

Configuration parameters
This article describes parameters that can be configured for ADQM Control services via ADCM. To read about the configuration process, refer to the Configure services article in the section Online installation of ADQM Control.
|
NOTE
Some of the parameters become visible in the ADCM UI after the Show advanced flag being set.
|
ADQM Control
| Parameter | Description | Default value |
|---|---|---|
ADQM username |
Username to connect to ADQM |
adqmc |
ADQM user password |
Password for the |
— |
ADQM default port |
Default port if it is not exported from an ADQM cluster |
9000 |
ADQM secure port |
Default port for SSL-secured communication with ADQM if it is not exported from an ADQM cluster |
9440 |
Connection type |
Type of connection (insecure or secure) between ADQM Control and ADQM. Possible values: |
Insecure (TCP) |
|
NOTE
A name and password passed to the |
| Parameter | Description | Default value |
|---|---|---|
Session timeout |
ADQM Control web interface session timeout (in seconds) |
1800 |
Enable CSRF validation |
Enables CSRF validation |
Enabled |
|
NOTE
For details on how to configure and enable SSL for components of ADQM Control’s services, see the SSL encryption article. |
| Parameter | Description | Default value |
|---|---|---|
[ADQM Control’s Backend] → Enable SSL |
Enables SSL for the Backend component |
Disabled |
[ADQM Control’s ADQM Agent] → Enable SSL |
Enables SSL for the Agents component |
Disabled |
[ADQM Control’s Alert Generator] → Enable SSL |
Enables SSL for the Alert Generator component |
Disabled |
[ADQM Control’s Alert Receiver] → Enable SSL |
Enables SSL for the Alert Receiver component |
Disabled |
[Alertmanager] → Enable SSL |
Enables SSL for the Alertmanager component |
Disabled |
[ADQM Control Services] → Certificate file |
Path to the server SSL certificate file for the Backend, Agents, Alert Generator, Alert Receiver components |
/etc/adqmc/server.crt |
[ADQM Control Services] → Private key file |
Path to the file with the private key of the server SSL certificate for the Backend, Agents, Alert Generator, Alert Receiver components |
/etc/adqmc/server.key |
[ADQM Control Services] → Certificate authority file |
Path to the file with the CA certificate for the Backend, Agents, Alert Generator, Alert Receiver components |
/etc/adqmc/ca.crt |
[Alertmanager] → Certificate file |
Path to the server SSL certificate file for the Alertmanager component |
/etc/admprom/alert-manager/server.crt |
[Alertmanager] → Private key file |
Path to the file with the private key of the server SSL certificate for the Alertmanager component |
/etc/admprom/alert-manager/server.key |
[Alertmanager] → Certificate authority file |
Path to the file with the CA certificate for the Alertmanager component |
/etc/admprom/alert-manager/ca.crt |
| Parameter | Description | Default value |
|---|---|---|
Backend port |
Port to access the ADQM Control web interface |
5555 |
Alert Generator port |
Port the alert generator listens on |
5001 |
ADQM agent port |
Port the Agents service listens on |
5002 |
Alertmanager port |
Port the alert manager listens on |
9093 |
Alert Receiver port |
Port the alert receiver listens on |
12322 |
| Parameter | Description | Default value |
|---|---|---|
Backend connection pool size |
Maximum number of connections to a PostgreSQL database of the Backend service |
8 |
ADQM agent connection pool size |
Maximum number of connections to a PostgreSQL database of the Agents service |
8 |
Statement timeout |
Timeout for queries and transactions (in seconds) |
120 |
Cleanup timeout |
Server timeout (in seconds): abort any database query that runs longer than the specified time |
86400 |
Migration timeout |
Database migration timeout (in seconds) |
3600 |
Prometheus timeout |
Prometheus connection timeout (in seconds) |
60 |
Alertmanager timeout |
Alertmanager connection timeout (in seconds) |
60 |
| Parameter | Description | Default value |
|---|---|---|
Hosts scrape interval |
Frequency of updating information about the ADQM cluster topology (in seconds) |
80 |
ADQMDB scrape interval |
