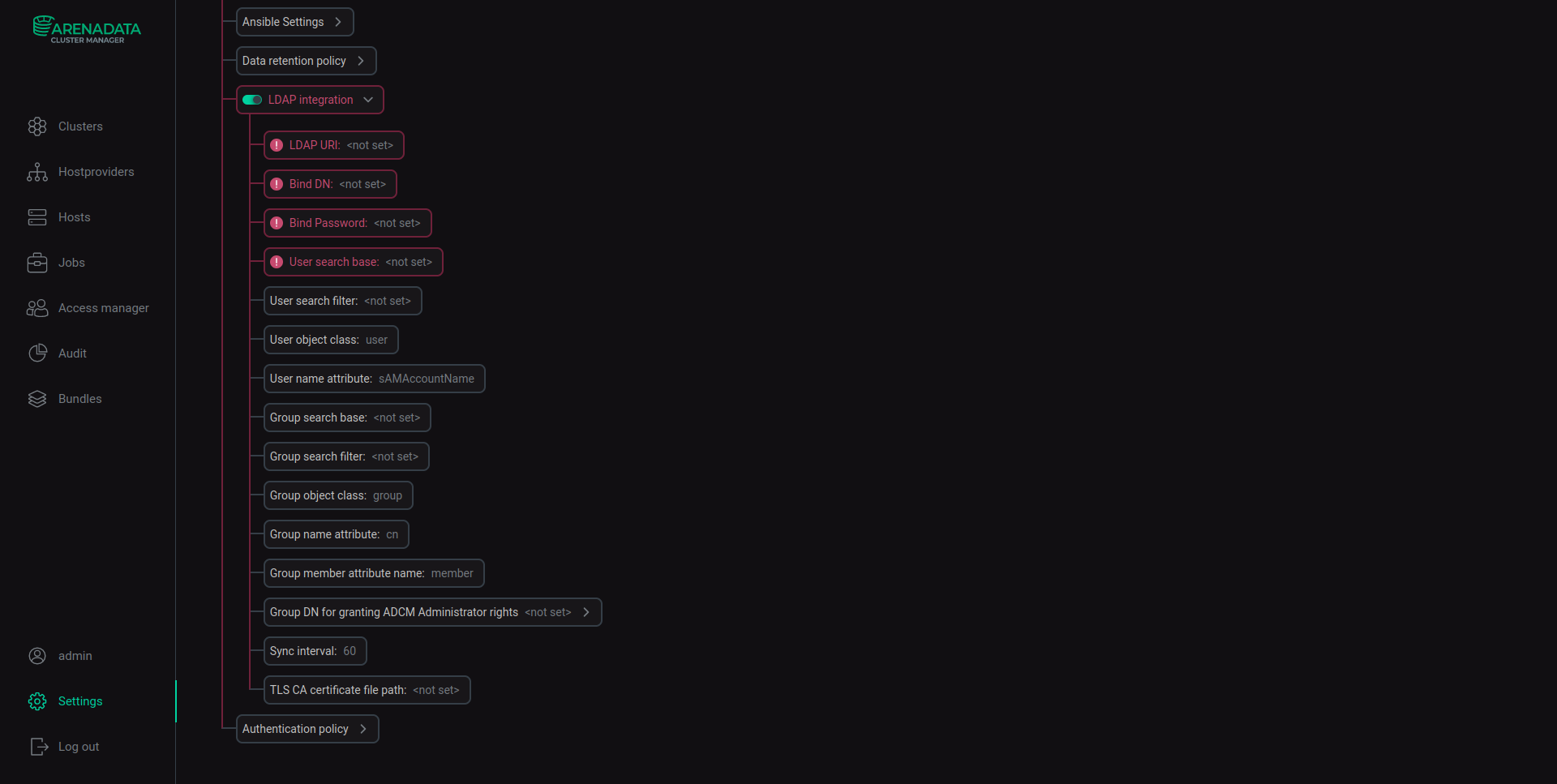 LDAP integration parameters
LDAP integration parameters -
Click Save. Now two actions become possible: Run LDAP sync and Test LDAP connection.
-
Run the Test LDAP connection action to test connection to LDAP. You can view the action result on the Jobs page.
-
Run the Run LDAP sync action to synchronize the users, groups, and their memberships from Active Directory, OpenLDAP, or FreeIPA into ADCM. You can view the action result on the Jobs page.
|
NOTE
If LDAP access is configured correctly, then any user that matches the configured LDAP settings is able to authenticate in ADCM (even if the Run LDAP sync action was not performed).
|
| Name | Description | Required |
|---|---|---|
LDAP URI |
URI of the LDAP server |
Yes |
Bind DN |
Distinguished name (DN) of the user that is used to connect to the LDAP server. For example: |
Yes |
Bind Password |
Password for access to the LDAP server of the user specified in the Bind DN field |
Yes |
User search base |
Distinguished name of the directory object from which to search for entries. For example: |
Yes |
User search filter |
Additional filter constraining the users selected for syncing |
No |
User object class |
Object class to identify user entries. The default value is |
Yes |
User name attribute |
Attribute from user entry that would be treated as user login. The default value is |
Yes |
Group search base |
Distinguished name of the directory object from which to search for entries. For example: |
No |
Group search filter |
Additional filter constraining the groups selected for syncing |
No |
Group object class |
Object class to identify group entries. The default value is |
Yes |
Group name attribute |
Attribute from group entry that would be treated as group name. The default value is |
Yes |
Group member attribute name |
Attribute from group entry that is list of members. The default value is |
Yes |
Group DN for granting the ADCM Administrator rights |
List of unique distinguished name groups whose members need to be granted ADCM Administrator rights. For example: |
No |
Sync interval |
Amount of time in minutes that groups, group memberships, and user distinguished names are synchronized between Active Directory, OpenLDAP, or FreeIPA and ADCM. The default value is |
Yes |
TLS CA certificate file path |
CA certificate path in the ADCM container volume |
No |