Frequency of updating information about tables in the ADQM cluster (in seconds) |
80 |
Query update interval |
Frequency of collecting queries (in seconds) |
105 |
Query normalize interval |
Frequency of updating queries (in seconds) |
120 |
Check query_log interval |
Frequency of checking query_log (in seconds) |
60 |
| Parameter | Description | Default value |
|---|---|---|
Normalize query raw max queries per iteration |
Maximum number of queries normalized per iteration |
50000 |
Collect queries limit |
Number of queries collected from the query_log per iteration |
10000 |
Query normalize threshold |
Number of attempts to normalize a query |
10 |
Existing tables tries |
Number of attempts to get metrics of an ADQM table. If ADQM Control has failed to retrieve the metrics for a table after the expiration of the time |
3 |
Tables cache size |
Size of the table cache |
32768 |
Table cache invalidate interval |
Time interval of the table cache invalidation (in seconds) |
28800 |
Maximum revision per table in cache |
Maximum number of revisions per table in the cache |
100 |
Queries cache size |
Size of the query cache |
8192 |
Batch size of queries normalization |
Query batch size for normalization |
1024 |
Capacity of existing tables cache |
Capacity of the existing tables cache |
500000000 |
Existing tables cache invalidate period |
Period of the existing table cache invalidation (in seconds) |
604800 |
Table’s existing period for existing tables cache calculation |
Period of a table’s existence (in seconds) for the existing table cache calculation |
7776000 |
Maximum of parallel workers |
Maximum number of parallel workers |
0 |
|
NOTE
To access the configuration parameters, activate the Use internal PostgreSQL server option. |
| Parameter | Description | Default value |
|---|---|---|
Alerts dbname |
Name of a database to be created for use by ADQM Control services |
adqmc |
Alertsdb username |
Name of a user with access to the |
adqmc |
Alertsdb password |
Password for the |
— |
|
NOTE
To access the configuration parameters, activate the Use external PostgreSQL server option. |
| Parameter | Description | Default value |
|---|---|---|
server_ip_port |
Click Add property to specify an IP address (as property name) and port (as property value) to access an external PostgreSQL server |
— |
Alerts dbname |
Database name to be used by ADQM Control services |
adqmc |
Alertsdb username |
Name of a user with access to the |
adqmc |
Alertsdb password |
Password for the |
— |
SSL is used by an external server |
Specifies whether SSL is used by an external server |
Disabled |
ADPG
| Parameter | Description | Default value |
|---|---|---|
Data directory |
Directories used to store data on ADPG hosts |
/pg_data1 |
|
TIP
You can obtain the optimal parameter values to achieve the best ADPG performance using the Collect recommendations action of the ADPG service.
|
| Parameter | Description | Default value |
|---|---|---|
listen_addresses |
TCP/IP addresses on which the server listens for connections from client applications |
* |
port |
TCP port the server listens on |
5432 |
max_connections |
Maximum number of concurrent connections to the database server |
100 |
shared_buffers |
Amount of memory the database server uses for shared memory buffer. A reasonable starting value is 25% of the memory in your system |
2048 MB |
max_worker_processes |
Maximum number of background processes that the system can support |
23 |
max_parallel_workers |
Maximum number of workers that the system can support for parallel operations |
4 |
max_parallel_workers_per_gather |
Maximum number of workers that can be started by a single Gather or Gather Merge node |
2 |
max_parallel_maintenance_workers |
Maximum number of parallel workers that can be started by a single utility command |
2 |
effective_cache_size |
Sets the ADPG query planner’s assumption about the effective size of the disk cache available to a single query. This is factored into estimates of the cost of using an index. The higher this value, the more likely the index scan will be applied. The lower this value, the more likely the sequential scan will be selected |
6144 MB |
maintenance_work_mem |
Memory limit for maintenance operations. Increasing the value for this parameter can improve the performance of operations for cleaning and restoring the database from a copy |
1024 MB |
work_mem |
Non-shared memory limit used for internal operations when the server executes queries (for example, queries to temporary tables) before temporary files on the disk are used. This limit acts as simple resource control, preventing the host from going into swapping due to overallocation. Since the allocated memory is non-shared memory, large and complex requests can exceed the specified limit |
5242 kB |
min_wal_size |
Until WAL disk usage stays below the |
1024 MB |
max_wal_size |
Memory limit to which the log size can grow between automatic checkpoints. Increasing this setting may increase the recovery time after a failure. The specified limit can be exceeded automatically with a high load on ADPG |
4096 MB |
wal_keep_size |
Specifies the minimum size of segments retained in the pg_wal directory, in case a standby server needs to fetch them for streaming replication. If a standby server connected to a sending server falls behind by more than |
0 MB |
huge_pages |
Defines whether huge pages can be requested for the main shared memory area. Possible values:
|
try |
superuser_reserved_connections |
Number of connection "slots" that are reserved for PostgreSQL superuser connections |
3 |
timescaledb.max_background_workers |
Maximum number of background worker processes allocated to TimescaleDB |
16 |
wal_buffers |
Amount of shared memory used for WAL data that has not yet been written to disk |
16 MB |
default_statistics_target |
Default statistics target for table columns without a column-specific target set via |
100 |
random_page_cost |
Planner’s estimate of the cost of a non-sequentially-fetched disk page |
1.1 |
checkpoint_completion_target |
Target time of checkpoint completion as a fraction of total time between checkpoints |
0.9 |
max_locks_per_transaction |
The shared lock table tracks locks on |
128 |
autovacuum_max_workers |
Maximum number of autovacuum processes (excluding the autovacuum launcher) that are allowed to run at the same time |
10 |
autovacuum_naptime(seconds) |
Minimum delay between autovacuum runs on any given database. In each round, the autovacuum daemon examines the database and executes the |
10 |
default_toast_compression |
Default TOAST compression method for values of a compressible column. Possible values: |
lz4 |
effective_io_concurrency |
Number of concurrent disk I/O operations that can be executed simultaneously. Raising this value will increase the number of I/O operations that a PostgreSQL session attempts to initiate in parallel |
256 |
jit |
Specifies whether PostgreSQL may use JIT compilation, if it is available |
off |
logging_collector |
Enables the logging collector — a background process that captures log messages sent to stderr and redirects them into log files |
Enabled |
log_directory |
Directory that contains log files. It can be specified as an absolute path, or relative to the ADPG cluster data directory |
log (the absolute path is /pg_data1/adpg14/log) |
log_filename |
Log file name pattern. A value can include strftime %-escapes to define time-varying file names. If you specify a file name pattern without escapes, use a log rotation utility to save disk space |
postgresql-%a.log |
log_rotation_age |
Maximum period of time to use a log file, after which a new log file is created. If this value is specified without units, it is taken as minutes. Set |
1d |
log_rotation_size |
Maximum size of a log file. After a log file reaches the specified size, a new log file is created. If the value is set without units, it is taken as kilobytes. Set |
0 |
log_min_messages |
Minimum severity level of messages to be written to a log file. Possible values are |
warning |
log_min_error_statement |
Specifies which SQL statements that cause errors are logged. Possible values are |
error |
In the Custom postgresql.conf section, you can set additional parameters to be written to the postgresql.conf file. To add a parameter, click Add property.
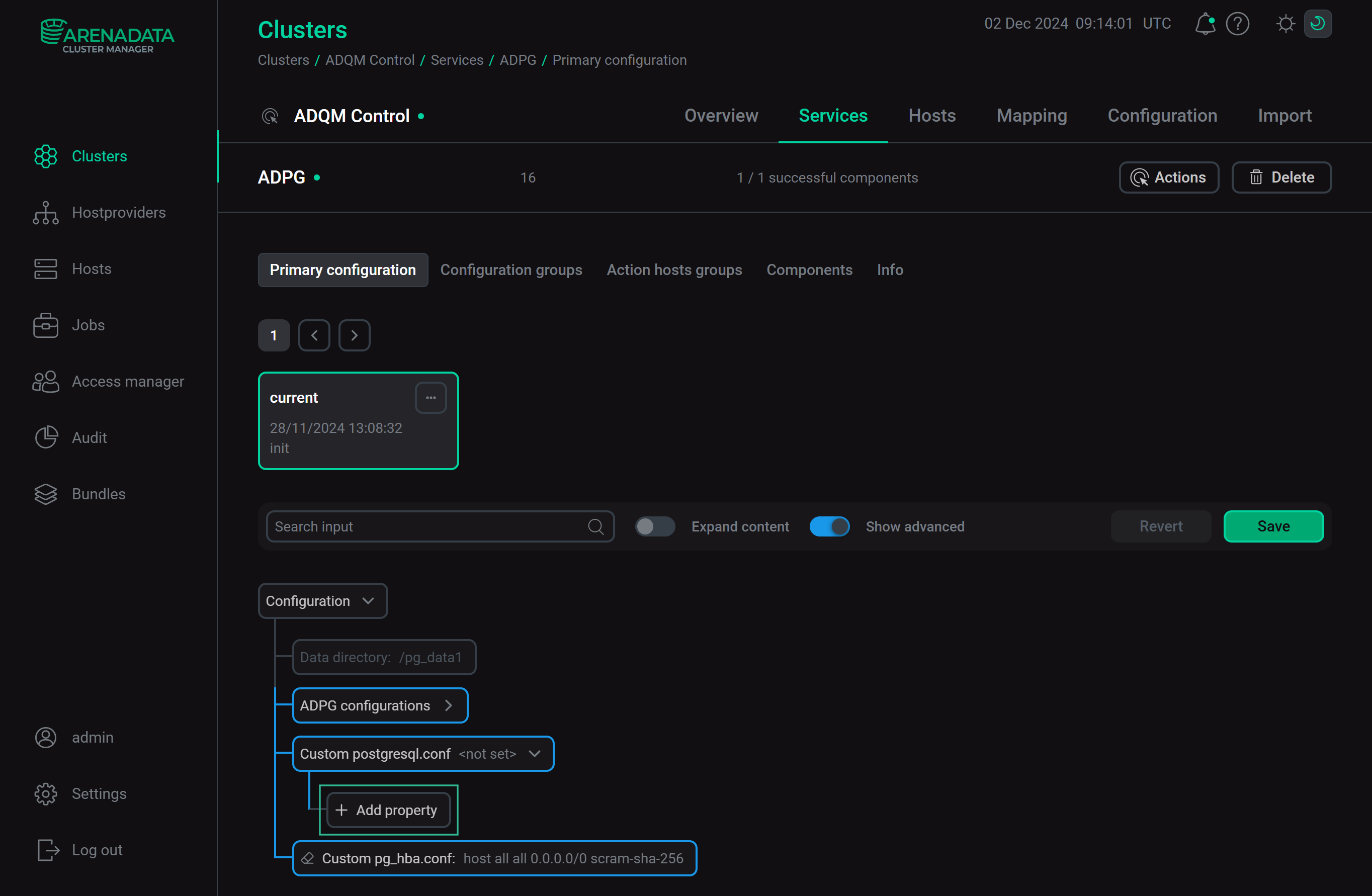
In the window that appears, enter a parameter (its name and value) and click Apply.
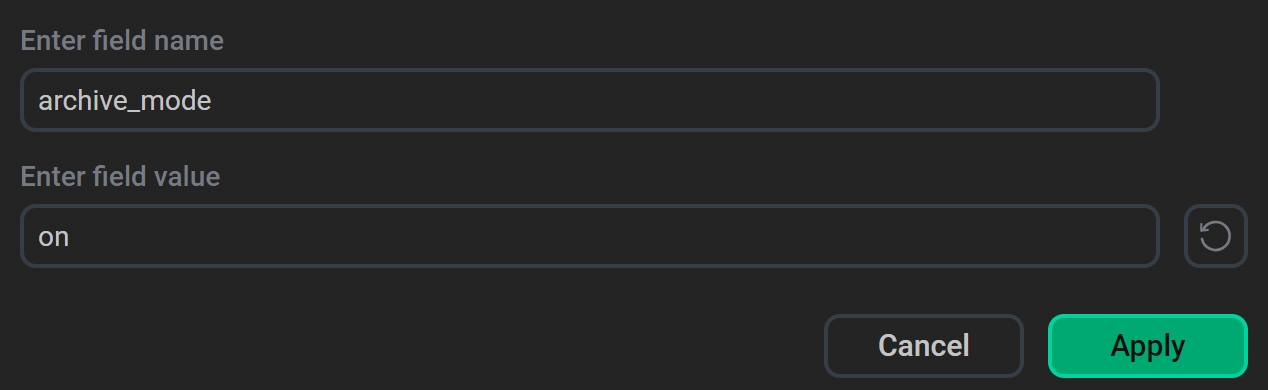
You can add multiple parameters.
Section for setting the shared_preload_libraries parameter of the postgresql.conf configuration. ADQM Control requires the timescaledb and timescaledb_toolkit extensions. If you need to add other extensions (for example, pg_stat_statements), use the icon
.
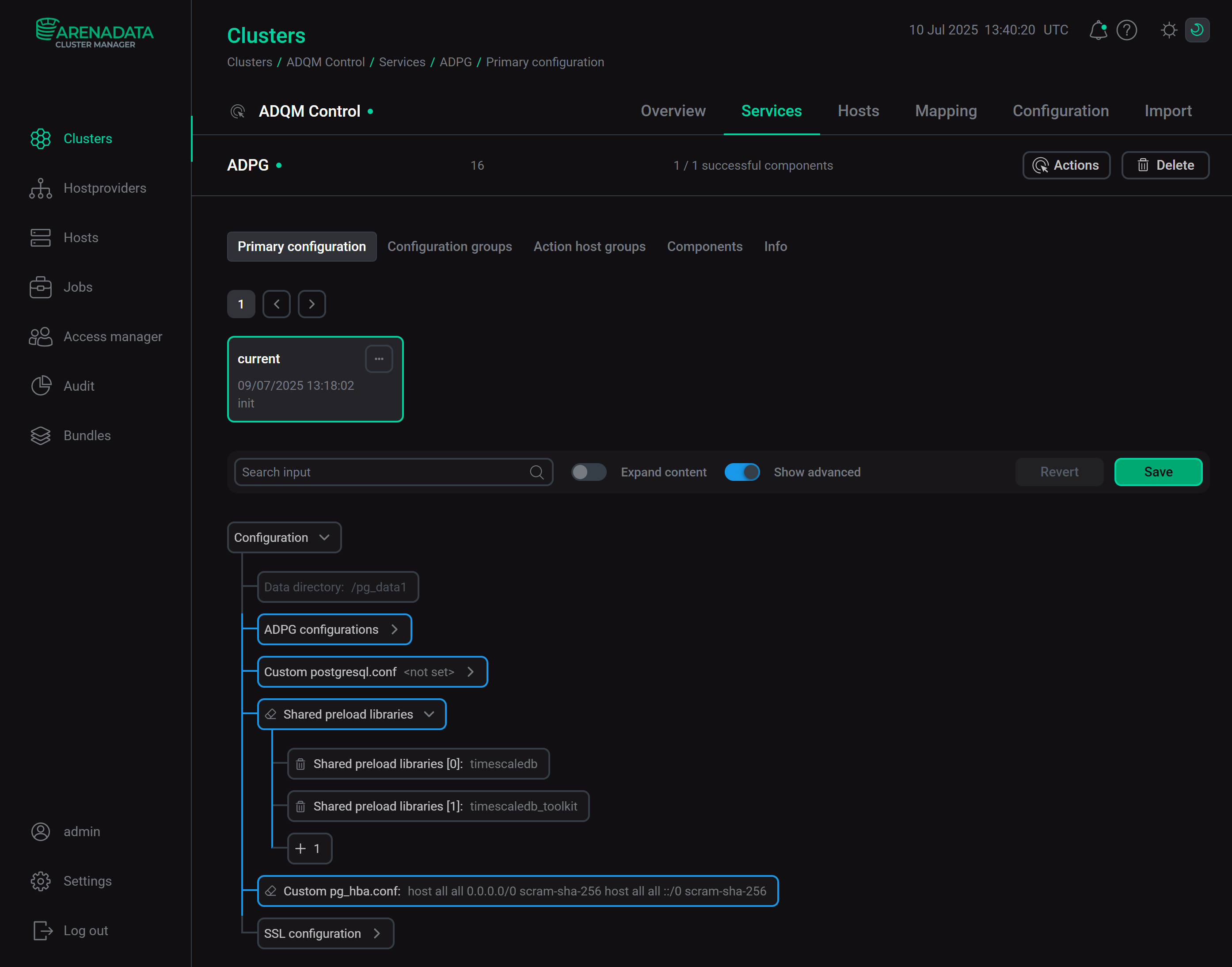
This field allows you to add records to the pg_hba.conf file that controls client authentication.
|
NOTE
For more information on SSL encryption support in ADQM Control, see the SSL encryption article. |
| Parameter | Description | Default value |
|---|---|---|
Enable SSL |
Enables SSL encryption of incoming traffic for the ADPG service |
Disabled |
Certificate file |
Path to the server SSL certificate file |
/etc/adpg16/server.crt |
Private key file |
Path to the file with the private key of the server SSL certificate |
/etc/adpg16/server.key |
Certificate authority file |
Path to the CA certificate file |
/etc/adpg16/ca.crt |
Monitoring
| Parameter | Description | Default value |
|---|---|---|
scrape_interval |
Specifies how frequently to scrape targets |
1m |
scrape_timeout |
Specifies how long to wait until a scrape request times out |
10s |
Password for grafana connection |
Password of a Grafana user to connect to Prometheus |
— |
Prometheus users to login/logout to Prometheus |
User credentials for logging into the Prometheus web interface |
— |
Service parameters |
Prometheus parameters |
— |
| Parameter | Description | Default value |
|---|---|---|
Grafana administrator’s password |
Password of a Grafana administrator user |
— |
Grafana listen port |
Port to access the Grafana web interface |
11210 |
| Parameter | Description | Default value |
|---|---|---|
Listen port |
Port to listen for a host’s system metrics in the Prometheus format |
11203 |
Metrics endpoint |
Endpoint to retrieve system metrics |
/metrics |
| Parameter | Description | Default value |
|---|---|---|
[Prometheus] → Enable SSL |
Enables SSL encryption of incoming traffic for the Prometheus Server component |
Disabled |
[Prometheus] → Certificate file |
Path to the server SSL certificate file for the Prometheus Server component |
/etc/admprom/prometheus/server.crt |
[Prometheus] → Private key file |
Path to the file with the private key of the server SSL certificate for the Prometheus Server component |
/etc/admprom/prometheus/server.key |
[Prometheus] → Certificate authority file |
Path to the file with the CA certificate to verify Prometheus targets |
/etc/admprom/prometheus/ca.crt |
[Grafana] → Enable SSL |
Enables SSL encryption of incoming traffic for the Grafana component |
Disabled |
[Grafana] → Certificate file |
Path to the server SSL certificate file for the Grafana component |
/etc/admprom/grafana/server.crt |
[Grafana] → Private key file |
Path to the file with the private key of the server SSL certificate for the Grafana component |
/etc/admprom/grafana/server.key |
[Grafana] → Certificate authority file |
Path to the file with the CA certificate to verify Prometheus certificate |
/etc/admprom/grafana/ca.crt |
[Node-exporter] → Enable SSL |
Enables SSL encryption of incoming traffic for the Node Exporter component |
Disabled |
[Node-exporter] → Certificate file |
Path to the server SSL certificate file for the Node Exporter component |
/etc/ssl/server.crt |
[Node-exporter] → Private key file |
Path to the file with the private key of the server SSL certificate for the Node Exporter component |
/etc/ssl/server.key |